An Alarm Correlation Algorithm for Network Management Based on Root Cause Analysis
|
|
|
- Rolf McKenzie
- 5 years ago
- Views:
Transcription
1 An Alarm Correlation Algorithm for Network Management Based on Root Cause Analysis Dae Sun Kim*, Hiroyuki Shinbo*, Hidetoshi Yokota* *KDDI R&D Laboratories, Inc. Fujimino, Saitama, Japan Abstract The alarm correlation is an essential function of network management systems to provide detection, isolation and correlation of unusual operational behaviour of telecommunication network. However, existing alarm correlation approaches still rely on the manual processing, and depend on the knowledge of the network operators. Since, the telecommunication network produces a number of alarms which are so called the alarm floods, it could be very difficult for the network operators to detect the root cause problems in a short period of time. Therefore, we propose the alarm correlation algorithm which is able to isolate and correlate the root causes in a very short time. In addition, we show that the proposed algorithm performs well in terms of efficiency of analyzing alarms and accuracy of identifying root cause. Keywords Network Management, Alarm Floods, Alarm Correlation, Root Cause Analysis 1. INTRODUCTION Considering the growing complexity of Today's networks, the operational efficiency and accuracy are required to handle the telecommunication network for network management systems. A network produces daily a number of data such as performance indicators and alarms. In particular, the area of fault management remains a key problem which is difficult to identify and predict the root cause problems in a short period of time for network operators. A root cause alarm[1][2] is the initiating cause problem which leads to an effect of other alarms. The incoming rate of network alarms often becomes too high for a network operator so that, the operator may not have enough time to recognize the network state without alarm correlation. The purpose of alarm correlation is to reduce a number of alarms and identify the root cause alarm from the number of alarms. A number of approaches[3][4] have been proposed for alarm correlation. Current alarm correlation approaches can be categorized as: Rule-Based approach[5][6], Codebook-Based approach[5][7], Case-Based approach[4][8], and Mining-Based approach[9][10][11]. The Rule-Based and Codebook based approaches have a drawback since the rule sets[6] and codebook[7] are specified based on experiences of the operators. Therefore, an excessive amount of expert knowledge is typically needed to specify the rule sets and the codebook. In the Case-based approach, if there is no matching case[8] for the current problem, it is unable to provide the solution for this problem in a short period time. Thus, it is difficult for the operators to make new cases that are not yet known. In the Mining-Based approach, many of the proposed algorithms[9][10][11] are not suitable to analyze the frequent event sets[11] in a short period time because of their long processing time. According to our investigations, most of the alarm correlation approaches still rely on the manual processing, and depend on the knowledge of the network operators which is a time consuming process. To address the above problems, an alarm correlation technique should diagnose the given problems in a very short time without expert knowledge. Moreover, the alarm correlation technique is expected to be lightweight and performed on any layered network architecture. Therefore, we propose a novel alarm correlation algorithm to identify the root cause alarm based on the TCP/IP model[12] so that, it can run at any types of environment, and topology on the Internet. In our approach, all alarms are classified according to an identifier of each TCP/IP protocol layer (e.g. Port number in TCP and UDP, IP address, Protocol type and so on)[12] and then clustered in order to indentify the root cause alarm according to the cause and effect relationship[13] between alarms without expert knowledge. The cause and effect relationship is that when alarm A happens, another alarm, alarm B is more likely to happen. The main idea of the proposed algorithm is that the fault occurring at each layer can be classified by the identifier, and the identifier is a key information to find the cause and effect relationship between the upper and lower TCP/IP layers. In general, the lower layer problems affect the higher layer problems as well as the neighbor nodes. In other words, the lower layer alarms appear as the root cause alarms more frequently than the higher layer alarms. Our paper is organized as follows. In Section 2, we briefly introduce the current alarm correlation approaches. Detailed descriptions of the proposed alarm correlation algorithm are presented in Section 3. Then we show the experimental results in Section 4. Finally, we conclude in Section RELATED WORKS In this section, we discuss four such alarm correlation approaches: Rule-Based Alarm Correlation, Codebook-Based Alarm Correlation, Case-Based Alarm Correlation and Mining-Based Alarm Correlation. ISBN Feb. 13~16, 2011 ICACT2011
2 2.1 Rule-Based Alarm Correlation The rule-based approach has been frequently used for alarm correlation. In this approach, the network operator identifies all of the events such as alarm, alert, error, threshold violation, and so on. After that, the network operator analyses the root causes and the symptoms[2] of the each root causes. Finally, the specific rule is created to process each of these events. However, the rule-based approach has a drawback since the rule set is specified based on human experiences. Therefore, an excessive amount of expert knowledge is typically needed to specify the rule sets. 2.2 Codebook based Alarm Correlation The Codebook-Based approach is based on a representation of relationships between problems and symptoms as a matrix[5][7]. In this approach, the matrix is represented by the causality graph[5] so that there are only direct cause and effect relationships between problems and symptoms in the causality graph. The symptoms which are caused by a problem are represented by a code that identifies the problem. The code[5] is a sequence of values from 0 to 1. The appearance of a particular symptom is denoted by 1, and 0 means the symptom has not been observed. Therefore, the number of problems can be detected by the codebook. Since the codebook correlation is performed only once to detect a root cause problem, it is very efficient to detect the problems of network in terms of speed and accuracy. However, the expert knowledge is required to construct the codebook. Furthermore, a change in the network requires regenerating the codebook which is a time consuming process. 2.3 Case based Alarm Correlation The case-based approach is a method to solve problems using the experience of the past cases. In this approach, problems are solved by the stored solutions. When a problem is solved, this solution is stored to be use in the future. However, if there is no matching case for the current problem, this approach is unable to provide the solution for this problem. Furthermore, it is impossible to make new cases that are not yet known in a short period time. Therefore, it also needs the expert knowledge to build the solution database[8], which is a time consuming process. 2.4 Mining based Alarm Correlation In this approach, frequent event sets can be detected by several mining algorithms[9][10][11]. It is very useful to detect the frequent event sets, and identify a root cause alarm among the collected alarms. However, many of the proposed algorithms are not suitable to analyse the frequent event sets in a short period time because of their long processing time. 3. PROPOSED ALARM CORRELATION SCHEME This section describes the proposed alarm correlation algorithm and illustrates it in detail with some cases. 3.1 Background Knowledge Representation The Internet is a global system of interconnected networks that use the TCP/IP protocol suite[12]. Moreover, most of the telecommunication networks existing today are a part of the Internet. Therefore, our alarm correlation approach focuses on the cause and effect relationship between each layer of TCP/IP model to determine how a problem of network happened and to understand why it happened. In a layered network architecture, the services are grouped in a hierarchy of layers. An entity of layer N uses only services of layer N-1 and it provides services only to layer N+1 as shown in Figure 1. When talking about two adjacent layers within a node, the higher layer is a service user and the lower layer is a service provider. As a result, a relationship between adjacent layers can be defined as follows: Definition 1. For any given two layers N and N-1 within a node, N is a higher layer than N-1. Therefore, if N-1 layer is not able to provide any service, N layer cannot provide any service to N+1 layer. In other words, the lower layer problems always affect the higher layer problems. In addition, each layer provides a protocol to communicate with its peer. Thus, N layer must be able to receive data from the peer N layer. Therefore, a relationship between identical peer layers can be defined as follows: Definition 2. For any given two identical layers N and peer N between communicating nodes, if N layer is not able to provide any service, peer N layer cannot provide any service data unit which is generated by N layer to peer N+1 layer. In other words, any layer problems always affect the its peer layer problems. Figure 1. Layered architecture of TCP/IP reference model The highest layer cannot be a service provider within a node but it can be the service provider for the highest layer of peer nodes. As a result, it can be defined as follows: Definition 3. Highest layer problems within a node are either generated by itself or by lower layer problems. In the former case, the highest layer is not affected by the lower layer problems but the highest layer of peer node can be affected by it. 3.2 Root cause analysis A root cause is the initial cause of other alarms and it should be identified and removed from the network. Otherwise, a number of alarms may be generated continuously. Table 1 ISBN Feb. 13~16, 2011 ICACT2011
3 shows a sample of alarm data set. ("Non-priv" denotes the set {1024,...,65535} of non-privileged ports.) Table 1. A sample of alarm data set Seq. Src-IP Src-Port Dst-IP Dst- Port Description 1 IP Port Down 2 IP Port Down 3 IP3 Non-Priv IP1 80 HTTP is unavailable 4 IP4 Non-Priv IP1 80 HTTP is unavailable 5 IP4 Non-Priv IP2 53 DNS is not reachable 6 IP IP1 Down 7 IP HTTP Down 8 IP DNS Down As the Table 1 shows, IP1 and IP2 are the HTTP server and the DNS server respectively. In addition, IP3 is the client of IP1 and IP4 is the client of both IP1 and IP2 since IP3 and IP4 alarms are targeted at IP1 and IP2. In our alarm correlation approach, at first, all alarms are grouped according to source IP address and then sorted by each layer which range from application layer to the physical layer as shown in Figure 2. To sort by each layer, our algorithm needs to know which alarm belongs to which layer. For instance, since HTTP and DNS in Table 1 belong to application layer, those alarms are grouped into application layer alarm. In this manner, other alarms in Table 1 are grouped into their corresponding layers. The grouping of alarms makes it easier to manage a large number of alarms generated for the identical network problem. According to our definition 1 in Section 3.1, the lower layer problems affect the higher layer problems. Therefore, "IP1 Down", "Port Down", "HTTP Unavailable" and "DNS Unreachable" which are the lowest layer alarms in this example can be the root causes of each group in Figure 2. Figure 2. Alarm Grouping Considering our definition 2, if an alarm is targeted at other alarm, they are merged into a group which we call the cluster[1]. Therefore, two "HTTP Unavailable" alarms in Group 3 and Group 4 are merged into Cluster 1. In addition, "DNS Unreachable" alarm is merged into Cluster 2 as shown in Figure 3 since the alarms in Group 3 and Group 4 are targeted at Group 1 and Group 2 respectively. The clustering of alarms also makes it easier to manage a huge number of alarms generated for problems in related areas. Finally, "IP1 Down" and "Port Down" are identified as the root causes of Cluster 1 and Cluster 2 respectively in Figure 3. In addition, two "HTTP Unavailable" alarms in Table 1 should be generalized to reduce multiple occurrences of identical alarms into a single alarm. And to conclude, a combination of grouping, clustering and generalizing is a key idea to determine the root cause of one or more alarms in this paper. Figure 3. Alarm Clustering 3.3 Alarm correlation algorithm The alarm correlation is not an easy task because the telecommunication networks usually generate a huge number of alarms every day. An interesting observation is that the most of alarms are noisy alarms which reduce the efficiency of analysing alarms and the accuracy of identifying the root cause. Thus, the alarm generalization process is required to reduce an amount of noisy alarms. To achieve this, Figure 4 shows the pseudo-code of the proposed alarm grouping algorithm which is the first step of alarm correlation. Figure 4. Alarm grouping algorithm The main idea of the alarm grouping algorithm is to group alarms according to identical source IP address(line 1). By doing so, the identical alarms can be detected at each group and it makes it easier to understand what happened at each node. After that, all alarms in each group are sorted in order by layer which range from application layer to the physical layer (Line 4). In addition, many identical alarms are removed in each group (Lines 5 and Line 6). Figure 5 shows an example of generalization process for the identical alarms. The difference between Alarm 1 and Alarm 2 in Figure 5 is only the time stamp value. Therefore, those alarms can be generalized as a single alarm in order to reduce a huge number of alarms. ISBN Feb. 13~16, 2011 ICACT2011
4 Figure 5. An example of generalization process for identical alarms Finally, line 10 will output a set G of groups which include the generalized alarms. Figure 6. Alarm clustering algorithm The main purpose of the alarm clustering algorithm is to find a cause and effect relationship between alarms. For example, "IP2 Port down" causes "DNS down" in Figure 3. Furthermore, "DNS down" causes "DNS unreachable". Thus, in this example, "IP2 Port down" has a cause and effect relationship with "DNS down". Also, "DNS down" has a cause and effect relationship with "DNS unreachable". Therefore, all alarms which have an identical cause and effect relationship in this example can be merged into a single cluster. To achieve this, Figure 6 shows the pseudo-code of the alarm clustering algorithm which is the second step of alarm correlation. In line 1 to 7, the algorithm counts total number of groups and alarms of each group to initialize the Cluster Key IDs which are used to cluster the alarms according to identical CK_ID as shown in Figure 7. Figure 7. An example of alarm clustering In Figure 7, at first, the CK_ID of "HTTP Unavailable" alarm is initialized to 3 in the phase 1 (Line 1 to 7 in Figure 6) and then it is set to 1 in the phase 2 since "HTTP Down" has a cause and effect relation with "HTTP Unavailable" (Line 8 to 17 in Figure 6). In the phase 3, all alarms are merged into a single cluster (Line 18 in Figure 6). In line 20 to 26, all alarms in each cluster are sorted in order by layer which range from application layer to the physical layer (Line 21). In addition, many similar alarms are removed in each cluster (lines 22 and 23). Figure 8 shows generalization process for the similar alarms. Figure 8. An example of generalization process for similar alarms The differences between Alarm 1 and Alarm2 in Figure 8 are the source IP address, the source port number and the time stamp value. Therefore, those alarms can be generalized as a single alarm in order to reduce a huge number of alarms. Finally, line 27 will output a set C of clusters which include the root cause alarms. The final step of alarm correlation is to identify the root cause alarms in each cluster. For instance, Figure 9 shows an example of output cluster after the alarm clustering algorithm processes the alarms in Table 1. It is very clear that "IP1 Down" and "Port 53 Down" are the root cause of Cluster 1 and 2 respectively. However, there is a possibility that multiple alarms can be appeared in the lowest layer of each cluster. In that case, since an alarm type can be divided into a critical alarm and a warning alarm generally, the critical alarm has a higher priority than the warning alarm. Therefore, any critical alarms can be the root cause alarms rather than the warning alarms. Figure 9. An example of output clusters in alarm correlation ISBN Feb. 13~16, 2011 ICACT2011
5 By analysing a set of clusters, how a problem of network and why it happened can be realized. Moreover, it will be useful data to prevent the problems which will be happened in the near future. 4. EXPERIMENT AND EVALUATION In this section, we describe the experiment and evaluation of our alarm correlation algorithm to confirm its efficiency of analyzing alarms and accuracy of identifying root cause alarm. The alarm correlation algorithm is coded in C++ language and performed on Linux machine. In addition, we used synthetic alarm datasets as shown in the Table 1 for the input data of the alarm correlation algorithm. Figure 10 shows the topology of twenty-two nodes with five critical alarms such as "Link Down", "IP Down" and so on. We assume that the critical alarms occur at five black nodes in Figure 10 at the same time and all node N are connected to all servers. For instance, N2 is connected to all servers. Thus, N2 generates several alarms such as "WS1 HTTP Unavailable" and "FS2 FTP Unavailable". Also, R2 generates "R3 Neighbor Loss" alarm and "R0 Neighbor Loss" alarm simultaneously. Number Of Alarms N1 N2 N3 N7 N8 N9 R0 R1 R2 R3 R4 WS1 FS2 Application Layer Transportation Layer Network Layer Link Layer 1 1 Figure 12. Output of grouping algorithm Figure 12 shows the output of grouping algorithm. The number of original alarms is reduced from 100 alarms to 26 alarms since a number of identical alarms are generalized as a single alarm. For instance, since N3 is connected to both WS1 and FS2, it can generate the two types of alarm such as "WS 1 HTTP Unavailable" and "FS2 FTP Unavailable". In our experiment, N3 generates six "WS1 HTTP Unavailable" alarms and six " FS2 FTP Unavailable" alarms and then, the grouping algorithm generalizes the two types of identical alarms as a single alarm respectively Number of Alarms Figure 10. Topology of our experimental network In this manner, we generate a hundred alarms randomly as shown in Figure 11. Number of Alarms N1 N2 N3 N7 N8 N9 R0 R1 R2 R3 R4 WS1 FS2 Application Layer Transportation Layer Network Layer Link Layer 2 2 Figure 11. Synthetic alarm datasets of each node Since, R3 link is down, there is no way to get the alarms from N4 to N6. Thus, those alarms are not included in the alarm datasets. 0 Cluster 1 Cluster 2 Cluster 3 Cluster 4 Cluster 5 Application Layer 2 2 Transportation Layer Network Layer Link Layer 1 1 Figure 13. Output of clustering algorithm Figure 13 shows the output of clustering algorithm. The number of alarms after the grouping algorithm processes the alarms is reduced from 26 alarms to 15 alarms since a number of similar alarms are generalized as a single alarm. For instance, since R3 generates "Link Down" alarm, it is the initial cause of "R3 IP Down" alarm which is detected at R3 and "R3 Neighbor Loss" alarms which are generated by R2 and R4 respectively. Thus, those alarms have an identical cause and effect relationship so that they are merged into a single cluster. After that, "R3 Neighbor Loss" alarms are generalized as a single alarm by the clustering algorithm since they are similar alarms. Finally, our algorithm can identify a root cause alarm in each cluster as shown in Figure 14. ISBN Feb. 13~16, 2011 ICACT2011
6 Figure 14. A root cause alarm of each clusters The lowest alarms in each cluster such as "N1 IP Down" alarm, "R3 Link Down" alarm and so on in Figure 14 are identified as the root cause alarm. As a result, the number of original alarms is reduced from 100 alarms to 5 alarms. [6] Wu Jian and Li Xing ming, "A Novel Algorithm for Dynamic Mining of Association Rules," International Workshop on Knowledge Discovery and Data Mining, jan 2008 PP [7] Qiuhua Zheng and Yuntao Qian1, "An Event Correlation Approach Based on the Combination of IHU and Codebook," Lecture Notes in Computer Science, 2005, Vol.3802, pp [8] L. Lewis, Managing Computer Networks - A Case-Based Reasoning Approach. Artech House, Inc., [9] Jukic O. and Kunstic M., "Logical Inventory Database Integration into Network Problems Frequency Detection Process," ConTEL 2009, June 2009, pp [10] Risto Vaarandi, "A Data Clustering Algorithm for Mining Patterns from Event Logs," IP Operations and Management(IPOM 2003), Octerber 2003, pp [11] Risto, Vaarandi, "Tools and Techniques for Event Log Analysis," PhD thesis, Tallinn University of Technology, Department of Computer Engineering, Estonia, June [12] Forouzan, Behrouz A, TCP/IP Protocol Suite (2th ed.). McGraw-Hill, [13] A. Devitt, J. Duffin, and R. Moloney, Topographical proximity for mining network alarm data, in ACM SIGCOMM workshop on Mining network data, Philadelphia, Pennsylvania, USA, Aug ACKNOWLEDGMENT This research was supported by the Ministry of Internal Affairs and Communications in Japan: High Reliability Cloud Networking. 5. CONCLUSIONS This paper proposed an alarm correlation algorithm leveraging TCP/IP model and focusing on root cause analysis without relying on expert knowledge to detect the root cause alarm. According to the cause and effect relationship, the alarms are merged into a cluster and then the root cause alarms are figured out exactly. In addition, a number of identical and similar alarms are reduced dramatically by alarm generalization. The results of experiment prove that this algorithm can analyse alarms efficiently and indentify the root cause alarm accurately. REFERENCES [1] AL-MAMORY Safaa O., HONGLI ZHANG, "Intrusion Detection Alarms Reduction Using Root Cause Analysis and Clustering," Journal of Computer Communications, February 2009, vol.32, no2, pp [2] Banerjee D., Madduri V.R., Srivatsa M., "A Framework for Distributed Monitoring and Root Cause Analysis for Large IP Networks," 28th IEEE International Symposium on Reliable Distributed Systems, September 2009, pp [3] Hanemann, A.and Marcu, P., "Algorithm design and application of service-oriented event correlation," 3rd IEEE/IFIP, April 2008, pp [4] M. Steinder and A. S. Sethi, "A Survey of Fault Localization Techniques in Computer Networks," Science of Computer Programming, Special Edition on Topics in System Administration, Vol. 53, November 2004, pp [5] White Paper, "Automating Root-Cause Analysis: EMC Ionix Codebook Correlation Technology vs. Rules-based Analysis," Nomber, ISBN Feb. 13~16, 2011 ICACT2011
Autonomic Fault Management based on Cognitive Control Loops
 Autonomic Fault Management based on Cognitive Control Loops 1 Sung-Su Kim, 1 Sin-seok Seo, 2 Joon-Myung Kang, and 1,3 James Won-Ki Hong 1 Dept. of Computer Science and Engineering, POSTECH, {kiss, sesise,
Autonomic Fault Management based on Cognitive Control Loops 1 Sung-Su Kim, 1 Sin-seok Seo, 2 Joon-Myung Kang, and 1,3 James Won-Ki Hong 1 Dept. of Computer Science and Engineering, POSTECH, {kiss, sesise,
Intrusion Detection: Eliminating False Alarms
 Intrusion Detection: Eliminating False Alarms MAFTIA Final Review Andreas Wespi 18/19 February 2003 Newcastle Overview! MAFTIA and Intrusion Detection! Eliminating False Alarms! Demonstrator of an Intrusion-Tolerant
Intrusion Detection: Eliminating False Alarms MAFTIA Final Review Andreas Wespi 18/19 February 2003 Newcastle Overview! MAFTIA and Intrusion Detection! Eliminating False Alarms! Demonstrator of an Intrusion-Tolerant
To appear in the IEEE/IFIP 1996 Network Operations and Management. Symposium (NOMS'96), Kyoto, Japan, April TASA: Telecommunication
 To appear in the IEEE/IFIP 1996 Operations and Management Symposium (NOMS'96), Kyoto, Japan, April 1996. TASA: Telecommunication Alarm Sequence Analyzer or How to enjoy faults in your network Kimmo Hatonen,
To appear in the IEEE/IFIP 1996 Operations and Management Symposium (NOMS'96), Kyoto, Japan, April 1996. TASA: Telecommunication Alarm Sequence Analyzer or How to enjoy faults in your network Kimmo Hatonen,
Intrusion Detection System: Facts, Challenges and Futures. By Gina Tjhai 13 th March 2007 Network Research Group
 Intrusion Detection System: Facts, Challenges and Futures By Gina Tjhai 13 th March 2007 Network Research Group 1 Overview Introduction Challenges of current IDS Potential solutions Alarm Correlation Existing
Intrusion Detection System: Facts, Challenges and Futures By Gina Tjhai 13 th March 2007 Network Research Group 1 Overview Introduction Challenges of current IDS Potential solutions Alarm Correlation Existing
Alarm Analysis with Fuzzy Logic and Multilevel Flow Models
 Alarm Analysis with Fuzzy Logic and Multilevel Flow Models Fredrik Dahlstrand Department of Information Technology Lund Institute of Technology Box 118, SE-221 00 Lund, Sweden Phone: +46 46 222 95 10 Fax
Alarm Analysis with Fuzzy Logic and Multilevel Flow Models Fredrik Dahlstrand Department of Information Technology Lund Institute of Technology Box 118, SE-221 00 Lund, Sweden Phone: +46 46 222 95 10 Fax
Conference Paper Decision Support System for Alarm Correlation in GSM Networks Based on Artificial Neural Networks
 Hindawi Publishing Corporation Conference Papers in Engineering Volume 213, Article ID 958926, 7 pages http://dx.doi.org/1.1155/213/958926 Conference Paper Decision Support System for Alarm Correlation
Hindawi Publishing Corporation Conference Papers in Engineering Volume 213, Article ID 958926, 7 pages http://dx.doi.org/1.1155/213/958926 Conference Paper Decision Support System for Alarm Correlation
Video Smoke Detection using Deep Domain Adaptation Enhanced with Synthetic Smoke Images
 Video Smoke Detection using Deep Domain Adaptation Enhanced with Synthetic Smoke Images Gao Xu, Qixing Zhang, Gaohua Lin, Jinjun Wang, Yongming Zhang State Key Laboratory of Fire Science, University of
Video Smoke Detection using Deep Domain Adaptation Enhanced with Synthetic Smoke Images Gao Xu, Qixing Zhang, Gaohua Lin, Jinjun Wang, Yongming Zhang State Key Laboratory of Fire Science, University of
Monitor Alarms and Events
 What Are Alarms and Events?, page 1 How are Alarms and Events Created and Updated?, page 2 Which Events Are Supported?, page 5 Set Alarm and Event Management Preferences, page 5 Interpret Event and Alarm
What Are Alarms and Events?, page 1 How are Alarms and Events Created and Updated?, page 2 Which Events Are Supported?, page 5 Set Alarm and Event Management Preferences, page 5 Interpret Event and Alarm
Room Temperature Control and Fire Alarm/Suppression IoT Service Using MQTT on AWS
 Room Control and Fire Alarm/Suppression IoT Service Using MQTT on AWS Do-Hun Kang, Min-Sung Park, Hyoung-Sub Kim, Da-young Kim, Sang-Hui Kim, Hyeon-Ju Son, * Sang-Gon Lee Dong-Seo University, Korea, {kadihi@naver.com,
Room Control and Fire Alarm/Suppression IoT Service Using MQTT on AWS Do-Hun Kang, Min-Sung Park, Hyoung-Sub Kim, Da-young Kim, Sang-Hui Kim, Hyeon-Ju Son, * Sang-Gon Lee Dong-Seo University, Korea, {kadihi@naver.com,
Oracle Real Application Clusters (RAC) 12c Release 2 What s Next?
 Oracle Real Application Clusters (RAC) 12c Release 2 What s Next? Markus Michalewicz Oracle Redwood Shores, CA, USA Keywords: RAC, Cloud, Private Cloud, Storage, Network, Development, Market Trends, Future
Oracle Real Application Clusters (RAC) 12c Release 2 What s Next? Markus Michalewicz Oracle Redwood Shores, CA, USA Keywords: RAC, Cloud, Private Cloud, Storage, Network, Development, Market Trends, Future
Applied Data Science: Using Machine Learning for Alarm Verification
 Applied Data Science: Using Machine Learning for Alarm Verification by Jan Stampfli and Kurt Stockinger Zurich University of Applied Sciences, Switzerland Introduction False alarms triggered by sensors
Applied Data Science: Using Machine Learning for Alarm Verification by Jan Stampfli and Kurt Stockinger Zurich University of Applied Sciences, Switzerland Introduction False alarms triggered by sensors
Procedia - Social and Behavioral Sciences 195 ( 2015 ) World Conference on Technology, Innovation and Entrepreneurship
 Available online at www.sciencedirect.com ScienceDirect Procedia - Social and Behavioral Sciences 195 ( 2015 ) 1846 1850 World Conference on Technology, Innovation and Entrepreneurship Fire Detection Systems
Available online at www.sciencedirect.com ScienceDirect Procedia - Social and Behavioral Sciences 195 ( 2015 ) 1846 1850 World Conference on Technology, Innovation and Entrepreneurship Fire Detection Systems
Monitor Alarms and Events
 This chapter contains the following topics: What Are Alarms and Events?, page 1 How are Alarms and Events Created and Updated?, page 2 Find and View Alarms, page 3 Set Alarm and Event Management Preferences,
This chapter contains the following topics: What Are Alarms and Events?, page 1 How are Alarms and Events Created and Updated?, page 2 Find and View Alarms, page 3 Set Alarm and Event Management Preferences,
Artificial Intelligence Enables a Network Revolution
 *ITU FL-ML5G Artificial Intelligence Enables a Network Revolution April 25, 2018 Network Technology Research Institute, China Unicom Artificial Intelligence Enables a Network Revolution A Part 1 AI application
*ITU FL-ML5G Artificial Intelligence Enables a Network Revolution April 25, 2018 Network Technology Research Institute, China Unicom Artificial Intelligence Enables a Network Revolution A Part 1 AI application
Detection of Temporal Dependencies in Alarm Time Series of Industrial Plants
 Preprints of the 19th World Congress The International Federation of Automatic Control Detection of Temporal Dependencies in Alarm Time Series of Industrial Plants Jens Folmer, Falk Schuricht and Birgit
Preprints of the 19th World Congress The International Federation of Automatic Control Detection of Temporal Dependencies in Alarm Time Series of Industrial Plants Jens Folmer, Falk Schuricht and Birgit
A Smart House in the Context of Internet of Things
 A Smart House in the Context of Internet of Things MARIUS RISTEIU *, REMUS DOBRA *, MONICA LEBA *, ANDREEA IONICA ** * Department of Computer and Electrical Engineering ** Department of Management University
A Smart House in the Context of Internet of Things MARIUS RISTEIU *, REMUS DOBRA *, MONICA LEBA *, ANDREEA IONICA ** * Department of Computer and Electrical Engineering ** Department of Management University
Research on Decision Tree Application in Data of Fire Alarm Receipt and Disposal
 Research Journal of Applied Sciences, Engineering and Technology 5(22): 5217-5222, 2013 ISSN: 2040-7459; e-issn: 2040-7467 Maxwell Scientific Organization, 2013 Submitted: October 09, 2012 Accepted: December
Research Journal of Applied Sciences, Engineering and Technology 5(22): 5217-5222, 2013 ISSN: 2040-7459; e-issn: 2040-7467 Maxwell Scientific Organization, 2013 Submitted: October 09, 2012 Accepted: December
Alarms and Events. Defining Alarm Conditions. Database-Generated Alarms
 9 Defining Alarm Conditions Database-Generated Alarms The LookoutDirect alarm service keeps track of error messages and any process elements you have defined alarm conditions for. You can define alarm
9 Defining Alarm Conditions Database-Generated Alarms The LookoutDirect alarm service keeps track of error messages and any process elements you have defined alarm conditions for. You can define alarm
STUDY ON THE CONTROL ALGORITHM OF THE HEAT PUMP SYSTEM FOR LOAD CHANGE
 Numbers of Abstract/Session (given by NOC) - 1 - STUDY ON THE CONTROL ALGORITHM OF THE HEAT PUMP SYSTEM FOR LOAD CHANGE Seok Ho Yoon, Kong Hoon Lee, Chan Ho Song, and Ook Joong Kim Environment and Energy
Numbers of Abstract/Session (given by NOC) - 1 - STUDY ON THE CONTROL ALGORITHM OF THE HEAT PUMP SYSTEM FOR LOAD CHANGE Seok Ho Yoon, Kong Hoon Lee, Chan Ho Song, and Ook Joong Kim Environment and Energy
EnergyMaster. ENEC Monitoring System. An on-site supervision and remote monitoring solution
 EnergyMaster ENEC Monitoring System An on-site supervision and remote monitoring solution ENERGYMASTER ENEC MONITORING SYSTEMS AN ON-SITE SUPERVISION AND REMOTE MONITORING SOLUTION Take Control of Your
EnergyMaster ENEC Monitoring System An on-site supervision and remote monitoring solution ENERGYMASTER ENEC MONITORING SYSTEMS AN ON-SITE SUPERVISION AND REMOTE MONITORING SOLUTION Take Control of Your
SCALE MODEL STUDIES ON SMOKE MOVEMENT IN INCLINED TUNNEL WITH LONGITUDINAL VENTILATION AND SMOKE BARRIERS
 , Volume 11, Number 2, p.21-26, 212 SCALE MODEL STUDIES ON SMOKE MOVEMENT IN INCLINED TUNNEL WITH LONGITUDINAL VENTILATION AND SMOKE BARRIERS C.Y. Tso and W.K. Chow Research Centre for Fire Engineering,
, Volume 11, Number 2, p.21-26, 212 SCALE MODEL STUDIES ON SMOKE MOVEMENT IN INCLINED TUNNEL WITH LONGITUDINAL VENTILATION AND SMOKE BARRIERS C.Y. Tso and W.K. Chow Research Centre for Fire Engineering,
Enterprise Service Bus
 Enterprise Service Bus Suva Uses WSO2 ESB to Manage 100-Plus Web Services Internally and Across Customers, Government Agencies, and Other Third Parties As Switzerland s leading provider of federal insurance
Enterprise Service Bus Suva Uses WSO2 ESB to Manage 100-Plus Web Services Internally and Across Customers, Government Agencies, and Other Third Parties As Switzerland s leading provider of federal insurance
Using Neural Networks for Alarm Correlation in Cellular Phone Networks
 Using Neural Networks for Alarm Correlation in Cellular Phone Networks Hermann Wietgrefe, Klaus-Dieter Tuchs, Klaus Jobmann, Guido Carls, Peter Fröhlich*, Wolfgang Nejdl*, Sebastian Steinfeld* Institut
Using Neural Networks for Alarm Correlation in Cellular Phone Networks Hermann Wietgrefe, Klaus-Dieter Tuchs, Klaus Jobmann, Guido Carls, Peter Fröhlich*, Wolfgang Nejdl*, Sebastian Steinfeld* Institut
CV-350 TCP/IP Access Control System. System Overview
 CV-350 TCP/IP Access Control System System Overview July 2015 Open Product Access Camden delivers the power of advanced IP access control differently than our competitors! - All product sales exclusively
CV-350 TCP/IP Access Control System System Overview July 2015 Open Product Access Camden delivers the power of advanced IP access control differently than our competitors! - All product sales exclusively
RESEARCH ON THE MAIN CRITERIA OF DECISION-MAKING FACTORS THAT AFFECT CONSUMERS' PURCHASE OF RESIDENTIAL FIRE ALARMS
 www.arpapress.com/volumes/vol35issue1/ijrras_35_1_03.pdf RESEARCH ON THE MAIN CRITERIA OF DECISION-MAKING FACTORS THAT AFFECT CONSUMERS' PURCHASE OF RESIDENTIAL FIRE ALARMS Chih-Yao Lo 1,Hung-Teng Chang
www.arpapress.com/volumes/vol35issue1/ijrras_35_1_03.pdf RESEARCH ON THE MAIN CRITERIA OF DECISION-MAKING FACTORS THAT AFFECT CONSUMERS' PURCHASE OF RESIDENTIAL FIRE ALARMS Chih-Yao Lo 1,Hung-Teng Chang
Design of Multi-Sensors Cooperation Control System for Intelligent Building
 Energy and Power Engineering, 2017, 9, 495-502 http://www.scirp.org/journal/epe ISSN Online: 1947-3818 ISSN Print: 1949-243X Design of Multi-Sensors Cooperation Control System for Intelligent Building
Energy and Power Engineering, 2017, 9, 495-502 http://www.scirp.org/journal/epe ISSN Online: 1947-3818 ISSN Print: 1949-243X Design of Multi-Sensors Cooperation Control System for Intelligent Building
Teaching Landscape Spatial Design with Grading Studies: An Experiment Based on High Fidelity DTM
 302 Full Paper Teaching Landscape Spatial Design with Grading Studies: An Experiment Based on High Fidelity DTM Pang Li 1 1 Landscape Architecture Department, School of Architecture, Southeast University/China
302 Full Paper Teaching Landscape Spatial Design with Grading Studies: An Experiment Based on High Fidelity DTM Pang Li 1 1 Landscape Architecture Department, School of Architecture, Southeast University/China
FIMD: Fine-grained Device-free Motion Detection
 ICPADS 2012 FIMD: Fine-grained Device-free Motion Detection Jiang Xiao, Kaishun Wu, Youwen Yi, Lu Wang, Lionel M. Ni Department of Computer Science and Engineering Hong Kong University of Science and Technology
ICPADS 2012 FIMD: Fine-grained Device-free Motion Detection Jiang Xiao, Kaishun Wu, Youwen Yi, Lu Wang, Lionel M. Ni Department of Computer Science and Engineering Hong Kong University of Science and Technology
Applications of Smart Home system for disabled people for using wireless network
 IOSR Journal of Electrical and Electronics Engineering (IOSR-JEEE) e-issn: 2278-1676, p-issn: 2320-3331, Volume 13, Issue 4, Ver. XX (Jul. Aug. 2018), PP XX-XX Applications of Smart Home system for disabled
IOSR Journal of Electrical and Electronics Engineering (IOSR-JEEE) e-issn: 2278-1676, p-issn: 2320-3331, Volume 13, Issue 4, Ver. XX (Jul. Aug. 2018), PP XX-XX Applications of Smart Home system for disabled
Alarm Correlation Research and Implementation Based on Similar Data Sources
 4th International Conference on Machinery, Materials and Information Technology Applications (ICMMITA 201) Alarm Correlation Research and Implementation Based on Similar Data Sources Yi Tang1, a and Dahai
4th International Conference on Machinery, Materials and Information Technology Applications (ICMMITA 201) Alarm Correlation Research and Implementation Based on Similar Data Sources Yi Tang1, a and Dahai
Design of the Fiber-optic Fence Warning System with Distributed Video Real-Time Display Function Qiang-yi YI and Zheng-hong YU *
 2016 International Conference on Artificial Intelligence: Techniques and Applications (AITA 2016) ISBN: 978-1-60595-389-2 Design of the Fiber-optic Fence Warning System with Distributed Video Real-Time
2016 International Conference on Artificial Intelligence: Techniques and Applications (AITA 2016) ISBN: 978-1-60595-389-2 Design of the Fiber-optic Fence Warning System with Distributed Video Real-Time
Soil Classification and Fertilizer Recommendation using WEKA
 Soil Classification and Fertilizer Recommendation using WEKA Suman 1, Bharat Bhushan Naib 2 1 Research Scholar, CSE, P.D.M. College of Engineering, Bahadurgarh, Haryana (India) sumansehrawat121@gmail.com
Soil Classification and Fertilizer Recommendation using WEKA Suman 1, Bharat Bhushan Naib 2 1 Research Scholar, CSE, P.D.M. College of Engineering, Bahadurgarh, Haryana (India) sumansehrawat121@gmail.com
Using ANM Mobile CHAPTER
 CHAPTER 19 Date: 3/22/13 This chapter describes Cisco ANM Mobile, which allows you to access your ANM server or ANM Virtual Appliance and manage your devices using a mobile device such as an iphone or
CHAPTER 19 Date: 3/22/13 This chapter describes Cisco ANM Mobile, which allows you to access your ANM server or ANM Virtual Appliance and manage your devices using a mobile device such as an iphone or
The Mode of Urban Renewal Base on the Smart City Theory under the Background of New Urbanization
 Frontiers of Engineering Management DOI 10.15302/J-FEM-2015035 ENGINEERING MANAGEMENT THEORIES AND METHODOLOGIES Yi-hua Mao, Hong-yu Li, Qin-rui Xu The Mode of Urban Renewal Base on the Smart City Theory
Frontiers of Engineering Management DOI 10.15302/J-FEM-2015035 ENGINEERING MANAGEMENT THEORIES AND METHODOLOGIES Yi-hua Mao, Hong-yu Li, Qin-rui Xu The Mode of Urban Renewal Base on the Smart City Theory
Performance Neuro-Fuzzy for Power System Fault Location
 International Journal of Engineering and Technology Volume 3 No. 4, April, 2013 Performance Neuro-Fuzzy for Power System Fault Location 1,2 Azriyenni, 1 M.W. Mustafa 1 Electrical Engineering, Fakulti Kejuruteraan
International Journal of Engineering and Technology Volume 3 No. 4, April, 2013 Performance Neuro-Fuzzy for Power System Fault Location 1,2 Azriyenni, 1 M.W. Mustafa 1 Electrical Engineering, Fakulti Kejuruteraan
Application of OPC in the Intelligent Building System Integration
 Application of OPC in the Intelligent Building System Integration Jie Chen Dongying Vocational College Dongying 257091, P.R.China Xiuli Sun The control system education of Jinan university Jinan 250022,
Application of OPC in the Intelligent Building System Integration Jie Chen Dongying Vocational College Dongying 257091, P.R.China Xiuli Sun The control system education of Jinan university Jinan 250022,
Comparative Study of Technological Trend between DAIKIN and Panasonic in the Field of Air Conditioner
 Comparative Study of Technological Trend between DAIKIN and Panasonic in the Field of Air Conditioner Nhivuong Pham, Yoshitoshi Tanaka Tokyo Institute of Technology, Management of Technology Dept., Tokyo,
Comparative Study of Technological Trend between DAIKIN and Panasonic in the Field of Air Conditioner Nhivuong Pham, Yoshitoshi Tanaka Tokyo Institute of Technology, Management of Technology Dept., Tokyo,
Experimental Implementation of Spectrum Sensing Using Cognitive Radio
 1 Experimental Implementation of Spectrum Sensing Using Cognitive Radio Prepared by: Kendall Schmalz Faculty Advisors: Dr. Yanxiao Zhao Assistant Professor, Electrical and Computer Engineering Dr. Thomas
1 Experimental Implementation of Spectrum Sensing Using Cognitive Radio Prepared by: Kendall Schmalz Faculty Advisors: Dr. Yanxiao Zhao Assistant Professor, Electrical and Computer Engineering Dr. Thomas
Service Oriented Architecture for Monitoring Cargo in Motion Along Trusted Corridors
 Service Oriented Architecture for Monitoring Cargo in Motion Along Trusted Corridors Martin Kuehnhausen Department of Electrical Engineering & Computer Science Master's Thesis Defense July 1, 2009 Committee
Service Oriented Architecture for Monitoring Cargo in Motion Along Trusted Corridors Martin Kuehnhausen Department of Electrical Engineering & Computer Science Master's Thesis Defense July 1, 2009 Committee
Intelligent alarm management
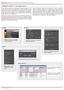 Intelligent alarm management icontrol Web s Advanced Alarm Management enables operators to work together to identify and resolve facility faults to minimize the MTTR. icontrol Web offers Advanced Alarm
Intelligent alarm management icontrol Web s Advanced Alarm Management enables operators to work together to identify and resolve facility faults to minimize the MTTR. icontrol Web offers Advanced Alarm
Chapter 1 Introduction
 Chapter 1 Introduction This chapter presents an introductory background to the research work undertaken, the problem statement, research issues involved and objectives of the research work. The contribution
Chapter 1 Introduction This chapter presents an introductory background to the research work undertaken, the problem statement, research issues involved and objectives of the research work. The contribution
Simulation study of evacuation in high-rise buildings
 Available online at www.sciencedirect.com ScienceDirect Transportation Research Procedia 00 (2014) 000 000 www.elsevier.com/locate/procedia The Conference in Pedestrian and Evacuation Dynamics 2014 (PED2014)
Available online at www.sciencedirect.com ScienceDirect Transportation Research Procedia 00 (2014) 000 000 www.elsevier.com/locate/procedia The Conference in Pedestrian and Evacuation Dynamics 2014 (PED2014)
Composite Event Detection in Wireless Sensor Networks
 Composite Event Detection in Wireless Sensor Networks Chinh T. Vu, Raheem A. Beyah and Yingshu Li Georgia State University 04-12-2007 Outline Why? Motivation What? Preliminaries How? Scheme Conclusion
Composite Event Detection in Wireless Sensor Networks Chinh T. Vu, Raheem A. Beyah and Yingshu Li Georgia State University 04-12-2007 Outline Why? Motivation What? Preliminaries How? Scheme Conclusion
Simple Equations for Predicting Smoke Filling Time in Fire Rooms with Irregular Ceilings
 Fire Science and Technorogy Vol.24 No.4(2005) 165-178 165 Simple Equations for Predicting Smoke Filling Time in Fire Rooms with Irregular Ceilings Jun-ichi Yamaguchi 1, Takeyoshi Tanaka 2 1 Technical Research
Fire Science and Technorogy Vol.24 No.4(2005) 165-178 165 Simple Equations for Predicting Smoke Filling Time in Fire Rooms with Irregular Ceilings Jun-ichi Yamaguchi 1, Takeyoshi Tanaka 2 1 Technical Research
Training Guide Series. CYMA User Portal Installation Guide
 Training Guide Series CYMA User Portal Installation Guide October 2018 CYMA Employee Self Service Installation Guide Contents SECTION 1: IMPORTANT NOTES AND SYSTEM REQUIREMENTS... 3 SECTION 2: NEW INSTALLATIONS...
Training Guide Series CYMA User Portal Installation Guide October 2018 CYMA Employee Self Service Installation Guide Contents SECTION 1: IMPORTANT NOTES AND SYSTEM REQUIREMENTS... 3 SECTION 2: NEW INSTALLATIONS...
Rosenberger Intergrated Operation and Maintenance Center for all repeaters(2g/3g/lte) following CMCC and TMN specification.
 Rosenberger Intergrated Operation and Maintenance Center for all repeaters(2g/3g/lte) following CMCC and TMN specification. Main Features The topology relationship of all repeater is shown by the domain
Rosenberger Intergrated Operation and Maintenance Center for all repeaters(2g/3g/lte) following CMCC and TMN specification. Main Features The topology relationship of all repeater is shown by the domain
Topic: Alarm Reduction and Correlation in IDS
 Electrical & Telecom Dependability & Security Partners: ENEA, LIU, QMUL, AIA EU-IST-2001-32685; Dec 2001 May 2004 Topic: Alarm Reduction and Correlation in IDS Authors: Tobias Chyssler, Kalle Burbeck (LIU)
Electrical & Telecom Dependability & Security Partners: ENEA, LIU, QMUL, AIA EU-IST-2001-32685; Dec 2001 May 2004 Topic: Alarm Reduction and Correlation in IDS Authors: Tobias Chyssler, Kalle Burbeck (LIU)
Effective Alarm Management for Dynamic and Vessel Control Systems
 DYNAMIC POSITIONING CONFERENCE October 12-13, 2010 OPERATIONS SESSION Effective Alarm Management for Dynamic and Vessel Control Systems By Steve Savoy Ensco Offshore Company 1. Introduction Marine control
DYNAMIC POSITIONING CONFERENCE October 12-13, 2010 OPERATIONS SESSION Effective Alarm Management for Dynamic and Vessel Control Systems By Steve Savoy Ensco Offshore Company 1. Introduction Marine control
NeXT is a powerful stand-alone application running fully embedded in network cameras to perform an intelligent video surveillance for ATM devices.
 NeXT is a powerful stand-alone application running fully embedded in network cameras to perform an intelligent video surveillance for ATM devices. It s no longer necessary installing workstation servers
NeXT is a powerful stand-alone application running fully embedded in network cameras to perform an intelligent video surveillance for ATM devices. It s no longer necessary installing workstation servers
Managing Network Alarms and Events
 9 CHAPTER Prime Performance Manager allows you to view alarms and events that occur in your network. The following topics provide information about displaying network alarms and events: Displaying Active
9 CHAPTER Prime Performance Manager allows you to view alarms and events that occur in your network. The following topics provide information about displaying network alarms and events: Displaying Active
Perimeter Product Overview. Effective protection for your business
 Perimeter Product Overview Effective protection for your business The Gallagher difference Our innovation is driven by the desire to solve problems, meet your needs and provide real business value. We
Perimeter Product Overview Effective protection for your business The Gallagher difference Our innovation is driven by the desire to solve problems, meet your needs and provide real business value. We
Patriot Systems Limited
 COPYRIGHT 1997 - The Patriot Systems Ltd. Patriot Alarm Monitoring Automation Package is licensed for use on one computer, by the original person, or company, or organization whose name is registered with
COPYRIGHT 1997 - The Patriot Systems Ltd. Patriot Alarm Monitoring Automation Package is licensed for use on one computer, by the original person, or company, or organization whose name is registered with
Product Brief for Alarm Analytics V9.2 April 2010
 Product Brief for Alarm Analytics V9.2 April 2010 Alarm Analytics V9.2 Product Brief April 2010 Complies with industry standards EEMUA 191 and OSHA PSM 1910.119 for Alarm Analytics, connects to all major
Product Brief for Alarm Analytics V9.2 April 2010 Alarm Analytics V9.2 Product Brief April 2010 Complies with industry standards EEMUA 191 and OSHA PSM 1910.119 for Alarm Analytics, connects to all major
LANDSCAPE INFOGRAPHIC DESIGN. Markéta Krejčí, PhD Iva Hradilová Mendel University of Brno, Czech Republic
 LANDSCAPE INFOGRAPHIC DESIGN Markéta Krejčí, PhD Iva Hradilová Mendel University of Brno, Czech Republic Abstract This lack of understanding is caused by the urban environment complexity as cities and
LANDSCAPE INFOGRAPHIC DESIGN Markéta Krejčí, PhD Iva Hradilová Mendel University of Brno, Czech Republic Abstract This lack of understanding is caused by the urban environment complexity as cities and
Smart Water Networks for Efficiency Gains
 Smart Water Networks for Efficiency Gains Standards Certification Education & Training Publishing Conferences & Exhibits Speaker: Brian Heimbigner Co-author: Mark Bitto 2013 ISA Water / Wastewater and
Smart Water Networks for Efficiency Gains Standards Certification Education & Training Publishing Conferences & Exhibits Speaker: Brian Heimbigner Co-author: Mark Bitto 2013 ISA Water / Wastewater and
A Study on Improvement of Fire Protection Systems based on Failure Characteristics accodrding to Yearly Variation in Old Commercial Buildings
 Indian Journal of Science and Technology, Vol 9(24), DOI: 10.17485/ijst/2016/v9i24/96032, June 2016 ISSN (Print) : 0974-6846 ISSN (Online) : 0974-5645 A Study on Improvement of Fire Protection Systems
Indian Journal of Science and Technology, Vol 9(24), DOI: 10.17485/ijst/2016/v9i24/96032, June 2016 ISSN (Print) : 0974-6846 ISSN (Online) : 0974-5645 A Study on Improvement of Fire Protection Systems
Research on the Monitor and Control System of Granary Temperature and Humidity Based on ARM
 Research on the Monitor and Control System of Granary Temperature and Humidity Based on ARM Liu Yang 1, Xinrong Cheng 2, Zhijie Jiang 3, and Zhijun Ren 1 1 Engineering College, China Agricultural University,
Research on the Monitor and Control System of Granary Temperature and Humidity Based on ARM Liu Yang 1, Xinrong Cheng 2, Zhijie Jiang 3, and Zhijun Ren 1 1 Engineering College, China Agricultural University,
Methods of Software Integration of Alarm Systems
 Methods of Software Integration of Alarm Systems Jan Valouch Faculty of Applied Informatics Tomas Bata University in Zlin Nad Stranemi 4511, CZ 76005 Zlin Czech Republic valouch@fai.utb.cz Abstract This
Methods of Software Integration of Alarm Systems Jan Valouch Faculty of Applied Informatics Tomas Bata University in Zlin Nad Stranemi 4511, CZ 76005 Zlin Czech Republic valouch@fai.utb.cz Abstract This
Milestone SMI Intrepid II Perimeter Module 1.1 User s Manual
 Milestone SMI Intrepid II Perimeter Module 1.1 User s Manual Target Audience for this Document This document is aimed at system users and provides descriptions on how to install and maintain the Milestone
Milestone SMI Intrepid II Perimeter Module 1.1 User s Manual Target Audience for this Document This document is aimed at system users and provides descriptions on how to install and maintain the Milestone
Remote fiber testing to improve SLA s
 Remote fiber testing to improve SLA s Presented by : Kamel SOUILAH System Sales Engineer kamel.souilah@exfo.com 2010 EXFO Inc. All rights reserved.. 1 EXFO is the leader in the test and measurement solutions
Remote fiber testing to improve SLA s Presented by : Kamel SOUILAH System Sales Engineer kamel.souilah@exfo.com 2010 EXFO Inc. All rights reserved.. 1 EXFO is the leader in the test and measurement solutions
Lesson 11 Internet Connected Environment (Weather, Air Pollution and Forest Fire) Monitoring
 Lesson 11 Internet Connected Environment (Weather, Air Pollution and Forest Fire) Monitoring 1 Environment Monitoring Weather Uses of sensors for T, RH and Patm parameters, WSNs, access points, gateways
Lesson 11 Internet Connected Environment (Weather, Air Pollution and Forest Fire) Monitoring 1 Environment Monitoring Weather Uses of sensors for T, RH and Patm parameters, WSNs, access points, gateways
False Alarm Suppression in Early Prediction of Cardiac Arrhythmia
 IEEE International Conference on Bioinformatics & Bioengineering 2015 False Alarm Suppression in Early Prediction of Cardiac Arrhythmia Shoumik Roychoudhury, Mohamed F. Ghalwash, Zoran Obradovic Presented
IEEE International Conference on Bioinformatics & Bioengineering 2015 False Alarm Suppression in Early Prediction of Cardiac Arrhythmia Shoumik Roychoudhury, Mohamed F. Ghalwash, Zoran Obradovic Presented
Smart Defrost Control for Refrigeration System
 Smart Defrost Control for Refrigeration System 1 V. Bagyaveereswaran, 2 S. Shiva Subramanian and R. Anitha 3 1,2, School of Electrical Engineering, Vellore Institute of Technology (VIT University), Vellore
Smart Defrost Control for Refrigeration System 1 V. Bagyaveereswaran, 2 S. Shiva Subramanian and R. Anitha 3 1,2, School of Electrical Engineering, Vellore Institute of Technology (VIT University), Vellore
Stability of Inclined Strip Anchors in Purely Cohesive Soil
 Stability of Inclined Strip Anchors in Purely Cohesive Soil R. S. Merifield 1 ; A. V. Lyamin 2 ; and S. W. Sloan 3 Abstract: Soil anchors are commonly used as foundation systems for structures requiring
Stability of Inclined Strip Anchors in Purely Cohesive Soil R. S. Merifield 1 ; A. V. Lyamin 2 ; and S. W. Sloan 3 Abstract: Soil anchors are commonly used as foundation systems for structures requiring
Product Brief for Alarm Analytics V9.3 October 2013
 Product Brief for Alarm Analytics V9.3 October 2013 Alarm Analytics V9.3 Product Brief October 2013 Complies with industry standards EEMUA 191 and OSHA PSM 1910.119 for Alarm Analytics, connects to all
Product Brief for Alarm Analytics V9.3 October 2013 Alarm Analytics V9.3 Product Brief October 2013 Complies with industry standards EEMUA 191 and OSHA PSM 1910.119 for Alarm Analytics, connects to all
Fire Detection Using Image Processing
 Fire Detection Using Image Processing Ku. R.A.Agrawal ME Student Department of CSE Babasaheb Naik college of Engineering Pusad, India rachanaagrawal90@gmail.com Prof. S.T.Khandare Associate professor Department
Fire Detection Using Image Processing Ku. R.A.Agrawal ME Student Department of CSE Babasaheb Naik college of Engineering Pusad, India rachanaagrawal90@gmail.com Prof. S.T.Khandare Associate professor Department
Itron Water Loss Management Solutions. Advanced Digital Leak Detection Overview Session
 Itron Water Loss Management Solutions Advanced Digital Leak Detection Overview Session Pipeline Assessment Management The Hidden/Aware/Locate/Repair cycle of a leak can cause extensive water loss The Conventional
Itron Water Loss Management Solutions Advanced Digital Leak Detection Overview Session Pipeline Assessment Management The Hidden/Aware/Locate/Repair cycle of a leak can cause extensive water loss The Conventional
Integrating fire-spread and household-level trigger modeling to stage wildfire evacuation warnings
 Integrating fire-spread and household-level trigger modeling to stage wildfire evacuation warnings Dapeng. Li 1, Thomas. J. Cova 1, Philip. E. Dennison 1 1 Department of Geography, University of Utah,
Integrating fire-spread and household-level trigger modeling to stage wildfire evacuation warnings Dapeng. Li 1, Thomas. J. Cova 1, Philip. E. Dennison 1 1 Department of Geography, University of Utah,
Design and Development of General Purpose Alarm Generator for Automated System
 Design and Development of General Purpose Alarm Generator for Automated System Amit Pandey 1 1 CSIR-Central Scientific Instruments Organisation India Abstract: This paper presents a model for general purpose
Design and Development of General Purpose Alarm Generator for Automated System Amit Pandey 1 1 CSIR-Central Scientific Instruments Organisation India Abstract: This paper presents a model for general purpose
This section describes how Prime Central locates, diagnoses, and reports network problems.
 This section describes how Prime Central locates, diagnoses, and reports network problems. Prime Central Fault Management uses a very limited version of the IBM Tivoli Netcool/OMNIbus technology. Some
This section describes how Prime Central locates, diagnoses, and reports network problems. Prime Central Fault Management uses a very limited version of the IBM Tivoli Netcool/OMNIbus technology. Some
Research on Evaluation of Fire Detection Algorithms
 Research on Evaluation of Fire Detection Algorithms JIAN LI 1,2, WENHUI DONG 1, ZHIBIN MEI 1, and ZHUOFU WANG 1 1 Shenyang Fire Research Institute Ministry of Public Security China, 110031 2 Dalian University
Research on Evaluation of Fire Detection Algorithms JIAN LI 1,2, WENHUI DONG 1, ZHIBIN MEI 1, and ZHUOFU WANG 1 1 Shenyang Fire Research Institute Ministry of Public Security China, 110031 2 Dalian University
A design of automatic boiler intelligent alert system based on the wireless AD hoc network
 5th International Conference on Computer Sciences and Automation Engineering (ICCSAE 2015) A design of automatic boiler intelligent alert system based on the wireless AD hoc network Shiping Li1, a Maodong
5th International Conference on Computer Sciences and Automation Engineering (ICCSAE 2015) A design of automatic boiler intelligent alert system based on the wireless AD hoc network Shiping Li1, a Maodong
A Design Method Based on Inherent Testability of Remote Control and Monitoring System for Marine Main Engine
 5th International Conference on Advanced Engineering Materials and Technology (AEMT 2015) A Design Method Based on Inherent Testability of Remote Control and Monitoring System for Marine Main Engine Xuedong
5th International Conference on Advanced Engineering Materials and Technology (AEMT 2015) A Design Method Based on Inherent Testability of Remote Control and Monitoring System for Marine Main Engine Xuedong
A Study on the Characteristics of Planning within Analyzing of Exterior Space in Mixed-use Development 1
 , pp.25-29 http://dx.doi.org/10.14257/astl.2014.47.06 A Study on the Characteristics of Planning within Analyzing of Exterior Space in Mixed-use Development 1 Lee-yong Sung Division of architecture, Mokwon
, pp.25-29 http://dx.doi.org/10.14257/astl.2014.47.06 A Study on the Characteristics of Planning within Analyzing of Exterior Space in Mixed-use Development 1 Lee-yong Sung Division of architecture, Mokwon
EVACUATION MODELLING IN ROAD TUNNEL FIRES
 Complex Underground Multipurpose Facilities: Safety Challenges and Solutions Workshop organised by the ITA-COSUF as part of the ITA-AITES World Tunnel Congress 2013 EVACUATION MODELLING IN ROAD TUNNEL
Complex Underground Multipurpose Facilities: Safety Challenges and Solutions Workshop organised by the ITA-COSUF as part of the ITA-AITES World Tunnel Congress 2013 EVACUATION MODELLING IN ROAD TUNNEL
The design of automatic remote monitoring system for the temperature and humidity based on GPRS Hui ZHANG 1, a, Honghua WANG 2,a
 Applied Mechanics and Materials Submitted: 2014-06-06 ISSN: 1662-7482, Vols. 599-601, pp 1102-1105 Accepted: 2014-06-09 doi:10.4028/www.scientific.net/amm.599-601.1102 Online: 2014-08-11 2014 Trans Tech
Applied Mechanics and Materials Submitted: 2014-06-06 ISSN: 1662-7482, Vols. 599-601, pp 1102-1105 Accepted: 2014-06-09 doi:10.4028/www.scientific.net/amm.599-601.1102 Online: 2014-08-11 2014 Trans Tech
PRESENTS AQUADUCT AUTOMATED WATER-LEAK MONITORING SYSTEM A KINGPIN TECHNOLOGY
 PRESENTS AQUADUCT AUTOMATED WATER-LEAK MONITORING SYSTEM A KINGPIN TECHNOLOGY INTRODUCING THE INNOVATIVE NEW TECHNOLOGY FOR THE DETECTION OF LEAKS IN WATER NETWORKS. SA WATER CRISIS the rising tide The
PRESENTS AQUADUCT AUTOMATED WATER-LEAK MONITORING SYSTEM A KINGPIN TECHNOLOGY INTRODUCING THE INNOVATIVE NEW TECHNOLOGY FOR THE DETECTION OF LEAKS IN WATER NETWORKS. SA WATER CRISIS the rising tide The
Remote Monitoring of Offshore Structures using Acoustic Emission.
 11th European Conference on Non-Destructive Testing (ECNDT 2014), October 6-10, 2014, Prague, Czech Republic Remote Monitoring of Offshore Structures using Acoustic Emission. More Info at Open Access Database
11th European Conference on Non-Destructive Testing (ECNDT 2014), October 6-10, 2014, Prague, Czech Republic Remote Monitoring of Offshore Structures using Acoustic Emission. More Info at Open Access Database
Improved occupancy detection accuracy using PIR and door sensors for a smart thermostat
 Improved occupancy detection accuracy using and door sensors for a smart thermostat Sun Ho Kim 1, Hyeun Jun Moon 1, Young Ran Yoon 1 1 Department of Architectural Engineering, Dankook University, Yongin,
Improved occupancy detection accuracy using and door sensors for a smart thermostat Sun Ho Kim 1, Hyeun Jun Moon 1, Young Ran Yoon 1 1 Department of Architectural Engineering, Dankook University, Yongin,
BMS. University of Economics in Katowice. Supervisory and Control System for University Buildings in Katowice
 BMS University of Economics in Supervisory and Control System for University Buildings in R E L I A B L E S O L U T I O N S O F A U T O M A T I O N S Y S T E M S Doc. No. ENPN013 Version: 06-11-2015 ASKOM
BMS University of Economics in Supervisory and Control System for University Buildings in R E L I A B L E S O L U T I O N S O F A U T O M A T I O N S Y S T E M S Doc. No. ENPN013 Version: 06-11-2015 ASKOM
Experimental Investigate on the Performance of High Temperature Heat Pump Using Scroll Compressor
 Experimental Investigate on the Performance of High Temperature Heat Pump Using Scroll Compressor Mingyue Huang a, Xiangfei Liang a,b *, Rong Zhuang a a Gree Electric Appliances, Inc.of Zhuhai,Zhuhai 519070,China
Experimental Investigate on the Performance of High Temperature Heat Pump Using Scroll Compressor Mingyue Huang a, Xiangfei Liang a,b *, Rong Zhuang a a Gree Electric Appliances, Inc.of Zhuhai,Zhuhai 519070,China
Facility Commander Complete, Integrated Command and Control
 Facility Commander Complete, Integrated Command and Control 2.0 Facility Commander Complete, integrated command and control Securing your business facilities requires multiple systems, often from different
Facility Commander Complete, Integrated Command and Control 2.0 Facility Commander Complete, integrated command and control Securing your business facilities requires multiple systems, often from different
Development of Open BIM-based Code Checking Modules for the Regulations of the Fire and Evacuation
 Development of Open BIM-based Code Checking Modules for the Regulations of the Fire and Evacuation Jungsik Choi 34, Junho Choi 35, Geunha Cho 36 and Inhan Kim 37 34 buildingsmart Korea 35,36,37 Kyung Hee
Development of Open BIM-based Code Checking Modules for the Regulations of the Fire and Evacuation Jungsik Choi 34, Junho Choi 35, Geunha Cho 36 and Inhan Kim 37 34 buildingsmart Korea 35,36,37 Kyung Hee
SIL DETERMINATION AND PROBLEMS WITH THE APPLICATION OF LOPA
 SIL DETERMINATION AND PROBLEMS WITH THE APPLICATION OF LOPA Alan G King Hazard & Reliability Specialist, ABB Engineering Services, Billingham, Cleveland UK. TS23 4YS For a number of years, industry has
SIL DETERMINATION AND PROBLEMS WITH THE APPLICATION OF LOPA Alan G King Hazard & Reliability Specialist, ABB Engineering Services, Billingham, Cleveland UK. TS23 4YS For a number of years, industry has
A Forest Fire Warning Method Based on Fire Dangerous Rating Dan Wang 1, a, Lei Xu 1, b*, Yuanyuan Zhou 1, c, Zhifu Gao 1, d
 International Conference on Applied Science and Engineering Innovation (ASEI 2015) A Forest Fire Warning Method Based on Fire Dangerous Rating Dan Wang 1, a, Lei Xu 1, b*, Yuanyuan Zhou 1, c, Zhifu Gao
International Conference on Applied Science and Engineering Innovation (ASEI 2015) A Forest Fire Warning Method Based on Fire Dangerous Rating Dan Wang 1, a, Lei Xu 1, b*, Yuanyuan Zhou 1, c, Zhifu Gao
EE04 804(B) Soft Computing Ver. 1.2 Class 1. Introduction February 21st,2012. Sasidharan Sreedharan
 EE04 804(B) Soft Computing Ver. 1.2 Class 1. Introduction February 21st,2012 Sasidharan Sreedharan www.sasidharan.webs.com 1 Syllabus Artificial Intelligence Systems- Neural Networks, fuzzy logic, genetic
EE04 804(B) Soft Computing Ver. 1.2 Class 1. Introduction February 21st,2012 Sasidharan Sreedharan www.sasidharan.webs.com 1 Syllabus Artificial Intelligence Systems- Neural Networks, fuzzy logic, genetic
A Simulation Study on the Energy Efficiency of Gas-Burned Boilers in Heating Systems
 International Journal of Energy and Power Engineering 2015; 4(6): 327-332 Published online December 5, 2015 (http://www.sciencepublishinggroup.com/j/ijepe) doi: 10.11648/j.ijepe.20150406.11 ISSN: 2326-957X
International Journal of Energy and Power Engineering 2015; 4(6): 327-332 Published online December 5, 2015 (http://www.sciencepublishinggroup.com/j/ijepe) doi: 10.11648/j.ijepe.20150406.11 ISSN: 2326-957X
Welcome to a world where technology flows through the heart of your business environment. Welcome to CDC
 Welcome to a world where technology flows through the heart of your business environment Welcome to CDC Introduction to Integra 4 Integra configuration 4 Graphical Supervisor 6 Integra difference 8 Integra
Welcome to a world where technology flows through the heart of your business environment Welcome to CDC Introduction to Integra 4 Integra configuration 4 Graphical Supervisor 6 Integra difference 8 Integra
Flood Monitoring and Early Warning System Using Ultrasonic Sensor
 IOP Conference Series: Materials Science and Engineering PAPER OPEN ACCESS Flood Monitoring and Early Warning System Using Ultrasonic Sensor To cite this article: J G Natividad and J M Mendez 2018 IOP
IOP Conference Series: Materials Science and Engineering PAPER OPEN ACCESS Flood Monitoring and Early Warning System Using Ultrasonic Sensor To cite this article: J G Natividad and J M Mendez 2018 IOP
HOT IN HERE: OFFICE OCCUPANT THERMAL COMFORT IN LAWRENCE HALL
 GROUP 1 HOT IN HERE: OFFICE OCCUPANT THERMAL COMFORT IN LAWRENCE HALL Daniel Abrahamson Department of Architecture University of Oregon Eugene, Oregon 97403 dva@uoregon.edu Dijon Jones Department of Architecture
GROUP 1 HOT IN HERE: OFFICE OCCUPANT THERMAL COMFORT IN LAWRENCE HALL Daniel Abrahamson Department of Architecture University of Oregon Eugene, Oregon 97403 dva@uoregon.edu Dijon Jones Department of Architecture
Statistical cluster analysis and visualisation for alarm management configuration. Butters, T D and Güttel, S and Shapiro, J L and Sharpe, T J
 Statistical cluster analysis and visualisation for alarm management configuration Butters, T D and Güttel, S and Shapiro, J L and Sharpe, T J 2014 MIMS EPrint: 2014.51 Manchester Institute for Mathematical
Statistical cluster analysis and visualisation for alarm management configuration Butters, T D and Güttel, S and Shapiro, J L and Sharpe, T J 2014 MIMS EPrint: 2014.51 Manchester Institute for Mathematical
Using fault tree analysis to identify the failures of level crossing protection devices
 The Sustainable City VII, Vol. 2 1197 Using fault tree analysis to identify the s of level crossing protection devices J. C. Jong 1, T. H. Lin 1, C. S. Suen 1, C. K. Lee 2, I. C. Chen 3 & H. J. Wu 3 1
The Sustainable City VII, Vol. 2 1197 Using fault tree analysis to identify the s of level crossing protection devices J. C. Jong 1, T. H. Lin 1, C. S. Suen 1, C. K. Lee 2, I. C. Chen 3 & H. J. Wu 3 1
Alarm setup and definitions in Cisco Unified Serviceability
 Alarm setup and definitions in Cisco Unified Serviceability Set up Cisco Unified IM and Presence Serviceability alarms, page 1 Alarm setup and update for a service, page 2 Alarm definitions and user-defined
Alarm setup and definitions in Cisco Unified Serviceability Set up Cisco Unified IM and Presence Serviceability alarms, page 1 Alarm setup and update for a service, page 2 Alarm definitions and user-defined
DelPro for stanchion barns The integrated dairy management system. Handing you better control
 DelPro for stanchion barns The integrated dairy management system Handing you better control Modern tools for traditional stanchion dairy farms Improving on tradition DeLaval DelPro integrated dairy management
DelPro for stanchion barns The integrated dairy management system Handing you better control Modern tools for traditional stanchion dairy farms Improving on tradition DeLaval DelPro integrated dairy management
System Description AutroMaster V Presentation System
 System Description AutroMaster V Presentation System AMASTERV-SYSTEM/XGB, Rev. B, 2018-05-07, Autronica Fire And Security AS COPYRIGHT This publication, or parts thereof, may not be reproduced in any form,
System Description AutroMaster V Presentation System AMASTERV-SYSTEM/XGB, Rev. B, 2018-05-07, Autronica Fire And Security AS COPYRIGHT This publication, or parts thereof, may not be reproduced in any form,
LESSON PLAN TOUCHCAST USAGE IN EDUCATION
 LESSON PLAN USAGE IN EDUCATION BY MR. BRIAN JONES SCIENCE - GENETICS -7TH GRADE TouchCast // Science // Lesson Plan Units 1-3 Genetics - Units 1-3 Grades : 7th grade Created by : Brian Jones and TouchCast
LESSON PLAN USAGE IN EDUCATION BY MR. BRIAN JONES SCIENCE - GENETICS -7TH GRADE TouchCast // Science // Lesson Plan Units 1-3 Genetics - Units 1-3 Grades : 7th grade Created by : Brian Jones and TouchCast
PSRC REVIEW REPORT & CERTIFICATION RECOMMENDATION
 PSRC REVIEW REPORT & CERTIFICATION RECOMMENDATION KITSAP COUNTY COUNTYWIDE PLANNING POLICIES July 2, 2012 BACKGROUND A major emphasis of the Washington State Growth Management Act (GMA) is the need to
PSRC REVIEW REPORT & CERTIFICATION RECOMMENDATION KITSAP COUNTY COUNTYWIDE PLANNING POLICIES July 2, 2012 BACKGROUND A major emphasis of the Washington State Growth Management Act (GMA) is the need to
SYNERGY IN LEAK DETECTION: COMBINING LEAK DETECTION TECHNOLOGIES THAT USE DIFFERENT PHYSICAL PRINCIPLES
 Proceedings of the 2014 10 th International Pipeline Conference IPC2014 September 29-October 3, 2014, Calgary, Alberta, Canada IPC2014-33387 SYNERGY IN LEAK DETECTION: COMBINING LEAK DETECTION TECHNOLOGIES
Proceedings of the 2014 10 th International Pipeline Conference IPC2014 September 29-October 3, 2014, Calgary, Alberta, Canada IPC2014-33387 SYNERGY IN LEAK DETECTION: COMBINING LEAK DETECTION TECHNOLOGIES
Design Procedure for a Liquid Dessicant and Evaporative Cooling Assisted 100% Outdoor Air System
 Design Procedure for a Liquid Dessicant and Evaporative Cooling Assisted 100% Outdoor Air System M.H.Kim 1, J.Y.Park 1, E.J.Lee 2, and J.W.Jeong 1* 1 Department of Architectural Engineering, Hanyang University,
Design Procedure for a Liquid Dessicant and Evaporative Cooling Assisted 100% Outdoor Air System M.H.Kim 1, J.Y.Park 1, E.J.Lee 2, and J.W.Jeong 1* 1 Department of Architectural Engineering, Hanyang University,
Getting Started with Live Exceptions
 Getting Started with Live Exceptions Live Exceptions provides alarm reporting by identifying problems that include delay, errors, failures, security, or configuration changes. The Live Exceptions Browser
Getting Started with Live Exceptions Live Exceptions provides alarm reporting by identifying problems that include delay, errors, failures, security, or configuration changes. The Live Exceptions Browser
