Detection of Temporal Dependencies in Alarm Time Series of Industrial Plants
|
|
|
- Dwight Whitehead
- 5 years ago
- Views:
Transcription
1 Preprints of the 19th World Congress The International Federation of Automatic Control Detection of Temporal Dependencies in Alarm Time Series of Industrial Plants Jens Folmer, Falk Schuricht and Birgit Vogel-Heuser Institute for Automation and Information Systems Technische Universität München, Garching near Munich ( folmer,schuricht, ais.mw.tum.de) Abstract: Concerning industrial plants, operators face the problem that more alarms are generated than can be physically perceived and addressed by a single operator. Such a situation is called alarm flood. The main reason for alarm floods are causally related disturbances, which either way raise an alarm, based on a single causal disturbance. These dependencies are difficult to recognize during the engineering of an AMS (Alarm Management System). However, the alarms are logged and stored as time series (historical data). Information about the alarm types and the time stamps of their occurrence can be used to analyze the time series data and thus finding dependencies between different alarms. This contribution presents an approach to find temporal dependencies between alarm events in an alarm time series. Therefore an algorithm was designed, implemented, and evaluated to detect temporal dependencies in alarm time series. Keywords: Timing Series Analysis, Manufacturing Processes, Process Automation, Data Processing, Alarm Systems, Delay Analysis 1. INTRODUCTION Process Control Systems (PCS) are one of the core elements in process control industry such as oil refineries or pharmaceutical and chemical plants. The PCS presents the most important information about the process plant to the operator. In addition to the observation of process data, the operator has to recognize abnormal plant situations. An abnormal plant situation is indicated by process visualizations and alarm lists. Messages about abnormal plant situations can be divided into two types, defined by the EEMUA (2013) as alarm and alert. An information message is indicated by using textual or graphical elements, e.g. based on a P&ID (IEC (2013)). The alarm management system (AMS) is an integral component of the PCS. The AMS presents detailed information of raised alarms in a chronological or priority order visualized by a table. By intervening, the operator is able to clear abnormal situations. Due to causal dependencies of failures (e.g. based on process/material flow), too many alarms may frequently be raised. Each alarm is displayed to the operator, who must handle this vast quantity of alarms. This effect is called alarm flood. Operators only acknowledge alarms, while handling the abnormal situation based on their process knowledge and experience. In such situations operators do not have enough time to analyze every alarm properly without exceeding the recommended operator response time. Thus, the prediction and reduction of alarm floods has a high priority when improving alarm systems design. The EEMUA 191 recommends an alarm rate less than one alarm per 10 minutes in steady operation. To reduce the quantity of alarms, on the one hand improved visualizations can be applied to reduce the overload of information as proposed in Pantforder and Vogel-Heuser (2009); Folmer et al. (2011). On the other hand, one should identify causal dependent alarms based on time series analysis to predict causal dependent malfunctions to inform operators, which then are able to intervene earlier. Those causal dependent alarms become more apparent when alarms are generated during plants run-time. The different generated alarms are stored in an alarm log as historical records of all alarms. These alarm logs can be automatically analyzed in order to find temporal and causal dependencies between alarms, by using statistical analysis techniques. The results of the analysis can be reviewed by experts to re-design the AMS or/and to design a forecast system. The reminder of the contribution is as follows. Related work on time series analysis is presented in section 2. In section 3, a new approach to find causal dependent alarms is proposed. The results of the analysis based on industrial data logs are presented in section 4. Section 5 concludes this contribution and introduces further research. 2. RELATED WORK ON ALARM DATA CAUSALITY ANALYSIS Data Mining methods are used to discover important information in large data sets. Regarding alarm data sets and causality analysis, the important information is represented by a sequence of alarm events, which occur at certain time stamps. In this section, related works to find causal dependent alarms by consideration of time are presented. Copyright 2014 IFAC 1802
2 2.1 Sequential Pattern Mining Sequential Pattern Mining, a sub discipline of Data Mining, is focusing on methods to find pattern in sequential data sets. Zhao and Bhowmick (2003) as well as Boghey and Singh (2013) give an overview of several Sequential Pattern Mining methods. Sequential data can be represented by a single sequence or a set of sequences containing single elements. A sequence is an amount of elements, which can be ordered (e.g. by time) or in random order. Often additional information, like geometrical or temporal data, is stored along with each element within a sequence. Sequences can for instance be represented as a string or a number of logged events whereat each event is generated during the plants run-time, e.g. a failure event. The objective of Sequential Pattern Mining is to find interesting patterns in the data set. Patterns can be an amount of frequently occurring elements. They can also be subsequences, which are correlated with interesting events. In addition, dependencies between sub-sequences can be found by examining their frequency of occurrence or by ordering in the data set. Important information in alarm data sets are sub-sequences, which occur frequently. The detection and analysis of the dependencies of these subsequences lead to structural information about the alarm sequence. The authors themselves (Folmer and Vogel-Heuser (2012)) presented the Automatic Alarm Data Analyzer (AADA) Algorithm. It clusters frequent occurring sub-sequences in alarm logs, by searching alarm sequences using finite automaton. Each recognized alarm (in the alarm log) is represented by a state and transitions are used to represent state transitions of the alarm that is raised. This leads to an automaton, which encapsulates the overall structure of the sequential data. The authors extracted time dependencies by ordering the alarms in the alarm log, but did not use time dependencies during the analysis itself for recognizing causal dependencies. However, they pointed out how important pre-processing of the alarm log is by taking important alarm types into account and not the overall alarm log. Ahmed et al. (2013) introduce several methods of analyzing alarm flood data. Alarm floods consist of a set of ordered alarm events. They are determined by clustering alarm floods and comparing them to each other. Similarity between the flood is measured by finding a mapping between alarm flood with dynamic time warping. However, these methods do not consider temporal information to find useful patterns or dependencies. All proposed approaches focus on determining relationships between events in general. Only Ahmed et al. (2013) focus on alarms in industrial automation or industrial plants. However, previously mentioned approaches do not consider time intervals between single events. Additionally, they are only dealing with pattern sequences. 2.2 Time-Series Data Mining Time-Series Data Mining deals with huge sequences of elements having a temporal order. Esling and Agon (2012) and Fu (2011) give an overview over several techniques of Time-Series Data Mining. Some methods concentrate on changing the representation of time-series to reduce the dimensionality or on enhancing the performance of other mining techniques. Main task is finding sequences or subsequences in the time-series, which occur frequently or have some abnormal features. For that purpose, sequences or sub-sequences are often compared to each other using a similarity measure. The sub-sequences in the timeseries are then clustered to find some overall structure. Temporal aspects are taken into account regarding the found clusters. The temporal behavior of the time-series in terms of time intervals between sequence elements or the detection of cyclic occurring patterns is then analyzed. Of particular interest is to find causal relationships in time-series. This task is called Temporal Association Rule Mining. Even if the approaches mentioned above are taking time intervals into consideration, no research is dealing with uncertainty of time intervals between data points. Furthermore, they do not focus on alarms of industrial automation systems. 2.3 Association Rule Mining Schluter and Conrad (2011) describe several approaches to find association rules in time-series. A temporal relationship is discovered by analyzing the ordering and interval of sub-sequences in a time-series. If a sub-sequence B follows a sub-sequence A within a certain time frame, there is a temporal dependency. Association rules can be found by regarding the temporal order, also between different timeseries. Associated events can occur periodically in a time-series. Some approaches like Thuan et al. (2012) and Li et al. (2001) focus on finding cyclic association rules, i.e. rules that are always true in certain time intervals. Höppner and Klawonn (2002) and Bouandas and Osmani (2007) developed methods to find temporal association rules in sequences that consist of intervals. A sequence is regarded as a set of states, which have a defined start and end time. These state intervals are related to each other. Rules are found by determining frequent occurrences of interval relationships. In Mannila et al. (1995) an algorithm is developed, which finds frequent episodes in sequences of events. An episode is a set of events, which occur frequently in a certain order. In this approach, time is taken into account by defining a time frame, in which episodes can be found in the event time-series. The presented approaches incorporate time in different ways. Often (pre-defined) time frames are regarded in which certain sub-sequences must follow each other, to be taken into account for a temporal dependency. Ordering and relationships of temporal state intervals are also used to find association rules. In the presented contribution, association rules are found by regarding time intervals of explicit length between elements of a sequence. The approach assumes that the emergence of a sequence element causes the occurrence of another element after a certain time. Those causal dependencies, which incorporate hard real time constraints, can detect unknown interrelations in data sets, which can lead to better understanding of the underlying processes. 1803
3 3. DEVELOPED CONCEPT A time series can be obtained from an alarm log with N alarms. Each time an alarm is raised, it is logged with the time stamp of its occurrence. The corresponding alarm log A log can then be formulated as a set of ordered elements as follows: A log = {a 1, a 2,..., a N 1, a N } (1) Whereat a N occurs after a N 1. Each alarm a N is a tuple a i = (t i, c i ), i N, 1 i N = A log (2) where c i is a unique alarm identifier (ID usually an identifying number), which occurs at a certain time t i. In the following, two alarms with IDs ID c (cause alarm) and ID e (effected alarm) are considered. Alarms with ID e are an effect of a caused alarms with ID c after a certain time interval. Depending on the considered process, this time interval may deviate. In this contribution, this time interval which indicates a causal dependency between cause and effect is called a temporal relationship. The existence of such a relationship is verified by statistical methods. 3.1 Statistical description of temporal relationships Inspecting the two related alarms of the corresponding alarm log (log), ID e is assumed to be caused by ID c. In case of the temporal relationships regarded in this paper, an occurrence of ID c always causes ID e after a certain time with some deviation. The time interval, in which these alarms follow each other, is used as a random variable. This random variable can be described by a probability density function. Parameters of the density function are estimated by analyzing all existing time intervals between two related alarms in the log. Resulting in a probability distribution, a confidence interval is used to verify that the temporal interval has a high probability within the defined boundary and, hence, a high significance. However, this approach assumes that every raised alarm potentially causes another alarm. There is also the possibility, that an alarm is sometimes caused by another event, e.g. if the operator intervenes early to bring under control the abnormal situation as soon as the effected alarm occurs. In that case, time intervals would lead to wrong probability density functions. To tackle this challenge, in the next section the possible mappings between alarms are described. Fig. 1. Two examples of possible temporal relationships between alarm in an alarm log which may occurs the log with alarm ID ID e, whereby some independent alarms occur between the dependent alarms. To discover a temporal relationship, the first occurrence of an alarm with ID e after emergence of an alarm with ID c can be used to calculate the time interval between both alarms. However, in real data sets, initiating alarms can also occur in columns (see Fig. 1 (b)), e.g. flicker alarms. If there is a temporal relationship with a large time interval and if only the next occurrence of the caused alarm (first alarm of the column of caused alarms) is taken into account, the dependency will be missed. To capture these relationships, also time intervals, in which temporal dependencies are assumed, must be known. Hence, alarms with ID e in the regarded time interval can be investigated and relationships can be found. This information leads to the formulation of a condition for temporal dependencies, which is explained in the next subsection. 3.3 Condition to determine temporal dependencies Supposing there is a temporal dependency after a time interval t, one can define a condition including a possible deviation as follows: t i + t t j < ɛ (3) Where t i corresponds to an alarm with c i = ID c and respectively t j to an alarm with c j = ID e. That means the two alarms a i and a j of the log follow each other with a time interval t within a maximal deviation ɛ. In case this condition holds for a certain amount of occurrences of a i, a temporal dependency is assumed for the alarms with the IDs ID c and ID e. Fig. 2 illustrates the condition graphically. 3.2 Mapping cause and effects of alarms In case of the temporal relationships, an occurrence of ID c causes ID e after a certain time with some deviation. However, it is not a priori obvious, which root cause alarm must be mapped to the corresponding affected alarm, because the proposed approach does not include additional information, e.g. plant structure. Fig. 1 shows two examples of possible mappings between alarms. In Fig. 1 (a), the caused alarm is always the next alarm in Fig. 2. Alarm log with two dependent alarms within time t and deviation ɛ 1804
4 This condition can now be used to formulate a conditional probability of a temporal relationship between alarms with ID c and ID e. The conditional probability is defined as follows: P (a i a j ) = P (a i a j ) P (a j ) (4) The probability of two random alarms a i and a j can then be formulated as the probability of occurrence of ID c and ID e within time interval t with a maximum deviation ɛ divided by the probability of occurrence of ID c. In case the calculated probability is higher than a certain threshold P thr, there is a temporal dependency between alarms with ID c and ID e in the time interval t with a maximum deviation ɛ. The threshold value P thr has to be chosen manually, e.g based on the dead-times and/or speed of the process. Thus the conditional probability can be formulated in a mathematical function depending on the occurrences of alarms in the log. P (ID c, ID e, ɛ, t) = N 1 N 2 (5) N 1 = {c i (t i, c i ) A log (6) (t j, c j ) A log c i = ID c c j = ID e t i + t t j < ɛ)} N 2 = {c i (t i, c i ) S c i = ID c } (7) This function only describes a relationship between two observed alarms in a particular time interval t and a certain deviation ɛ. Evaluating all possible combinations of alarms to calculate all time intervals and deviations leads to a high computational effort. Therefore only alarms which have a certain minimal occurrence min occ in the log have to be considered. Alarms that occur rarely in corresponding log are ignored by the algorithm. This does not mean that rarely occurring alarms are unimportant but, furthermore, the results of the proposed approach are not significant in this case because there are not enough samples. The next challenge is to choose an appropriate time interval for the considered alarm tuples. Since the time distribution of the alarm around a certain alarm is unknown, an estimation of the time interval is a challenging task. A promising method is to analyze many time intervals, which cover a whole time frame after the occurrence of the initial alarm (alarm with ID ID c ) in the log. In this contribution, time intervals in uniform intervals are chosen using a histogram. The bins depend on the deviation ɛ. tmax ɛ t i = ɛ + 2 ɛ i, i = 0...M, M = 2 ɛ (8) Fig. 3. Possible discrete derivations of probabilities of an alarm event tuple (a) Ideal temporal dependence (b) Uniformly distributed time intervals between events with ID c and ID e By choosing these time intervals, every point in time until t max after the occurrence of the initial alarm is exposed. Thus no temporal dependence will be missed. To find temporal relationships, the maximal time that has to be analyzed is t max. However, this approach only regards a finite set of time intervals. Temporal dependencies which have not exactly one of the time intervals t i can also be found. This depends on the real deviation of the time intervals of the related alarms around the caused alarm. The next analysis step is to compute for every relevant alarm tuples the corresponding probabilities for all time intervals t i. The probabilities can be obtained by iterating over the overall alarm log and by counting the occurrences of following alarms in certain time intervals. The results can then be stored in a discrete deviation of probabilities: P (i) = p i, p i P = p 0, p 1,..., p m (9) P (i) = P (ID c, ID e, ɛ, t i ) (10) This deviation can be visualized by a histogram. Fig. 3 (a - dashed line) shows the bar chart of an ideal temporal dependency. The probability of the caused alarm occurring in the time interval [4 ɛ, 6 ɛ] is 1, which means that an alarm always follows an initiating alarm within a specific time 5ɛ and time deviation 4ɛ to 6ɛ. This detected dependency is significant, since there is an element of the amount of interval probabilities, which is higher than the pre-defined probability threshold P thr (in this case P thr = 0.8). Fig. 3 (b - bold line) shows the bar chart of another discrete deviation. Here, a nearly uniformly distributed alarm type with ID e is assumed. In contrast to Fig. 3 (a), it occurs that the time between alarms fits into several bins of the bar chart and, therefore, does not reach the pre-defined threshold. In this case no dependency is detected using the presented approach, because the calculated time dependency is too inaccurate. There is also the possibility that more than one element of the discrete probability distribution can exceed the given threshold. This can for example happen, if the time frame is large enough to detect the same temporal dependence twice. The bar chart would have 2 peaks at different time 1805
5 intervals. However, a tuple of alarms can only have one temporal dependency. This is the dependency with the lowest time interval t j. 3.4 Developed algorithm and computational complexity The developed concept was implemented by an algorithm. For each tuple of regarded alarms it iterates the alarm time series. If an alarm event with ID c is found, all following alarms with ID e that occur in the specified time window are investigated. They are then accumulated according to their time interval and placed in an array. Knowing the occurrences of alarms with ID c, the discrete probability distribution can be calculated. Assuming a medial amount of alarms with ID e to be investigated when an event with ID c occurs, the effort of computing a discrete probability deviation for a tuple of alarms is linear to the number of alarms in the time series. Furthermore, the number of tuples to be examined is quadratic to the amount of different unique alarms types in the time series. The overall computational complexity of the algorithm can then be estimated: complexity(n, Q) = O(N, Q 2 ) (11) N: Amount of alarms in the time series Q: Amount of unique alarms types to be investigated The computational complexity and the number of alarm types to analyze must be kept low. Thus only tuples with alarms that have a certain minimal occurrence in the time series are investigated. An appropriate approach to minimize the amount of alarms is to consider important event types, which are essential for related events, e.g. deleting visualization alarms or notification alarms without meaningful information about the manufacturing plant. The size of the time frame also affects the computational complexity linearly. The choice of the deviation has no effect on the computational effort. 4. EVALUATION AND DISCUSSION The developed concept was evaluated with eight different alarm logs from industry plants. The algorithm was applied on alarm logs from continuous (process control industry), discrete (manufacturing industry) and hybrid processes. Table 1 gives a summary of the characteristics of the alarm logs. The data have been collected over several days during the run-time of every plant. The shown alarms have strong variations in the number of investigated alarms, alarm types and mean times between the alarms. However, despite the regarded time series are from very different processes, the quality of the results is highly affected by the chosen algorithm parameters (e.g. t max, ɛ). During the evaluation, several experiences on the choice of these parameters were made. They are described later in this section. The results of the developed algorithm contain information about the time interval, deviation, probability and number of observations of each temporal dependency. For visualization purposes, the temporal dependencies can be illustrated as directed graphs. Fig. 4 shows an example of such a graph. The nodes contain alarm IDs. Alarms Fig. 4. Directed graphs illustrating temporal relationships found in an alarm time series. Excerpt of a bigger graph structure are connected with edges. At the edge the mean time of a temporal relationship between two alarms is shown. Fig. 4 shows an excerpt of a bigger graph structure, visualizing temporal dependencies in a plant. The graph shows only relationships with a minimum occurrences of 100 in the alarm log and an incidence probability of at least 0.8. The chosen maximal deviation ɛ is 10 seconds. The above mentioned graphs have been reviewed by plants operators which are experts on plants behavior. The experts pointed out that the algorithm is able to detect causalities between failures they did not know before or they detected only recently. For instance erroneous inputs have been made by the operator that affected the overall process and raised other alarms. This information can be used for a re-design of the operator interface, to avoid these erroneous inputs by the operator. Additionally the algorithm points out alarms that occur first and lead to plant shutdowns, e.g. failure of axes. These causal dependencies can be used to improve the intervention recommendations for the operator, to inform the operator earlier. Interrelations between logged alarms were discovered (e.g. incorrect inputs by the operator, which raise alarms due to failure of axes, which then leads to plant s shutdown) but due to the statistical approach, some random relationships were also recognized. Even if there are some significant alarm dependencies, there are still some major drawbacks. The detected time intervals between alarms in most alarm logs have strong variations. They can vary from seconds to hours as it is the case in nearly every analyzed process. The reason for that is the high non-determinism of the plant s behavior due to the operators behavior and several other influencing parameters (environment, produced product etc.). Additionally, the alarm log is not pre-processed and, hence, also alarms occurring during maintenance are stored in the alarm log, which distort the statistical alarm sequence recognition. Furthermore, the proposed approach expects input parameters, which are used for the Table 1. Analyzed alarm time series with industry segments. Legend: C: Continuous Processes, D: Discrete Processes, H: Hybrid Processes 1806
6 alarm sequence recognition. These parameters cannot be assumed to be static. For instance, a causal dependent failure between a pump and the filling level of a vessel depends on the volume of a tank and the volume/length of the pipe. Hence, proposed parameters have to be set a priori, e.g. by using engineering data. Hence, the temporal information gained from this algorithm must be combined with knowledge about the particular processes. For example, a process flow model can be connected with the temporal dependencies to discover relationships in the occurrences of abnormal process parameters. This can be used to derive changes in the plant s functionality to avoid these erroneous situations. Furthermore the discovered dependencies can be used to predict soon arising alarms at certain times. Alarms that occur in direct temporal relations can also be removed from the alarm system to reduce operators workload. The interviewed operators mentioned that alarms are raised during downtime of plant sections, i.e.during maintenance. These alarms are not disabled and, hence, are illustrated to the operator. These alarms do not include important information and may hide important alarms. Unfortunately, these alarms are still recorded and complicate the recognition of dependencies. Further challenges are longer time intervals, where huge delays between cause and effects can lead to high deviations in the alarm event times. Hence, temporal relationships cannot be detected anymore in longer time intervals. 5. CONCLUSION AND OUTLOOK This paper presents an algorithm to find causal dependencies of alarm within alarm logs, recorded during the run-time of industrial plants. A temporal dependencies are determined by analyzing the temporal dependency between two alarms, which occur several times in the alarm log, based on statistical approaches. In this contribution important parameters for the analysis are defined. The algorithm can find relationships even in longer time intervals by regarding multiple time intervals at once. For the evaluation an algorithm with linear computational effort has been developed and applied on eight different alarm logs from different industry segments. The results pointed out causal dependent alarms, e.g. based on erroneous inputs of operators or based on the process/product flow. The benefits and major drawback of parameter estimation for the algorithm are discussed. The gained information can be used to make alarm management systems more effective or to discover dependencies in the erroneous behavior of a plant. This can be used to reduce operators workload, to draw further conclusions about the erroneous behavior of the plant processes or the configuration of the alarm management configuration. In addition, the temporal dependencies can be used to forecast several critical alarm events before they occur. This knowledge can be used to avoid those events and thus improve the performance of the whole plant process. Due to the drawback of the algorithm, future research will focus on combining further process information, like plants layout and additional parameters about plants operation mode, to improve the results of the proposed algorithm. REFERENCES Ahmed, K., Izadi, I., Chen, T., Joe, D., and Burton, T. (2013). Similarity Analysis of Industrial Alarm Flood Data. IEEE Transactions on Automation Science and Engineering, 10(2), Boghey, R. and Singh, S. (2013). Sequential Pattern Mining: A Survey on Approaches. In International Conference on Communication Systems and Network Technologies (CSNT), Bouandas, K. and Osmani, A. (2007). Mining Association Rules in Temporal Sequences. In Symposium on Computational Intelligence and Data Mining, EEMUA (2013). Alarm systems a guide to design, management and procurement. EEMUA publication No. 191, 3rd edition. Esling, P. and Agon, C. (2012). Time-series data mining. ACM Computing Surveys, 45(1), Folmer, J., Pantförder, D., and Vogel-Heuser, B. (2011). An analytical alarm flood reduction to reduce operator s workload. In J. Jacko (ed.), Human-Computer Interaction. Users and Applications, volume 6764 of Lecture Notes in Computer Science, Springer Berlin Heidelberg. Folmer, J. and Vogel-Heuser, B. (2012). Computing dependent industrial alarms for alarm flood reduction. In 9th IEEE International Multi-Conference on Systems, Signals and Devices (SSD), 1 6. Fu, T.c. (2011). A review on time series data mining. Engineering Applications of Artificial Intelligence, 24(1), Höppner, F. and Klawonn, F. (2002). Finding informative rules in interval sequences. Intelligent Data Analysis, 6(3), IEC (2013). Representation of process control engineering - request in p&i diagrams and data exchange between p&id tools and pce-cae tools. Li, Y., Ning, P., Wang, X.S., and Jajodia, S. (2001). Discovering calendar-based temporal association rules. In Temporal Representation and Reasoning, Proceedings. Eighth International Symposium on, Mannila, H., Toivonen, H., and Verkamo, A.I. (1995). Discovering frequent episodes in sequences Extended abstract. In 1st Conference on Knowledge Discovery and Data Mining. Pantforder, D. and Vogel-Heuser, B. (2009). Benefit and evaluation of interactive 3d process data visualization in operator training of plant manufacturing industry. In Systems, Man and Cybernetics, SMC IEEE International Conference on, Schluter, T. and Conrad, S. (2011). About the analysis of time series with temporal association rule mining. In IEEE Symposium on Computational Intelligence and Data Mining, Thuan, N.D., Toan, N.G., and Tuan, N.L.V. (2012). An Approach Mining Cyclic Association Rules in E-Commerce. In 15th International Conference on Network-Based Information Systems, Zhao, Q. and Bhowmick, S.S. (2003). Sequential pattern mining: A survey. ITechnical Report, Nayang Technological University Singapore,
Intrusion Detection System: Facts, Challenges and Futures. By Gina Tjhai 13 th March 2007 Network Research Group
 Intrusion Detection System: Facts, Challenges and Futures By Gina Tjhai 13 th March 2007 Network Research Group 1 Overview Introduction Challenges of current IDS Potential solutions Alarm Correlation Existing
Intrusion Detection System: Facts, Challenges and Futures By Gina Tjhai 13 th March 2007 Network Research Group 1 Overview Introduction Challenges of current IDS Potential solutions Alarm Correlation Existing
Methodology and Application of Pattern Mining in Multiple Alarm Flood Sequences
 Preprints of the 9th International Symposium on Advanced Control of Chemical Processes The International Federation of Automatic Control TuM4.4 Methodology and Application of Pattern Mining in Multiple
Preprints of the 9th International Symposium on Advanced Control of Chemical Processes The International Federation of Automatic Control TuM4.4 Methodology and Application of Pattern Mining in Multiple
Reduction of alerts in automated systems based on a combined analysis of process connectivity and alarm logs
 Ian David Lockhart Bogle and Michael Fairweather (Editors), Proceedings of the 22nd European Symposium on Computer Aided Process Engineering, 17-20 June 2012, London. 2012 Elsevier B.V. All rights reserved.
Ian David Lockhart Bogle and Michael Fairweather (Editors), Proceedings of the 22nd European Symposium on Computer Aided Process Engineering, 17-20 June 2012, London. 2012 Elsevier B.V. All rights reserved.
To appear in the IEEE/IFIP 1996 Network Operations and Management. Symposium (NOMS'96), Kyoto, Japan, April TASA: Telecommunication
 To appear in the IEEE/IFIP 1996 Operations and Management Symposium (NOMS'96), Kyoto, Japan, April 1996. TASA: Telecommunication Alarm Sequence Analyzer or How to enjoy faults in your network Kimmo Hatonen,
To appear in the IEEE/IFIP 1996 Operations and Management Symposium (NOMS'96), Kyoto, Japan, April 1996. TASA: Telecommunication Alarm Sequence Analyzer or How to enjoy faults in your network Kimmo Hatonen,
Unifying Alarms and Operating Envelopes for the Achievement of KPI s and Business Objectives
 Geometric Process Control Unifying Alarms and Operating Envelopes for the Achievement of KPI s and Business Objectives Robin Brooks, Alan Mahoney, John Wilson, Na Zhao, Process Plant Computing Ltd (PPCL),
Geometric Process Control Unifying Alarms and Operating Envelopes for the Achievement of KPI s and Business Objectives Robin Brooks, Alan Mahoney, John Wilson, Na Zhao, Process Plant Computing Ltd (PPCL),
Effective Alarm Management for Dynamic and Vessel Control Systems
 DYNAMIC POSITIONING CONFERENCE October 12-13, 2010 OPERATIONS SESSION Effective Alarm Management for Dynamic and Vessel Control Systems By Steve Savoy Ensco Offshore Company 1. Introduction Marine control
DYNAMIC POSITIONING CONFERENCE October 12-13, 2010 OPERATIONS SESSION Effective Alarm Management for Dynamic and Vessel Control Systems By Steve Savoy Ensco Offshore Company 1. Introduction Marine control
doi: / _57(
 doi: 10.1007/978-3-319-0618-9_57(http://doi.org/10.1007/978-3-319-0618-9_57) Modelling of a Business Process for Alarm Management Lifecycle in Chemical Industries K. Takeda 1,*, T. Hamaguchi, N. Kimura
doi: 10.1007/978-3-319-0618-9_57(http://doi.org/10.1007/978-3-319-0618-9_57) Modelling of a Business Process for Alarm Management Lifecycle in Chemical Industries K. Takeda 1,*, T. Hamaguchi, N. Kimura
Alarm Analysis with Fuzzy Logic and Multilevel Flow Models
 Alarm Analysis with Fuzzy Logic and Multilevel Flow Models Fredrik Dahlstrand Department of Information Technology Lund Institute of Technology Box 118, SE-221 00 Lund, Sweden Phone: +46 46 222 95 10 Fax
Alarm Analysis with Fuzzy Logic and Multilevel Flow Models Fredrik Dahlstrand Department of Information Technology Lund Institute of Technology Box 118, SE-221 00 Lund, Sweden Phone: +46 46 222 95 10 Fax
Alarm Management for SCADA control rooms
 Whitepaper Alarm Management for SCADA control rooms Definition of the term alarm The concept of alarms (French for a l arme which means spring to arms ) is very old and originates from the military concept
Whitepaper Alarm Management for SCADA control rooms Definition of the term alarm The concept of alarms (French for a l arme which means spring to arms ) is very old and originates from the military concept
SIL DETERMINATION AND PROBLEMS WITH THE APPLICATION OF LOPA
 SIL DETERMINATION AND PROBLEMS WITH THE APPLICATION OF LOPA Alan G King Hazard & Reliability Specialist, ABB Engineering Services, Billingham, Cleveland UK. TS23 4YS For a number of years, industry has
SIL DETERMINATION AND PROBLEMS WITH THE APPLICATION OF LOPA Alan G King Hazard & Reliability Specialist, ABB Engineering Services, Billingham, Cleveland UK. TS23 4YS For a number of years, industry has
Monitor Alarms and Events
 This chapter contains the following topics: What Are Alarms and Events?, page 1 How are Alarms and Events Created and Updated?, page 2 Find and View Alarms, page 3 Set Alarm and Event Management Preferences,
This chapter contains the following topics: What Are Alarms and Events?, page 1 How are Alarms and Events Created and Updated?, page 2 Find and View Alarms, page 3 Set Alarm and Event Management Preferences,
Research on Evaluation of Fire Detection Algorithms
 Research on Evaluation of Fire Detection Algorithms JIAN LI 1,2, WENHUI DONG 1, ZHIBIN MEI 1, and ZHUOFU WANG 1 1 Shenyang Fire Research Institute Ministry of Public Security China, 110031 2 Dalian University
Research on Evaluation of Fire Detection Algorithms JIAN LI 1,2, WENHUI DONG 1, ZHIBIN MEI 1, and ZHUOFU WANG 1 1 Shenyang Fire Research Institute Ministry of Public Security China, 110031 2 Dalian University
An Alarm Correlation Algorithm for Network Management Based on Root Cause Analysis
 An Alarm Correlation Algorithm for Network Management Based on Root Cause Analysis Dae Sun Kim*, Hiroyuki Shinbo*, Hidetoshi Yokota* *KDDI R&D Laboratories, Inc. Fujimino, Saitama, Japan da-kim@kddilabs.jp,
An Alarm Correlation Algorithm for Network Management Based on Root Cause Analysis Dae Sun Kim*, Hiroyuki Shinbo*, Hidetoshi Yokota* *KDDI R&D Laboratories, Inc. Fujimino, Saitama, Japan da-kim@kddilabs.jp,
2012 Honeywell Pacific Users Group. Sus tain.ability.
 2012 Honeywell Pacific Users Group Sus tain.ability. 1 2012 Honeywell Pacific Users Group Sus tain.ability. Nico Oosthuizen Effective Alarm and Operations Management 2 Topics Overview What is the problem?
2012 Honeywell Pacific Users Group Sus tain.ability. 1 2012 Honeywell Pacific Users Group Sus tain.ability. Nico Oosthuizen Effective Alarm and Operations Management 2 Topics Overview What is the problem?
Getting Started with Live Exceptions
 Getting Started with Live Exceptions Live Exceptions provides alarm reporting by identifying problems that include delay, errors, failures, security, or configuration changes. The Live Exceptions Browser
Getting Started with Live Exceptions Live Exceptions provides alarm reporting by identifying problems that include delay, errors, failures, security, or configuration changes. The Live Exceptions Browser
Computer Modelling and Simulation of a Smart Water Heater
 Computer Modelling and Simulation of a Smart Water Heater Maria Kathleen Ellul University of Malta ellul_maria@yahoo.com Adrian Muscat University of Malta adrian.muscat@um.edu.mt Abstract A computational
Computer Modelling and Simulation of a Smart Water Heater Maria Kathleen Ellul University of Malta ellul_maria@yahoo.com Adrian Muscat University of Malta adrian.muscat@um.edu.mt Abstract A computational
Procedia - Social and Behavioral Sciences 195 ( 2015 ) World Conference on Technology, Innovation and Entrepreneurship
 Available online at www.sciencedirect.com ScienceDirect Procedia - Social and Behavioral Sciences 195 ( 2015 ) 1846 1850 World Conference on Technology, Innovation and Entrepreneurship Fire Detection Systems
Available online at www.sciencedirect.com ScienceDirect Procedia - Social and Behavioral Sciences 195 ( 2015 ) 1846 1850 World Conference on Technology, Innovation and Entrepreneurship Fire Detection Systems
Human Performance Models for Response to Alarm Notifications in the Process Industries: An Industrial Case Study
 Human Performance Models for Response to Alarm Notifications in the Process Industries: An Industrial Case Study Dal Vernon C. Reising Joshua L. Downs Danni Bayn ACS Advanced Technology Department of Psychology
Human Performance Models for Response to Alarm Notifications in the Process Industries: An Industrial Case Study Dal Vernon C. Reising Joshua L. Downs Danni Bayn ACS Advanced Technology Department of Psychology
Brine Generation Study
 DOE/WIPP 00-2000 Brine Generation Study April 2000 Waste Isolation Pilot Plant Carlsbad, New Mexico Processing and final preparation of this report was performed by the Waste Isolation Pilot Plant Management
DOE/WIPP 00-2000 Brine Generation Study April 2000 Waste Isolation Pilot Plant Carlsbad, New Mexico Processing and final preparation of this report was performed by the Waste Isolation Pilot Plant Management
[ [ ADMIN PANEL USER GUIDE
 [ [ ADMIN PANEL USER GUIDE ADMIN PANEL USER GUIDE 2 Contents Logging In & Systems Overview 3 System Details 5 Analytics 6 View Alarms 8 Manage Alarms 9 Create Alarms 10 Device Reporting Alarm 11 Monthly
[ [ ADMIN PANEL USER GUIDE ADMIN PANEL USER GUIDE 2 Contents Logging In & Systems Overview 3 System Details 5 Analytics 6 View Alarms 8 Manage Alarms 9 Create Alarms 10 Device Reporting Alarm 11 Monthly
FLIGHT UNLOADING IN ROTARY SUGAR DRYERS. P.F. BRITTON, P.A. SCHNEIDER and M.E. SHEEHAN. James Cook University
 FLIGHT UNLOADING IN ROTARY SUGAR DRYERS By P.F. BRITTON, P.A. SCHNEIDER and M.E. SHEEHAN James Cook University Paul.Britton@jcu.edu.au, Phil.Schnieder@jcu.edu.au, Madoc.Sheehan@jcu.edu.au Keywords: Drying,
FLIGHT UNLOADING IN ROTARY SUGAR DRYERS By P.F. BRITTON, P.A. SCHNEIDER and M.E. SHEEHAN James Cook University Paul.Britton@jcu.edu.au, Phil.Schnieder@jcu.edu.au, Madoc.Sheehan@jcu.edu.au Keywords: Drying,
A Forest Fire Warning Method Based on Fire Dangerous Rating Dan Wang 1, a, Lei Xu 1, b*, Yuanyuan Zhou 1, c, Zhifu Gao 1, d
 International Conference on Applied Science and Engineering Innovation (ASEI 2015) A Forest Fire Warning Method Based on Fire Dangerous Rating Dan Wang 1, a, Lei Xu 1, b*, Yuanyuan Zhou 1, c, Zhifu Gao
International Conference on Applied Science and Engineering Innovation (ASEI 2015) A Forest Fire Warning Method Based on Fire Dangerous Rating Dan Wang 1, a, Lei Xu 1, b*, Yuanyuan Zhou 1, c, Zhifu Gao
MODELLING AND OPTIMIZATION OF DIRECT EXPANSION AIR CONDITIONING SYSTEM FOR COMMERCIAL BUILDING ENERGY SAVING
 MODELLING AND OPTIMIZATION OF DIRECT EXPANSION AIR CONDITIONING SYSTEM FOR COMMERCIAL BUILDING ENERGY SAVING V. Vakiloroaya*, J.G. Zhu, and Q.P. Ha School of Electrical, Mechanical and Mechatronic Systems,
MODELLING AND OPTIMIZATION OF DIRECT EXPANSION AIR CONDITIONING SYSTEM FOR COMMERCIAL BUILDING ENERGY SAVING V. Vakiloroaya*, J.G. Zhu, and Q.P. Ha School of Electrical, Mechanical and Mechatronic Systems,
Ovation Alarm Management System
 Ovation Alarm Management System Features Multiple types of fully configurable, easy-tounderstand alarm displays Convenient access to past alarms, returns and state changes Simplified ability to acknowledge,
Ovation Alarm Management System Features Multiple types of fully configurable, easy-tounderstand alarm displays Convenient access to past alarms, returns and state changes Simplified ability to acknowledge,
Alarm and Event Analysis for Batch Process Improvement
 Presented at the World Batch Forum North American Conference Atlantic City, NJ April 2000 107 S. Southgate Drive Chandler, Arizona 85226-3222 480-893-8803 Fax 480-893-7775 E-mail: info@wbf.org www.wbf.org
Presented at the World Batch Forum North American Conference Atlantic City, NJ April 2000 107 S. Southgate Drive Chandler, Arizona 85226-3222 480-893-8803 Fax 480-893-7775 E-mail: info@wbf.org www.wbf.org
Lesson 25 Analysis Of Complete Vapour Compression Refrigeration Systems
 Lesson 25 Analysis Of Complete Vapour Compression Refrigeration Systems Version 1 ME, IIT Kharagpur 1 The specific objectives of this lecture are to: 1. Importance of complete vapour compression refrigeration
Lesson 25 Analysis Of Complete Vapour Compression Refrigeration Systems Version 1 ME, IIT Kharagpur 1 The specific objectives of this lecture are to: 1. Importance of complete vapour compression refrigeration
An improved Algorithm of Generating Network Intrusion Detector Li Ma 1, a, Yan Chen 1, b
 An improved Algorithm of Generating Network Intrusion Detector Li Ma 1, a, Yan Chen 1, b 1 Department of Information Engineering Guilin University of Aerospace Technology, Guilin China a E-mail: woshiml@sina.com,
An improved Algorithm of Generating Network Intrusion Detector Li Ma 1, a, Yan Chen 1, b 1 Department of Information Engineering Guilin University of Aerospace Technology, Guilin China a E-mail: woshiml@sina.com,
Critical Condition Management on a Corporate Scale. Lyondell Is a Major Global Chemical Company
 Critical Condition Management on a Corporate Scale Lothar Lang Consulting Engineer - CSEE Lyondell Chemical Company Lyondell Is a Major Global Chemical Company A global leader in the manufacture of chemicals
Critical Condition Management on a Corporate Scale Lothar Lang Consulting Engineer - CSEE Lyondell Chemical Company Lyondell Is a Major Global Chemical Company A global leader in the manufacture of chemicals
Benefits of Enhanced Event Analysis in. Mark Miller
 Benefits of Enhanced Event Analysis in Data Center OTDR Testing Mark Miller Dr. Fang Xu AFL/Noyes Test & Inspection Overview Challenges Topics Techniques and Improvements Benefits of enhanced event analysis
Benefits of Enhanced Event Analysis in Data Center OTDR Testing Mark Miller Dr. Fang Xu AFL/Noyes Test & Inspection Overview Challenges Topics Techniques and Improvements Benefits of enhanced event analysis
Video Analytics Technology for Disaster Management and Security Solutions
 FEATURED ARTICLES Disaster Management and Security Solutions for a Safe and Secure Way of Life Video Analytics Technology for Disaster Management and Security Solutions The rising demand for safety and
FEATURED ARTICLES Disaster Management and Security Solutions for a Safe and Secure Way of Life Video Analytics Technology for Disaster Management and Security Solutions The rising demand for safety and
How to Use Fire Risk Assessment Tools to Evaluate Performance Based Designs
 How to Use Fire Risk Assessment Tools to Evaluate Performance Based Designs 1 ABSTRACT Noureddine Benichou and Ahmed H. Kashef * Institute for Research in Construction National Research Council of Canada
How to Use Fire Risk Assessment Tools to Evaluate Performance Based Designs 1 ABSTRACT Noureddine Benichou and Ahmed H. Kashef * Institute for Research in Construction National Research Council of Canada
AN ANALYSIS OF THE PERFORMANCE OF RESIDENTIAL SMOKE DETECTION TECHNOLOGIES UTILIZING THE CONCEPT OF RELATIVE TIME
 AN ANALYSIS OF THE PERFORMANCE OF RESIDENTIAL SMOKE DETECTION TECHNOLOGIES UTILIZING THE CONCEPT OF RELATIVE TIME Elizabeth L. Milarcik, Stephen M. Olenick*, and Richard J. Roby Combustion Science & Engineering,
AN ANALYSIS OF THE PERFORMANCE OF RESIDENTIAL SMOKE DETECTION TECHNOLOGIES UTILIZING THE CONCEPT OF RELATIVE TIME Elizabeth L. Milarcik, Stephen M. Olenick*, and Richard J. Roby Combustion Science & Engineering,
Cool, calm and collected No cause for alarm on the Grane oil rig
 The control room on an offshore oil platform can quickly become a scene of frenzied activity in an emergency: Alarms scream, warning lights blaze and screens flash. Operators are inundated with information.
The control room on an offshore oil platform can quickly become a scene of frenzied activity in an emergency: Alarms scream, warning lights blaze and screens flash. Operators are inundated with information.
Understanding total measurement uncertainty in power meters and detectors
 Understanding total measurement uncertainty in power meters and detectors Jay Jeong, MKS Instruments. Inc. INTRODUCTION It is important that users of calibrated power meters and detectors understand and
Understanding total measurement uncertainty in power meters and detectors Jay Jeong, MKS Instruments. Inc. INTRODUCTION It is important that users of calibrated power meters and detectors understand and
Oracle Real Application Clusters (RAC) 12c Release 2 What s Next?
 Oracle Real Application Clusters (RAC) 12c Release 2 What s Next? Markus Michalewicz Oracle Redwood Shores, CA, USA Keywords: RAC, Cloud, Private Cloud, Storage, Network, Development, Market Trends, Future
Oracle Real Application Clusters (RAC) 12c Release 2 What s Next? Markus Michalewicz Oracle Redwood Shores, CA, USA Keywords: RAC, Cloud, Private Cloud, Storage, Network, Development, Market Trends, Future
Monitor Alarms and Events
 What Are Alarms and Events?, page 1 How are Alarms and Events Created and Updated?, page 2 Which Events Are Supported?, page 5 Set Alarm and Event Management Preferences, page 5 Interpret Event and Alarm
What Are Alarms and Events?, page 1 How are Alarms and Events Created and Updated?, page 2 Which Events Are Supported?, page 5 Set Alarm and Event Management Preferences, page 5 Interpret Event and Alarm
White Paper: CCPS Process Safety Metrics Review Considerations from an ASM Perspective
 White Paper: CCPS Process Safety Metrics Review Considerations from an ASM Perspective 2008 Mary Kay O Connor Process Safety Center International Symposium 28 October 2008 Doug Metzger: Honeywell, ASM
White Paper: CCPS Process Safety Metrics Review Considerations from an ASM Perspective 2008 Mary Kay O Connor Process Safety Center International Symposium 28 October 2008 Doug Metzger: Honeywell, ASM
Diagnostics with fieldbus
 2002 Emerson Process Management. All rights reserved. View this and other courses online at www.plantwebuniversity.com. Fieldbus 105 Diagnostics with fieldbus Overview More than device maintenance Equipment
2002 Emerson Process Management. All rights reserved. View this and other courses online at www.plantwebuniversity.com. Fieldbus 105 Diagnostics with fieldbus Overview More than device maintenance Equipment
Video Smoke Detection using Deep Domain Adaptation Enhanced with Synthetic Smoke Images
 Video Smoke Detection using Deep Domain Adaptation Enhanced with Synthetic Smoke Images Gao Xu, Qixing Zhang, Gaohua Lin, Jinjun Wang, Yongming Zhang State Key Laboratory of Fire Science, University of
Video Smoke Detection using Deep Domain Adaptation Enhanced with Synthetic Smoke Images Gao Xu, Qixing Zhang, Gaohua Lin, Jinjun Wang, Yongming Zhang State Key Laboratory of Fire Science, University of
Computers and Chemical Engineering
 Computers and Chemical Engineering 8 (2) 89 98 Contents lists available at ScienceDirect Computers and Chemical Engineering j ourna l ho me pa g e: www.elsevier.com/locate/compchemeng A new method to detect
Computers and Chemical Engineering 8 (2) 89 98 Contents lists available at ScienceDirect Computers and Chemical Engineering j ourna l ho me pa g e: www.elsevier.com/locate/compchemeng A new method to detect
Study and Design Considerations of HRSG Evaporators in Fast Start Combined Cycle Plants. Govind Rengarajan, P.E.CEM, Dan Taylor
 Study and Design Considerations of HRSG Evaporators in Fast Start Combined Cycle Plants Govind Rengarajan, P.E.CEM, Dan Taylor CMI Energy, Erie PA 1651 Bernd Pankow P.E, Pankow Engineering Abstract Combined
Study and Design Considerations of HRSG Evaporators in Fast Start Combined Cycle Plants Govind Rengarajan, P.E.CEM, Dan Taylor CMI Energy, Erie PA 1651 Bernd Pankow P.E, Pankow Engineering Abstract Combined
Dynamic Simulation of Double Pipe Heat Exchanger using MATLAB simulink
 Dynamic Simulation of Double Pipe Heat Exchanger using MATLAB simulink 1 Asoka R.G, 2 Aishwarya N, 3 Rajasekar S and 4 Meyyappan N 1234 Department of Chemical Engineering Sri Venkateswara College of Engineering,
Dynamic Simulation of Double Pipe Heat Exchanger using MATLAB simulink 1 Asoka R.G, 2 Aishwarya N, 3 Rajasekar S and 4 Meyyappan N 1234 Department of Chemical Engineering Sri Venkateswara College of Engineering,
Simplex Panel Interface Guide
 Simplex Panel Interface Guide February 2016 SATEON Software Integrations Simplex Panel Interface Guide Issue 1.0, released February 2016 Disclaimer Copyright 2016, Grosvenor Technology. All rights reserved.
Simplex Panel Interface Guide February 2016 SATEON Software Integrations Simplex Panel Interface Guide Issue 1.0, released February 2016 Disclaimer Copyright 2016, Grosvenor Technology. All rights reserved.
ABB Ability System 800xA Alarm Management
 ABB Ability System 800xA Alarm Management Effective detection, notification, analysis and corrective action of abnormal situations. When an alarm sounds in a process controlled by ABB s System 800xA, operators
ABB Ability System 800xA Alarm Management Effective detection, notification, analysis and corrective action of abnormal situations. When an alarm sounds in a process controlled by ABB s System 800xA, operators
Procidia iware AlarmWorX32. AlarmWorX32 Viewer January 2010
 Procidia iware AlarmWorX32 AlarmWorX32 Viewer Siemens Protection AG 2008. notice All / Copyright rights reserved. notice Introduction / Contents Procidia iware is an operator interface software designed
Procidia iware AlarmWorX32 AlarmWorX32 Viewer Siemens Protection AG 2008. notice All / Copyright rights reserved. notice Introduction / Contents Procidia iware is an operator interface software designed
Proxemic Interactions in Ubiquitous Computing Ecologies
 Proxemic Interactions in Ubiquitous Computing Ecologies Figure 1. People, digital devices, and non-digital physical objects in a ubiquitous computing ecology. Nicolai Marquardt Interactions Lab, University
Proxemic Interactions in Ubiquitous Computing Ecologies Figure 1. People, digital devices, and non-digital physical objects in a ubiquitous computing ecology. Nicolai Marquardt Interactions Lab, University
Samsung SDS BMS Ver.2.0. Technical Specification
 Samsung SDS BMS Ver.2.0 Technical Specification Technical Specifications All rights and title, including all intellectual property rights to Samsung SDS BMS" is retained by Samsung SDS Co, Ltd. ("SDS"),
Samsung SDS BMS Ver.2.0 Technical Specification Technical Specifications All rights and title, including all intellectual property rights to Samsung SDS BMS" is retained by Samsung SDS Co, Ltd. ("SDS"),
Simulation study of evacuation in high-rise buildings
 Available online at www.sciencedirect.com ScienceDirect Transportation Research Procedia 00 (2014) 000 000 www.elsevier.com/locate/procedia The Conference in Pedestrian and Evacuation Dynamics 2014 (PED2014)
Available online at www.sciencedirect.com ScienceDirect Transportation Research Procedia 00 (2014) 000 000 www.elsevier.com/locate/procedia The Conference in Pedestrian and Evacuation Dynamics 2014 (PED2014)
Statistical cluster analysis and visualisation for alarm management configuration. Butters, T D and Güttel, S and Shapiro, J L and Sharpe, T J
 Statistical cluster analysis and visualisation for alarm management configuration Butters, T D and Güttel, S and Shapiro, J L and Sharpe, T J 2014 MIMS EPrint: 2014.51 Manchester Institute for Mathematical
Statistical cluster analysis and visualisation for alarm management configuration Butters, T D and Güttel, S and Shapiro, J L and Sharpe, T J 2014 MIMS EPrint: 2014.51 Manchester Institute for Mathematical
Advance Warning Flasher System at High Speed
 Evaluation of Integrated t Platoon-Priority Pi it and Advance Warning Flasher System at High Speed Intersections Dr. Henry Liu Sundeep Bhimireddy Department of Civil Engineering University of Minnesota,
Evaluation of Integrated t Platoon-Priority Pi it and Advance Warning Flasher System at High Speed Intersections Dr. Henry Liu Sundeep Bhimireddy Department of Civil Engineering University of Minnesota,
presentations the week of the final exams. Anyone who misses the appointment will receive a grade of zero.
 CS 116 Section 4 PROJECT Spring 2016 Grade: Up to 12 points. Rules: To be worked on individually. Must be presented to the instructor in person in order to be graded. Similar projects will both receive
CS 116 Section 4 PROJECT Spring 2016 Grade: Up to 12 points. Rules: To be worked on individually. Must be presented to the instructor in person in order to be graded. Similar projects will both receive
Design and Development of Industrial Pollution Monitoring System using LabVIEW and GSM
 Design and Development of Industrial Pollution Monitoring System using LabVIEW and GSM Dr. Channappa Bhyri¹, Eliyaz Ahmed² 2 Student, Dept. of Electronics and Instrumentation, PDACE, Kalaburgi, Karnataka,
Design and Development of Industrial Pollution Monitoring System using LabVIEW and GSM Dr. Channappa Bhyri¹, Eliyaz Ahmed² 2 Student, Dept. of Electronics and Instrumentation, PDACE, Kalaburgi, Karnataka,
Battery Performance Alert: A TOOL FOR IMPROVED PATIENT MANAGEMENT FOR DEVICES UNDER BATTERY ADVISORY
 Battery Performance Alert: A TOOL FOR IMPROVED PATIENT MANAGEMENT FOR S UNDER BATTERY ADVISORY VERSION 1.0 AUGUST 8, 2017 Abstract: BACKGROUND: In October 2016, St. Jude Medical issued an advisory on a
Battery Performance Alert: A TOOL FOR IMPROVED PATIENT MANAGEMENT FOR S UNDER BATTERY ADVISORY VERSION 1.0 AUGUST 8, 2017 Abstract: BACKGROUND: In October 2016, St. Jude Medical issued an advisory on a
When Precision is not good enough
 When Precision is not good enough Andrew Kelley XACT PCB Ltd North Shields, UK Abstract As PCB designs become ever more complex with more sequential build up layers, tighter annular ring designs and broader
When Precision is not good enough Andrew Kelley XACT PCB Ltd North Shields, UK Abstract As PCB designs become ever more complex with more sequential build up layers, tighter annular ring designs and broader
Battery Performance Alert
 Battery Performance Alert A TOOL FOR IMPROVED PATIENT MANAGEMENT FOR S UNDER BATTERY ADVISORY VERSION 2.0 Abstract BACKGROUND: In October 2016, St. Jude Medical (now Abbott) issued an advisory on a family
Battery Performance Alert A TOOL FOR IMPROVED PATIENT MANAGEMENT FOR S UNDER BATTERY ADVISORY VERSION 2.0 Abstract BACKGROUND: In October 2016, St. Jude Medical (now Abbott) issued an advisory on a family
Table of Contents PART I: The History and Current Status of the Industrial HMI PART II: Fundamentals of HMI Design and Best Practices
 Table of Contents PART I: The History and Current Status of the Industrial HMI We begin with the origin and evolution of the industrial HMI. The positive and negative issues posed by the introduction of
Table of Contents PART I: The History and Current Status of the Industrial HMI We begin with the origin and evolution of the industrial HMI. The positive and negative issues posed by the introduction of
PM-ANALYZE. Overview 1. System Configuration 2. Operation 3. Analysis of Alarms and process values. User Interface 4
 Overview 1 System Configuration 2 Operation 3 Analysis of Alarms and process values User Interface 4 Version 8 Configuration 5 Edition: 04/04/2017 Table of Contents Contents 1 Overview... 1-1 1.1 General
Overview 1 System Configuration 2 Operation 3 Analysis of Alarms and process values User Interface 4 Version 8 Configuration 5 Edition: 04/04/2017 Table of Contents Contents 1 Overview... 1-1 1.1 General
Fire Dynamics Simulation and Evacuation for a Large Shopping Center (Mall), Part II, Evacuation Scenarios
 American Journal of Energy Engineering 2015; 3(4-1): 72-78 Published online June 12, 2015 (http://www.sciencepublishinggroup.com/j/ajee) doi: 10.11648/j.ajee.s.2015030401.15 ISSN: 2329-1648 (Print); ISSN:
American Journal of Energy Engineering 2015; 3(4-1): 72-78 Published online June 12, 2015 (http://www.sciencepublishinggroup.com/j/ajee) doi: 10.11648/j.ajee.s.2015030401.15 ISSN: 2329-1648 (Print); ISSN:
False Alarm Suppression in Early Prediction of Cardiac Arrhythmia
 IEEE International Conference on Bioinformatics & Bioengineering 2015 False Alarm Suppression in Early Prediction of Cardiac Arrhythmia Shoumik Roychoudhury, Mohamed F. Ghalwash, Zoran Obradovic Presented
IEEE International Conference on Bioinformatics & Bioengineering 2015 False Alarm Suppression in Early Prediction of Cardiac Arrhythmia Shoumik Roychoudhury, Mohamed F. Ghalwash, Zoran Obradovic Presented
Advanced Digital Signal Processing Part 4: DFT and FFT
 Advanced Digital Signal Processing Part 4: DFT and FFT Gerhard Schmidt Christian-Albrechts-Universität zu Kiel Faculty of Engineering Institute of Electrical and Information Engineering Digital Signal
Advanced Digital Signal Processing Part 4: DFT and FFT Gerhard Schmidt Christian-Albrechts-Universität zu Kiel Faculty of Engineering Institute of Electrical and Information Engineering Digital Signal
Making the Most of Alarms
 Making the Most of Alarms Leverage the alarm management features of MPA to address network performance problems more effectively. Blueprint to Leverage Alarms and Alerts Using Mitel Performance Analytics
Making the Most of Alarms Leverage the alarm management features of MPA to address network performance problems more effectively. Blueprint to Leverage Alarms and Alerts Using Mitel Performance Analytics
Sensor Cloud User Manual
 Sensor Cloud User Manual Table of Contents DEVICES TAB 4 1. DEVICE LIST 4 2. EXPAND ALL 4 3. EXPAND 4 4. STATUS 4 5. DEVICE 4 6. NAME 5 7. MONITORING INTERVAL 5 8. LAST ACTIVITY 5 9. VIEW 5 10. DELETE
Sensor Cloud User Manual Table of Contents DEVICES TAB 4 1. DEVICE LIST 4 2. EXPAND ALL 4 3. EXPAND 4 4. STATUS 4 5. DEVICE 4 6. NAME 5 7. MONITORING INTERVAL 5 8. LAST ACTIVITY 5 9. VIEW 5 10. DELETE
Improving Control of Dual-Duct Single-Fan Variable Air Volume Systems
 Improving Control of Dual-Duct Single-Fan Variable Air Volume Systems Guanghua Wei, P.E. Joe Martinez Tom Minihan Assistant Research Engineer Research Engineering Associate Graduate Student Tim Brundidge
Improving Control of Dual-Duct Single-Fan Variable Air Volume Systems Guanghua Wei, P.E. Joe Martinez Tom Minihan Assistant Research Engineer Research Engineering Associate Graduate Student Tim Brundidge
for family composition, time allocation of people, ownership and specification of home appliances. This paper first presents the simulation procedure
 Validation of an Energy Demand Model of Residential Buildings Yohei Yamaguchi 1*, Yoshiyuki Shimoda 1 1 Graduate School of Engineering Osaka University, S4 Building, 2-1 Yamadaoka, Suita, Osaka, 565-871,
Validation of an Energy Demand Model of Residential Buildings Yohei Yamaguchi 1*, Yoshiyuki Shimoda 1 1 Graduate School of Engineering Osaka University, S4 Building, 2-1 Yamadaoka, Suita, Osaka, 565-871,
INDOOR HUMAN THERMAL COMFORT OPTIMAL CONTROL WITH DESICCANT WHEEL COOLING SYSTEM
 Available online at www.sciencedirect.com ScienceDirect Energy Procedia 61 (2014 ) 882 886 The 6 th International Conference on Applied Energy ICAE2014 INDOOR HUMAN THERMAL COMFORT OPTIMAL CONTROL WITH
Available online at www.sciencedirect.com ScienceDirect Energy Procedia 61 (2014 ) 882 886 The 6 th International Conference on Applied Energy ICAE2014 INDOOR HUMAN THERMAL COMFORT OPTIMAL CONTROL WITH
Effect of domestic storage and cooking conditions on the risk distribution in ready to cook meat products
 Effect of domestic storage and cooking conditions on the risk distribution in ready to cook meat products Bakalis S.*, Giannakourou M.C. and Taoukis P. School of Chemical Engineering, National Technical
Effect of domestic storage and cooking conditions on the risk distribution in ready to cook meat products Bakalis S.*, Giannakourou M.C. and Taoukis P. School of Chemical Engineering, National Technical
Evaluation of a dynamic model for a cold climate counter flow air to air heat exchanger
 Evaluation of a dynamic model for a cold climate counter flow air to air heat exchanger Toke Rammer Nielsen, Associate Professor, Department of Civil Engineering, Technical University of Denmark; trn@byg.dtu.dk
Evaluation of a dynamic model for a cold climate counter flow air to air heat exchanger Toke Rammer Nielsen, Associate Professor, Department of Civil Engineering, Technical University of Denmark; trn@byg.dtu.dk
Fire Detection Using Image Processing
 Fire Detection Using Image Processing Ku. R.A.Agrawal ME Student Department of CSE Babasaheb Naik college of Engineering Pusad, India rachanaagrawal90@gmail.com Prof. S.T.Khandare Associate professor Department
Fire Detection Using Image Processing Ku. R.A.Agrawal ME Student Department of CSE Babasaheb Naik college of Engineering Pusad, India rachanaagrawal90@gmail.com Prof. S.T.Khandare Associate professor Department
Chapter 4 - Preparation of Stormwater Site Plans
 Chapter 4 - Preparation of Stormwater Site Plans The Stormwater Site Plan is the comprehensive report containing all of the technical information and analysis necessary for the City to evaluate a proposed
Chapter 4 - Preparation of Stormwater Site Plans The Stormwater Site Plan is the comprehensive report containing all of the technical information and analysis necessary for the City to evaluate a proposed
Applied Data Science: Using Machine Learning for Alarm Verification
 Applied Data Science: Using Machine Learning for Alarm Verification by Jan Stampfli and Kurt Stockinger Zurich University of Applied Sciences, Switzerland Introduction False alarms triggered by sensors
Applied Data Science: Using Machine Learning for Alarm Verification by Jan Stampfli and Kurt Stockinger Zurich University of Applied Sciences, Switzerland Introduction False alarms triggered by sensors
MULTISITE. Multisite Activation. Microsoft Dynamics AX White Paper
 MULTISITE Microsoft Dynamics AX 2009 Multisite Activation White Paper Date: June 2008 Introduction... 3 Multisite activation... 4 Prerequisites... 4 Multisite activation update jobs... 5 Multisite activation
MULTISITE Microsoft Dynamics AX 2009 Multisite Activation White Paper Date: June 2008 Introduction... 3 Multisite activation... 4 Prerequisites... 4 Multisite activation update jobs... 5 Multisite activation
Measure Lifetime Derived from a Field Study of Age at Replacement
 Measure Lifetime Derived from a Field Study of Age at Replacement David Robison, MicroGrid David Cohan Bruce True, Portland General Electric The traditional engineering technique for estimating the expected
Measure Lifetime Derived from a Field Study of Age at Replacement David Robison, MicroGrid David Cohan Bruce True, Portland General Electric The traditional engineering technique for estimating the expected
Intrusion Detection: Eliminating False Alarms
 Intrusion Detection: Eliminating False Alarms MAFTIA Final Review Andreas Wespi 18/19 February 2003 Newcastle Overview! MAFTIA and Intrusion Detection! Eliminating False Alarms! Demonstrator of an Intrusion-Tolerant
Intrusion Detection: Eliminating False Alarms MAFTIA Final Review Andreas Wespi 18/19 February 2003 Newcastle Overview! MAFTIA and Intrusion Detection! Eliminating False Alarms! Demonstrator of an Intrusion-Tolerant
Research on Decision Tree Application in Data of Fire Alarm Receipt and Disposal
 Research Journal of Applied Sciences, Engineering and Technology 5(22): 5217-5222, 2013 ISSN: 2040-7459; e-issn: 2040-7467 Maxwell Scientific Organization, 2013 Submitted: October 09, 2012 Accepted: December
Research Journal of Applied Sciences, Engineering and Technology 5(22): 5217-5222, 2013 ISSN: 2040-7459; e-issn: 2040-7467 Maxwell Scientific Organization, 2013 Submitted: October 09, 2012 Accepted: December
Application Note. Application Note for BAYEX
 Application Note Application Note for BAYEX Preface This application note provides the user a more detailed description of the Bayesian statistical methodology available in Version 8.05 and above, of the
Application Note Application Note for BAYEX Preface This application note provides the user a more detailed description of the Bayesian statistical methodology available in Version 8.05 and above, of the
OPERATION OF RADIATION PORTAL MONITORS OF SPECIAL NUCLEAR MATERIALS AT NUCLEAR SITES IN TERMS OF RELIABILITY
 Jr. of Industrial Pollution Control 32(2016) pp 442-448 www.icontrolpollution.com Research OPERATION OF RADIATION PORTAL MONITORS OF SPECIAL NUCLEAR MATERIALS AT NUCLEAR SITES IN TERMS OF RELIABILITY E.A.
Jr. of Industrial Pollution Control 32(2016) pp 442-448 www.icontrolpollution.com Research OPERATION OF RADIATION PORTAL MONITORS OF SPECIAL NUCLEAR MATERIALS AT NUCLEAR SITES IN TERMS OF RELIABILITY E.A.
A Generalized Delay-timer for Alarm Triggering
 2012 American Control Conference Fairmont Queen Elizabeth, Montreal, Canada June 27-June 29,2012 A Generalized Delay-timer for Alarm Triggering Naseeb Ahmed Adnan, Yue Cheng, Iman Izadi and Tongwen Chen
2012 American Control Conference Fairmont Queen Elizabeth, Montreal, Canada June 27-June 29,2012 A Generalized Delay-timer for Alarm Triggering Naseeb Ahmed Adnan, Yue Cheng, Iman Izadi and Tongwen Chen
DynAMo Alarm & Operations Management
 Connected Plant DynAMo Alarm & Operations Management Solution Note Delivering operations integrity through better plant safety, availability and compliance across your entire enterprise Honeywell s DynAMo
Connected Plant DynAMo Alarm & Operations Management Solution Note Delivering operations integrity through better plant safety, availability and compliance across your entire enterprise Honeywell s DynAMo
ADIPEC 2013 Technical Conference Manuscript
 ADIPEC 2013 Technical Conference Manuscript Name: Heidi Fuglum Company: ABB AS Job title: Deployment Manager Address: Ole Deviksvei, Oslo, Norway Phone number: +47 91 36 98 70 Email: Heidi.Fuglum@no.abb.com
ADIPEC 2013 Technical Conference Manuscript Name: Heidi Fuglum Company: ABB AS Job title: Deployment Manager Address: Ole Deviksvei, Oslo, Norway Phone number: +47 91 36 98 70 Email: Heidi.Fuglum@no.abb.com
Effective Use of Statistical Models to Establish and Update Vibration Alarm
 Knowledge Base Article Effective Use of Statistical Models to Establish and Update Vibration Alarm Article ID: NK-1000-0468 Publish Date: 27 Feb 2015 Article Status: Article Type: Required Action: Approved
Knowledge Base Article Effective Use of Statistical Models to Establish and Update Vibration Alarm Article ID: NK-1000-0468 Publish Date: 27 Feb 2015 Article Status: Article Type: Required Action: Approved
Security Management System - Configuring Video Analytics
 Introduction This document describes the steps for configuring the Video Analytics (VA) module available in the Security Management System software. Security Management System video analytics module is
Introduction This document describes the steps for configuring the Video Analytics (VA) module available in the Security Management System software. Security Management System video analytics module is
System development and performance evaluation of track intrusion in Taipei MRT system
 icccbe 2010 Nottingham University Press Proceedings of the International Conference on Computing in Civil and Building Engineering W Tizani (Editor) System development and performance evaluation of track
icccbe 2010 Nottingham University Press Proceedings of the International Conference on Computing in Civil and Building Engineering W Tizani (Editor) System development and performance evaluation of track
ON-LINE SENSOR CALIBRATION MONITORING AND FAULT DETECTION FOR CHEMICAL PROCESSES
 ON-LINE SENSOR CALIBRATION MONITORING AND FAULT DETECTION FOR CHEMICAL PROCESSES Xiao Xu, J. Wesley Hines, Robert E. Uhrig Maintenance and Reliability Center The University of Tennessee Knoxville, TN 37996-23
ON-LINE SENSOR CALIBRATION MONITORING AND FAULT DETECTION FOR CHEMICAL PROCESSES Xiao Xu, J. Wesley Hines, Robert E. Uhrig Maintenance and Reliability Center The University of Tennessee Knoxville, TN 37996-23
Real-Time Root Cause Analysis for Complex Technical Systems
 Real-Time Root Cause Analysis for Complex Technical Systems Jan Eric Larsson, Joseph DeBor IEEE HPRCT Monterey, CA, August 29 th 2007 Handling Alarm Cascades Root cause analysis: find the initiating events
Real-Time Root Cause Analysis for Complex Technical Systems Jan Eric Larsson, Joseph DeBor IEEE HPRCT Monterey, CA, August 29 th 2007 Handling Alarm Cascades Root cause analysis: find the initiating events
excellence in Dependable Automation ALARM MANAGEMENT
 excellence in Dependable Automation ALARM MANAGEMENT www.exida.com Improve the performance of your operators through effective Alarm Management. Typical alarm management issues that hamper operator performance
excellence in Dependable Automation ALARM MANAGEMENT www.exida.com Improve the performance of your operators through effective Alarm Management. Typical alarm management issues that hamper operator performance
SIMPLICITY BY DESIGN M52 CONTROLLER
 SIMPLICITY BY DESIGN M52 CONTROLLER CO-WORK TM CONNECTIVITY Our controller is at the heart of all of ClimateWorx product intelligence. Co-Work TM is based on a unique multi-master network system designed
SIMPLICITY BY DESIGN M52 CONTROLLER CO-WORK TM CONNECTIVITY Our controller is at the heart of all of ClimateWorx product intelligence. Co-Work TM is based on a unique multi-master network system designed
Saying Mahalo to Solar Savings: A Billing Analysis of Solar Water Heaters in Hawaii
 Saying Mahalo to Solar Savings: A Billing Analysis of Solar Water Heaters in Hawaii Jenny Yaillen, Evergreen Economics Chris Ann Dickerson, CAD Consulting Wendy Takanish and John Cole, Hawaii Public Utilities
Saying Mahalo to Solar Savings: A Billing Analysis of Solar Water Heaters in Hawaii Jenny Yaillen, Evergreen Economics Chris Ann Dickerson, CAD Consulting Wendy Takanish and John Cole, Hawaii Public Utilities
Improved occupancy detection accuracy using PIR and door sensors for a smart thermostat
 Improved occupancy detection accuracy using and door sensors for a smart thermostat Sun Ho Kim 1, Hyeun Jun Moon 1, Young Ran Yoon 1 1 Department of Architectural Engineering, Dankook University, Yongin,
Improved occupancy detection accuracy using and door sensors for a smart thermostat Sun Ho Kim 1, Hyeun Jun Moon 1, Young Ran Yoon 1 1 Department of Architectural Engineering, Dankook University, Yongin,
The Basics of Package/Device Cooling
 The Basics of Package/Device Cooling Various cooling methods are available for keeping electronic devices within their operating temperature specifications. Cooling Consumer Products In the case of consumer
The Basics of Package/Device Cooling Various cooling methods are available for keeping electronic devices within their operating temperature specifications. Cooling Consumer Products In the case of consumer
1066. A self-adaptive alarm method for tool condition monitoring based on Parzen window estimation
 1066. A self-adaptive alarm method for tool condition monitoring based on Parzen window estimation Xiaoguang Chen, Guanghua Xu 1066. A SELF-ADAPTIVE ALARM METHOD FOR TOOL CONDITION MONITORING BASED ON
1066. A self-adaptive alarm method for tool condition monitoring based on Parzen window estimation Xiaoguang Chen, Guanghua Xu 1066. A SELF-ADAPTIVE ALARM METHOD FOR TOOL CONDITION MONITORING BASED ON
DYNAMO ALARM MANAGEMENT
 Tyron Vardy Product Director The Secret to Unlocking Operational Integrity 28 September 2017 DYNAMO ALARM MANAGEMENT Defining Operational Integrity 1 To secure a process plants integrity is to reduce the
Tyron Vardy Product Director The Secret to Unlocking Operational Integrity 28 September 2017 DYNAMO ALARM MANAGEMENT Defining Operational Integrity 1 To secure a process plants integrity is to reduce the
Artificial Intelligence Enables a Network Revolution
 *ITU FL-ML5G Artificial Intelligence Enables a Network Revolution April 25, 2018 Network Technology Research Institute, China Unicom Artificial Intelligence Enables a Network Revolution A Part 1 AI application
*ITU FL-ML5G Artificial Intelligence Enables a Network Revolution April 25, 2018 Network Technology Research Institute, China Unicom Artificial Intelligence Enables a Network Revolution A Part 1 AI application
A SURVEY OF OCCUPANT RESPONSE TOWARDS AN AUDIBLE FIRE ALARM
 Int. Journal for Housing Science, Vol.33, No.4 pp. 249-258, 2009 Published in the United States A SURVEY OF OCCUPANT RESPONSE TOWARDS AN AUDIBLE FIRE ALARM L. T. Wong, N. K. Fong and W. H. Sui Department
Int. Journal for Housing Science, Vol.33, No.4 pp. 249-258, 2009 Published in the United States A SURVEY OF OCCUPANT RESPONSE TOWARDS AN AUDIBLE FIRE ALARM L. T. Wong, N. K. Fong and W. H. Sui Department
Interim Advice Note 76 / 06 ASSESSMENT PART 1 AIMS AND OBJECTIVES OF ENVIRONMENTAL ASSESSMENT. Contents
 Interim Advice Note 76 / 06 VOLUME 11 SECTION 1: ENVIRONMENTAL ASSESSMENT INTRODUCTION PART 1 AIMS AND OBJECTIVES OF ENVIRONMENTAL ASSESSMENT Contents 1. Introduction and Application 2. Aims and Objectives
Interim Advice Note 76 / 06 VOLUME 11 SECTION 1: ENVIRONMENTAL ASSESSMENT INTRODUCTION PART 1 AIMS AND OBJECTIVES OF ENVIRONMENTAL ASSESSMENT Contents 1. Introduction and Application 2. Aims and Objectives
Practical Distributed Control Systems (DCS) for Engineers & Technicians. Contents
 Practical Distributed Control Systems (DCS) for Engineers & Technicians Contents Chapter 1 Introduction to Computer Based Control Systems 1 1.1 Introduction to computer based measurement and control systems
Practical Distributed Control Systems (DCS) for Engineers & Technicians Contents Chapter 1 Introduction to Computer Based Control Systems 1 1.1 Introduction to computer based measurement and control systems
False Alarm Analysis of the CATM-CFAR in Presence of Clutter Edge
 66 D. IVKOVIĆ, M. ANDRIĆ, B. ZRNIĆ, FALSE ALARM ANALYSIS OF HE M-CFAR IN PRESENCE OF CLUER EDGE False Alarm Analysis of the M-CFAR in Presence of Clutter Edge Dejan IVKOVIĆ., Milenko ANDRIĆ 2, Bojan ZRNIĆ
66 D. IVKOVIĆ, M. ANDRIĆ, B. ZRNIĆ, FALSE ALARM ANALYSIS OF HE M-CFAR IN PRESENCE OF CLUER EDGE False Alarm Analysis of the M-CFAR in Presence of Clutter Edge Dejan IVKOVIĆ., Milenko ANDRIĆ 2, Bojan ZRNIĆ
Product Brief for Alarm Analytics V9.2 April 2010
 Product Brief for Alarm Analytics V9.2 April 2010 Alarm Analytics V9.2 Product Brief April 2010 Complies with industry standards EEMUA 191 and OSHA PSM 1910.119 for Alarm Analytics, connects to all major
Product Brief for Alarm Analytics V9.2 April 2010 Alarm Analytics V9.2 Product Brief April 2010 Complies with industry standards EEMUA 191 and OSHA PSM 1910.119 for Alarm Analytics, connects to all major
Intelligent alarm management
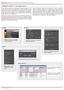 Intelligent alarm management icontrol Web s Advanced Alarm Management enables operators to work together to identify and resolve facility faults to minimize the MTTR. icontrol Web offers Advanced Alarm
Intelligent alarm management icontrol Web s Advanced Alarm Management enables operators to work together to identify and resolve facility faults to minimize the MTTR. icontrol Web offers Advanced Alarm
Experimental Study on the Effects of Compression Parameters on Molding Quality of Dried Fish Floss
 Experimental Study on the Effects of Compression arameters on Molding Quality of Dried Fish Floss Hongmei Xu, Li Zong, Ling Li, and Jing Zhang College of Engineering and Technology, Huazhong Agricultural
Experimental Study on the Effects of Compression arameters on Molding Quality of Dried Fish Floss Hongmei Xu, Li Zong, Ling Li, and Jing Zhang College of Engineering and Technology, Huazhong Agricultural
Microgrid Fault Protection Based on Symmetrical and Differential Current Components
 Microgrid Fault Protection Based on Symmetrical and Differential Current Components Prepared for Public Interest Energy Research California Energy Commission Prepared by Hassan Nikkhajoei and Robert H.
Microgrid Fault Protection Based on Symmetrical and Differential Current Components Prepared for Public Interest Energy Research California Energy Commission Prepared by Hassan Nikkhajoei and Robert H.
