Human-Guided Machine Learning for Fast and Accurate Network Alarm Triage
|
|
|
- Kristopher Griffith
- 6 years ago
- Views:
Transcription
1 Human-Guided Machine Learning for Fast and Accurate Network Alarm Triage Saleema Amershi, Bongshin Lee, Ashish Kapoor, Ratul Mahajan, Blaine Christian * Microsoft Research Redmond, WA {bongshin, akapoor, Computer Science & Engineering, DUB, University of Washington Seattle, WA samershi@cs.washington.edu * Microsoft Corporation Redmond, WA blainech@microsoft.com Abstract Network alarm triage refers to grouping and prioritizing a stream of low-level device health information to help operators find and fix problems. Today, this process tends to be largely manual because existing rule-based tools cannot easily evolve with the network. We present CueT, a system that uses interactive machine learning to constantly learn from the triaging decisions of operators. It then uses that learning in novel visualizations to help them quickly and accurately triage alarms. Unlike prior interactive machine learning systems, CueT handles a highly dynamic environment where the groups of interest are not known a priori and evolve constantly. Our evaluations with real operators and data from a large network show that CueT significantly improves the speed and accuracy of alarm triage. 1 Introduction Network alarm triage refers to grouping and prioritizing a stream of low-level device health information (e.g., high link utilization and fan failure alarms) to help operators find and fix problems in computer networks. It is critical that triage is fast and accurate so operators are not misled and problems can be identified and resolved quickly. Many automated systems have been developed for the alarm triage problem [Gardner and Harle, 1996; Steinder and Sethi, 2004], mostly taking the form of expert defined rules or models. However, despite years of effort, these systems are never fully accurate due to the complexity of the problem. Large networks have thousands of diverse devices, each generating a different set of alarms. Further, because each network is different and the set of devices within a network changes over time, it is very challenging to develop systems that work across networks. Therefore, to cope with the inherent inaccuracy of automated systems, networks invariably employ human operators (so called Tier 1 operators) to triage the remaining thousands of alarms per day that can be missed by automation. We explore a fundamentally different approach for alarm triage, using interactive machine learning to constantly learn from operator triage actions and in turn assist them by providing recommendations on how to group incoming alarms based on the learned model at that instant. Our approach is designed for highly dynamic environments where the groups are not known a priori and evolve constantly. It can also be applied to other scenarios where people need help organizing a continuous data stream (e.g., RSS feeds, management, social network updates). We implement our approach in the context of the alarm triage problem with a system we call CueT (Figure 1). Our simulation experiments with real data from a large, global network with approximately 15,000 devices show the potential of our constantly-updating machine-learning-based approach for improving the alarm triage process. However, as with all automation, machine-learning-based systems are never perfectly accurate. Therefore, in real-world applications of our approach, it is critical that operators carefully inspect and compare recommendations before deciding how to finally proceed. To this end, CueT includes a novel visualization that conveys its recommendation confidence to further help operators decide how to triage. Our evaluation with human operators shows that CueT s combination of interactive machine learning with novel visualizations significantly improves the accuracy and reduces the time required for alarm triage. 2 Related Work Most research in network monitoring and alarm correlation has focused either on visualizations or automated solutions in isolation. Researchers have recently proposed visualization systems for network monitoring and diagnosis. For example, Visual-I [Fisher et al., 2008] uses visual grouping and scatterplots to highlight correlations between multiple devices and problems. Our approach combines visualization and interactive machine learning in order to further reduce the cognitive effort of manually identifying patterns in large data sets. Helping automate pattern discovery can increase operator efficiency and accuracy, necessary for these time critical problems. Automated alarm correlation (also related to root cause analysis and fault localization) has long been an active area of research because of the complexity of the problem and the
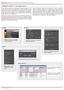
2 Figure 1. CueT s interface. Alarms stream in from the network and are displayed on the right. CueT s triage recommendations for each alarm appear on the left along with a visualization of CueT s confidence in those recommendations (far left). Device Names and other information are blurred for security reasons. potential impact on the industry [Gardner and Harle, 1996; Steinder and Sethi, 2004]. Most solutions have taken the form of expert defined rules or models (e.g., [Gardner and Harle, 1996; Jakobson and Weissman, 1993]). Such approaches require manual configuration of rules which can be difficult to obtain, are not robust to new situations, and require frequent maintenance [Gardner and Harle, 1996; Steinder and Sethi, 2004]. In contrast, our approach can handle general alarm correlations that require alarm grouping based on similarity. Some researchers have explored automatically learning rules or models from data that can then be used for automated alarm correlation and filtering (e.g., [Klementtinen et al., 1999; Steinder and Sethi, 2004]). However, most of these approaches require extensive training periods and must be retrained whenever the network topology changes [Steinder and Sethi, 2004]. In contrast, our approach is based on a dynamically changing model that is constantly learning from human guidance. We argue that human input is critical during the alarm correlation process because of the inherently inconsistent and ambiguous nature of the problem [Gardner and Harle, 1996], a key reason why alarm correlation is still an open area of research. While today s commercial systems employ some of these previous techniques [EMC Ionix 1 ; Yemini et al., 1996], most companies still require teams of Tier 1 operators to manually triage the thousands of remaining alarms unhandled by existing systems. Our work is closely aligned with evolving research on interactive machine learning, asserting the importance of human involvement and proposing interactive systems for various applications (e.g., image segmentation [Fails and Olsen, 2003], document grouping [Basu et al., 2010], and image search [Fogarty et al., 2008]). While previous work has focused on pool-based static environments where the categories of interest and the pool of unlabeled data are known a priori, our work involves a more challenging scenario where data is streaming in and out and the set of labels is constantly changing over time. 3 CueT CueT consists of two interacting components: (1) an interface to assist operators in inspecting triage recommendations and feeding operator actions back into the learning system and (2) a stream-based interactive machine learning engine for making triage recommendations. We will refer to the alarm currently being triaged as the incoming alarm, a group of one or more related alarms that have already been triaged as a ticket, and the current set of tickets that are being used for recommendations (and have not been discarded yet) as the working set of tickets. 1
3 3.1 CueT Interface CueT s interface (Figure 1) consists of two main views: the Alarm View on the right and the Ticket View on the left. Alarms are displayed in the Alarm View as they stream in from the network. Since operators often miss important alarms that appear off of the screen, the Alarm View includes an Alarm Overview (far right in Figure 1) that provides awareness of all alarms still requiring triage even if they are off the screen. Each time an operator clicks on an alarm to triage in the Alarm View, CueT generates its ticket recommendations for the selected alarm and displays them in the Ticket View along with a visualization illustrating its confidence in those recommendations with the Ticket Distance Overview (far left in Figure 1). Tickets are a collection of related alarms. Each ticket has a parent alarm, which is manually determined by a human operator and typically represents either the most severe or the first alarm in the ticket. Immediately below the ticket label (at the top of each ticket in the Ticket View) is information about the ticket s parent alarm along with the ticket description. Below the parent alarm is the best matching alarm within the ticket to the incoming alarm (next to the star icons in Figure 1). This serves as an explanation for why CueT is recommending that an operator triage an alarm into a given ticket. Thus, ticket representations are tailored for each alarm. Operators can also click on a ticket to display all the alarms currently grouped within the ticket. New ticket recommendations are displayed as empty ticket stubs with a gray label and text displaying Start New Ticket. Operators can inspect CueT s ticket recommendations and the Ticket Distance Overview visualization to determine how to triage an incoming alarm (i.e., either add it to an existing ticket or start a new one). Each bubble in the Ticket Distance Overview corresponds to a ticket and its vertical position relative to the top of the overview reflects the similarity between the alarm being triaged and each ticket within the working set. That is, the closer the bubble is to the top, the better a match the corresponding ticket is for the alarm currently being triaged. Bubbles that are positioned near each other are comparable in terms of their similarity to the alarm. In this case, the overview should encourage operators to inspect all comparable tickets before triaging. The Ticket View initially displays only the tickets closest to the alarm being triaged (where closest is determined by our simulations discussed in the following sections) as this helps to balance operator load and the probability of these tickets containing the correct recommendation. However, CueT allows operators to reveal more tickets to inspect using the Ticket Distance Overview. Operators triage an alarm by dragging and dropping it onto the appropriate ticket in the Ticket View. CueT s interface also contains a Search View (bottom left in Figure 1) through which operators can search for existing tickets by entering a search string as they do with their current system for triaging alarms. Operators can add alarms to tickets appearing in the Search View just as in the Ticket View. 3.2 Stream-Based Interactive Machine Learning We tackle the challenges due to the highly dynamic environment and ever-evolving set of classes (i.e., the working set of tickets and the alarms within those tickets) by building on nearest neighbor classification. CueT provides triage recommendations for an incoming alarm by ordering the working set of tickets by their similarity to that alarm. Similarity is measured using a distance function that adapts based on operator actions. We extend classification to include a mechanism for recommending when an incoming alarm should spawn a new ticket. Recommending Existing Tickets CueT makes recommendations by ordering the working set of tickets by the average distance between the incoming alarm and each alarm in the ticket. Distance between alarms is measured using 17 individual string-based distance metrics, each of which represents similarity along an alarm attribute. Our simulations described later show that these string-based distance metrics effectively capture operators practice of visually comparing the attribute values of alarms. The attributes operators typically inspect are: Device Name (e.g., ab1-cd2-ef3-gh4), Device Type (e.g., Router, Switch), Element Type (device part needing attention, e.g., Port), Name (includes Device Name and information about the Element needing attention, e.g., Port-ab1-cd2-ef3-gh4), Severity (from 1 to 5 representing highest to lowest priority, respectively), and Event Name (e.g., High Utilization). For alarm attributes Device Name, Name, Event Name, and the four standard components of the Device Name (e.g., ab1-cd2-ef3-gh4 ab1, cd2, ef3, and gh4), CueT computes two string-based distance metrics (amounting to fourteen total metrics): the edit distance and the longest common substring (LCS) converted to a distance according to: d i,j = maxlength (i, j) s i,j where s i,j is the length of the LCS between strings i and j. We include both edit distance and LCS because they have complementary strengths. For example, LCS is a good measure for strings that encode location. Devices ab1* and ac1* are likely in different locations. For these, LCS distance (which is 2) better captures that these are different than edit distance (which is 1). As described below, our method of learning the combination of these individual metrics will reduce the effect of any irrelevant metric (edit distance in this case). For alarm attributes Device Type, Element Type, and Severity, CueT computes one string matching distance metric each (amounting to three metrics in total). This distance metric returns 0 if the attribute values are the same or 1 if they are different. We combine these 17 distance metrics using Mahalanobis distance, which parameterizes distance between any alarms u and v, represented as d dimensional feature vectors, by a d d positive definite covariance matrix A: Distance (u, v) = (u - v) T A (u - v) This function effectively weights the 17 distances by the matrix A, which encodes their relative importance for alarm classification and the correlations between them.
4 We learn the parameters of the matrix A from operator actions, extending an online metric learning algorithm [Jain et al., 2008] originally derived for static environments to dynamic scenarios where both the number and type of classes are varying. In particular, given a stream of alarms, each labeled with the ticket it was triaged into, we incrementally update the matrix A by encoding the labels as constraints indicating that the incoming alarm and each alarm in the target ticket should be near each other. When an alarm spawns a new ticket, no update is made to the matrix A (however, this changes the working set of tickets). To learn the parameters of A, we initialize it to the identity matrix (setting the regularization parameter η to.001) and then update the parameters as we observe triage actions. We continue this process for N alarms, where N is determined empirically from our simulations described below, and then fix the distance function. The final covariance matrix A N is used in making recommendations for the remaining data. Intuitively, the parameters learned for the matrix A reflect the importance of and correlations among the individual distance metrics to best explain the human operator s actions. The advantage of learning the matrix A from data is that it does not require expert tuning, which can be difficult to obtain and does not evolve with the network [Gardner and Harle, 1996; Steinder and Sethi, 2004]. Recommending Starting a New Ticket CueT maintains a threshold distance for starting a new ticket based on information about when operators spawn new tickets. When an operator spawns a new ticket for an incoming alarm, the distance between this alarm and the nearest ticket in the working set is stored. We experimented with several strategies for computing the threshold distance from these stored distances including taking the minimum and average of the most recently stored distances or of all the distances. We found that taking the minimum within the five most recently stored distances performs best. For each incoming alarm, CueT computes the latest threshold distance using the strategy above and inserts a Start New Ticket recommendation into its ordered list of recommendations according to this distance. Spawning New Tickets and Discarding Old Tickets When an operator determines that an incoming alarm is part of a new problem, a new ticket is created and added to the working set. CueT also automatically discards old tickets, simulating the resolution of problems. We use a windowing mechanism to discard old tickets. In particular, we fix the window size to N, which is the number of alarms used for learning our covariance matrix. Any time the number of unique alarms in the working set of tickets exceeds N we remove the oldest ticket in the set. Spawning new tickets and discarding old ones means that the working set of tickets used for machine-learning-based recommendations is continually evolving as an operator interacts with CueT. 3.3 Simulation Experiments For our experiments simulating human interaction with CueT s interactive machine learning component, we obtained alarm triage data from a network operations center at a large organization that monitors a network with approximately 15,000 devices. This data was labeled by Tier 1 operators through their manual triage process. To evaluate CueT s interactive machine learning component over a long period, we use data spread across several months: from the first day of each month between January and August 2010 (inclusive) except for May and July when the network had recording problems. This data set contains 338,218 alarms, of which 8,719 are unique (as devices typically generate duplicate alarms when problems occur) and are mapped to 1,281 unique tickets. To simulate human interaction and compute the accuracy of CueT s learning, we processed alarms in the data in the order in which they occurred. For each alarm, we first compute an ordered list of recommendations that we use to measure accuracy. Then, we obtain the actual label for the alarm and either add the alarm to an existing ticket or create a new ticket. If we add the incoming alarm to an existing ticket and we have observed fewer than N alarms, we update A N as described previously. If we start a new ticket, we update the threshold distance for starting new tickets and update the working set of tickets. Finally, if we determine that the working set has exceeded the window size of N alarms, we discard the oldest ticket in the set. We measure recommendation accuracy for each incoming alarm by comparing the recommendations to the ground truth (all of the alarm triage data observed before reaching the incoming alarm, without discarding any tickets due to our fixed window size N). Note that the nature of the problem we are dealing with requires that we operate in a moving window. Therefore, some of our errors may be the result of discarding tickets (e.g., recommending a new ticket when the correct ticket is in the ground truth but no longer exists in the working set). Because multiple tickets may be the same distance away from an incoming alarm, we compute recommendation accuracy as whether or not the alarm s actual label appeared within the set of ticket recommendations a given distance away from the alarm or closer. For example, if CueT predicts two different tickets as being equally closest to the incoming alarm ( Top 1 distance away) and if the correct label is one of the two tickets, then we consider this a correct recommendation at the Top 1 distance. We experimented with accuracy within the Top 1, 2, 3, and 4 distances from the incoming alarm. We ran ten simulations over our data, varying the number of alarms N used in both learning the distance function parameters A N as well as in the window size for discarding old tickets. Figure 2 (left) illustrates CueT s accuracy within the set of tickets recommended at the Top 1, 2, 3, and 4 distances from incoming alarms averaged over all the simulation trials. Figure 2 (middle and right) shows the average number and percentage of tickets (out of N) presented at each of the Top 1 to 4 distances. From these results it appears that presenting tickets within the Top 3 distances achieves a good balance between relatively high accuracy and a small number of tickets being presented.
5 Figure 2. CueT s accuracy (left), number (middle), and % of tickets presented (right) within Top 1, 2, 3, 4 distances from each incoming alarm, averaged over all simulation trials. Figure 3. CueT s accuracy at the Top 3 distances for various window sizes N. N=30 achieves peak performance. Therefore, for our user study described later, we fix CueT to recommend tickets for an incoming alarm (in the TicketView) within the Top 3 distances from that alarm. CueT s accuracy at the Top 3 distances over the various values of N that we experimented with (10, 20, 30, 40, 50, 100, 150, 200, 250, and 300) appears to peak at an N value of 30 alarms (Figure 3). Therefore, for our user study, we set N=30 in our interactive machine learning engine. 4 User Study We conducted a user study to examine the effectiveness of CueT for alarm triage as compared to the traditional method of manually ticketing alarms. For the Traditional condition, we replicated the commercial system used by our network operators. For our study we used part of the data that we used for our simulation experiments (January 1, 2010 data). We ran it as a within-subjects study, with each participant performing alarm triage using both CueT and the Traditional method. To avoid a learning effect, we counterbalanced the presentation order of the two interfaces. We recruited eleven people (two female, ages 28 to 44) plus one male pilot from the network operations team. Each participant worked on an identical dual-core Windows 7 machine attached to a 20.1 monitor at a resolution of 1200x1600 (i.e., in a portrait orientation). We measured accuracy, speed, and user preference. For more details about the study design and results refer to [Amershi et al., 2011]. 4.1 Results Accuracy is computed as the percentage of alarms correctly triaged out of the total presented. Correctness of participant labels is measured against the ground truth labels. We compute two measures for speed: Time on Screen and Time to Ticket. The former is the time between when an alarm appeared on screen and when the participant triaged that alarm. Along with Accuracy, it is a key measure of triage performance and is used to formulate service level agreements (SLAs) that the monitoring team offers. For instance, a possible guarantee may be that for 95% of alarms, Time on Screen will be under 5 minutes. Since operators need not triage alarms in the order in which they appear on screen, Time on Screen is affected by the order in which an operator decides to triage alarms. Therefore, we also study Time to Ticket, which is the time between successive triage actions regardless of order. For Accuracy, Time on Screen, and Time to Ticket, we perform paired-samples t tests and our analyses showed that participants were able to triage alarms faster with CueT than with the Traditional interface while maintaining the same level of accuracy. Participants were significantly faster with CueT than Traditional in terms of Time on Screen (M=107.7s, SD=127.7s vs. M=277.8s, SD=168.5s, t(10)=4.43, p=.001) and Time to Ticket (M=10.1s, SD=2.69s vs. M=12.9s, SD=3.79s, t(10)=3.26, p=.009). There was no significant difference in terms of accuracy (M=71.8%, SD=17% vs. M=76.4%, SD=8%). Our data included a type of alarm that required special handling. Operators are usually instructed to always create a new ticket for each such alarm, regardless of similarity to other alarms. Only a few participants asked us how to triage these alarms, to which we responded that they should triage as normal. The logged data shows that these alarms were handled unevenly by participants. Some rapidly created new tickets without inspecting recommendations (in CueT) or searching related tickets (in the CueT or Traditional condition), while others triaged based on similarity. These alarms reduce CueT s accuracy because its model does not handle exceptional cases. Despite this, our results show that CueT s accuracy is no worse and its speed is much better. We re-did our analysis after removing 39 of these exceptional alarms to evaluate CueT s performance in the absence of special cases. Our corrected analyses show that participants were still faster with CueT but also more accurate than with Traditional (M=81.3%, SD=6% vs. M=72.4%, SD=12%, t(10)=2.29, p=.045) (Figure 4). They were significantly faster with CueT at triaging in terms of both Time on Screen (M=86.9s, SD=69.2s vs. M=176.2s, SD=85.2s, t(10)=4.63, p=.001) and Time to Ticket (M=9.9s, SD=3.1s vs. M=15.7s, SD=4.6s, t(10)=6.52, p<.001). We analyze our user preference questionnaires using Friedman Chi-Square tests. CueT was favored significantly more than Traditional in terms of overall satisfaction Figure 4. Accuracy (left), Time on Screen (middle), and Time to Ticket (right) comparisons. All differences are significant. Error bars represent standard error.
6 (χ 2 (1,N=11)=9.0, p=.003), how much participants liked using the system (χ 2 (1,N=11)=11.0, p=.001), whether they felt that they could efficiently ticket alarms with the system (χ 2 (1,N=11)=6.4, p=.011), and whether they felt the system was easy to use (χ 2 (1,N=11)=11.0, p=.001). Regarding CueT-specific features, participants tended to agree with the statements The ticket recommendations were useful (5.81 avg. on a 7-point Likert scale, 7 being the highest level of agreement) and The Distance Overview was useful (5.36 avg.). In addition, all of our participants chose CueT as their preferred system for alarm triage. 5 Discussion and Conclusion Our results show that network operators can triage alarms significantly faster with CueT than with their traditional method. When considering general alarms as well as exceptional cases, CueT reduces the Time on Screen of alarms by 61.2% on average. When excluding exceptional cases the savings are 50.7%. Savings are lower without exceptional cases because these require an action that can be performed quickly and without deliberation (e.g., rapidly creating new tickets without looking for similar tickets). For Time to Ticket, CueT enables a savings of 21.6% when considering general and exceptional alarms, and a savings of 36.8% when considering only the general alarms that CueT is designed for. To put this in perspective, assuming 10K alarms per day and a time savings of 5.8s per alarm (36.8%), the estimated cumulative time savings using this measure amounts to about 20 operator days per month. CueT currently cannot automatically exclude exceptional cases from its dynamically changing model. Remarkably, when considering general alarms along with exceptional cases, no significant decrease in overall accuracy is observed. This suggests that CueT does not adversely affect operator ability to deal with exceptional cases. Furthermore, although including exceptional cases in CueT s dynamic model may cause interference in recommendation accuracy, CueT still performed significantly better than the traditional method for the general case, by 9%. This points at the robustness of using triage recommendations from human-guided interactive machine learning based models. As interference can negatively affect CueT s recommendation accuracy, it is fair to regard CueT s performance results as a lower bound on its potential for improving alarm triage. We believe CueT s tight integration of interactive machine learning and visualization is key to its success. As with other distance-based recommendation systems, multiple tickets in CueT can be equally distant from an alarm. Presenting recommendations as a traditional list would therefore require arbitrarily ordering tickets which would likely mislead operators. To ensure high accuracy, the Ticket Distance Overview was designed to illustrate recommendation quality and encourage operators to inspect comparable tickets. Further, the coupling between machine learning and visualization makes it easy for operators to provide feedback and keep the model up-to-date. CueT demonstrates the importance of human involvement to complement and improve automated systems that are never fully accurate due to the complexity of the problem. While CueT is designed for triaging alarms, we believe that the lessons learned readily extend to other scenarios where humans need to organize continuous streams of data. Acknowledgments We thank the staff at the network operations center and our study participants for their time and feedback. References [Amershi et al., 2011] Saleema Amershi, Bongshin Lee, Ashish Kapoor, Ratul Mahajan, and Blaine Christian. CueT: Human-Guided Fast and Accurate Network Alarm Triage. To appear in Proc. CHI [Basu et al., 2010] Sumit Basu, Danyel Fisher, Steven M. Drucker, and Hao Lu. Assisting Users with Clustering Tasks by Combining Metric Learning and Classification. Proc. AAAI [Fails and Olsen, 2003] Jerry Alan Fails and Dan R. Olsen, Jr. Interactive Machine Learning. Proc. IUI 2003, pages [Fisher et al., 2008] Danyel Fisher, David A. Maltz, Albert Greenberg, Xiaoyu Wang, Heather Warncke, Geroge Robertson, and Mary Czerwinski. Using Visualization to Support Network and Application Management in a Data Center. Proc. INM 2008, pages 1-6. [Fogarty et al., 2008] James Fogarty, Desney Tan, Ashish Kapoor, and Simon Winder. CueFlik: Interactive Concept Learning in Image Search. Proc. CHI 2008, pages [Gardner and Harle, 1996] Robert D. Gardner and David A. Harle. Methods and Systems for Alarm Correlation. Proc. GLOBECOM 1996, pages [Jain et al., 2008] Prateek Jain, Brian Kulis, Inderjit S. Dhillon, and Kristen Grauman. Online Metric Learning and Fast Similarity Search. Proc. NIPS 2008, pages [Jakobson and Weissman, 1993] Gabriel Jakobson and Mark D. Weissman. Alarm Correlation: Correlating multiple network alarms improves telecommunications network surveillance and fault management. IEEE Network, 7(6): 52-59, [Klementtinen et al., 1999] Mika Klemettinen, Heikki Mannila, and Hannu Toivonen. Rule Discovery in Telecommunication Alarm Data. J. Network and Systems Management, 7(4): , [Steinder and Sethi, 2004] Malgorzata Steinder and Adarshpal S. Sethi. A Survey of Fault Localization Techniques in Computer Networks. Science of Computer Programming, 53(2): , [Yemini et al., 1996] Shaula Alexander Yemini, Shmuel Kliger, Eyal Mozes, Yechiam Yemini, and David Ohsie. High Speed and Robust Event Correlation. IEEE Communications Magazine, 34(5): 82-90, 1996.
To appear in the IEEE/IFIP 1996 Network Operations and Management. Symposium (NOMS'96), Kyoto, Japan, April TASA: Telecommunication
 To appear in the IEEE/IFIP 1996 Operations and Management Symposium (NOMS'96), Kyoto, Japan, April 1996. TASA: Telecommunication Alarm Sequence Analyzer or How to enjoy faults in your network Kimmo Hatonen,
To appear in the IEEE/IFIP 1996 Operations and Management Symposium (NOMS'96), Kyoto, Japan, April 1996. TASA: Telecommunication Alarm Sequence Analyzer or How to enjoy faults in your network Kimmo Hatonen,
Effective Alarm Management for Dynamic and Vessel Control Systems
 DYNAMIC POSITIONING CONFERENCE October 12-13, 2010 OPERATIONS SESSION Effective Alarm Management for Dynamic and Vessel Control Systems By Steve Savoy Ensco Offshore Company 1. Introduction Marine control
DYNAMIC POSITIONING CONFERENCE October 12-13, 2010 OPERATIONS SESSION Effective Alarm Management for Dynamic and Vessel Control Systems By Steve Savoy Ensco Offshore Company 1. Introduction Marine control
Applied Data Science: Using Machine Learning for Alarm Verification
 Applied Data Science: Using Machine Learning for Alarm Verification by Jan Stampfli and Kurt Stockinger Zurich University of Applied Sciences, Switzerland Introduction False alarms triggered by sensors
Applied Data Science: Using Machine Learning for Alarm Verification by Jan Stampfli and Kurt Stockinger Zurich University of Applied Sciences, Switzerland Introduction False alarms triggered by sensors
Intelligent alarm management
 Intelligent alarm management icontrol Web s Advanced Alarm Management enables operators to work together to identify and resolve facility faults to minimize the MTTR. icontrol Web offers Advanced Alarm
Intelligent alarm management icontrol Web s Advanced Alarm Management enables operators to work together to identify and resolve facility faults to minimize the MTTR. icontrol Web offers Advanced Alarm
An Alarm Correlation Algorithm for Network Management Based on Root Cause Analysis
 An Alarm Correlation Algorithm for Network Management Based on Root Cause Analysis Dae Sun Kim*, Hiroyuki Shinbo*, Hidetoshi Yokota* *KDDI R&D Laboratories, Inc. Fujimino, Saitama, Japan da-kim@kddilabs.jp,
An Alarm Correlation Algorithm for Network Management Based on Root Cause Analysis Dae Sun Kim*, Hiroyuki Shinbo*, Hidetoshi Yokota* *KDDI R&D Laboratories, Inc. Fujimino, Saitama, Japan da-kim@kddilabs.jp,
DeltaV Operate. Product Data Sheet DeltaV Operate December 2006 Page 1. Introduction. Benefits
 December 2006 Page 1 You can easily manage your process with. Powerful operator interface, optionally up to four monitors Alarms prioritized by user Secure, standard operating desktop Intuitive graphics
December 2006 Page 1 You can easily manage your process with. Powerful operator interface, optionally up to four monitors Alarms prioritized by user Secure, standard operating desktop Intuitive graphics
Real Time Pipeline Leak Detection on Shell s North Western Ethylene Pipeline
 Real Time Pipeline Leak Detection on Shell s North Western Ethylene Pipeline Dr Jun Zhang & Dr Ling Xu* REL Instrumentation Limited ABSTRACT In the past ten years, a number of pipeline leak detection systems
Real Time Pipeline Leak Detection on Shell s North Western Ethylene Pipeline Dr Jun Zhang & Dr Ling Xu* REL Instrumentation Limited ABSTRACT In the past ten years, a number of pipeline leak detection systems
Video Smoke Detection using Deep Domain Adaptation Enhanced with Synthetic Smoke Images
 Video Smoke Detection using Deep Domain Adaptation Enhanced with Synthetic Smoke Images Gao Xu, Qixing Zhang, Gaohua Lin, Jinjun Wang, Yongming Zhang State Key Laboratory of Fire Science, University of
Video Smoke Detection using Deep Domain Adaptation Enhanced with Synthetic Smoke Images Gao Xu, Qixing Zhang, Gaohua Lin, Jinjun Wang, Yongming Zhang State Key Laboratory of Fire Science, University of
[ [ ADMIN PANEL USER GUIDE
 [ [ ADMIN PANEL USER GUIDE ADMIN PANEL USER GUIDE 2 Contents Logging In & Systems Overview 3 System Details 5 Analytics 6 View Alarms 8 Manage Alarms 9 Create Alarms 10 Device Reporting Alarm 11 Monthly
[ [ ADMIN PANEL USER GUIDE ADMIN PANEL USER GUIDE 2 Contents Logging In & Systems Overview 3 System Details 5 Analytics 6 View Alarms 8 Manage Alarms 9 Create Alarms 10 Device Reporting Alarm 11 Monthly
Smoke Alarm Response Time:
 Smoke Alarm Response Time: Examining the Relationship Between Working Smoke Alarms, Fire Service Response Times and Fire Outcomes Joseph Clare, Charles Jennings, Len Garis November 2018 Executive Summary
Smoke Alarm Response Time: Examining the Relationship Between Working Smoke Alarms, Fire Service Response Times and Fire Outcomes Joseph Clare, Charles Jennings, Len Garis November 2018 Executive Summary
SYNERGY IN LEAK DETECTION: COMBINING LEAK DETECTION TECHNOLOGIES THAT USE DIFFERENT PHYSICAL PRINCIPLES
 Proceedings of the 2014 10 th International Pipeline Conference IPC2014 September 29-October 3, 2014, Calgary, Alberta, Canada IPC2014-33387 SYNERGY IN LEAK DETECTION: COMBINING LEAK DETECTION TECHNOLOGIES
Proceedings of the 2014 10 th International Pipeline Conference IPC2014 September 29-October 3, 2014, Calgary, Alberta, Canada IPC2014-33387 SYNERGY IN LEAK DETECTION: COMBINING LEAK DETECTION TECHNOLOGIES
ABB Ability System 800xA Alarm Management
 ABB Ability System 800xA Alarm Management Effective detection, notification, analysis and corrective action of abnormal situations. When an alarm sounds in a process controlled by ABB s System 800xA, operators
ABB Ability System 800xA Alarm Management Effective detection, notification, analysis and corrective action of abnormal situations. When an alarm sounds in a process controlled by ABB s System 800xA, operators
Samsung SDS BMS Ver.2.0. Technical Specification
 Samsung SDS BMS Ver.2.0 Technical Specification Technical Specifications All rights and title, including all intellectual property rights to Samsung SDS BMS" is retained by Samsung SDS Co, Ltd. ("SDS"),
Samsung SDS BMS Ver.2.0 Technical Specification Technical Specifications All rights and title, including all intellectual property rights to Samsung SDS BMS" is retained by Samsung SDS Co, Ltd. ("SDS"),
Alarm Management: EPRI Survey on the State of Technology
 Alarm Management: EPRI Survey on the State of Technology Sean McGuinness EPRI EPCC 13, Bled, Slovenia 20-May-2015 General Alarm Management Background Alarm Management is critical to safe and reliable grid
Alarm Management: EPRI Survey on the State of Technology Sean McGuinness EPRI EPCC 13, Bled, Slovenia 20-May-2015 General Alarm Management Background Alarm Management is critical to safe and reliable grid
Where Technology Shapes Solutions. Alarm management : Wasn t that problem already solved years ago?
 Honeywell Users Group 2011 Where Technology Shapes Solutions. Luc De Wilde, Total Petrochemicals Dal Vernon Reising, Human Centered Solutions Alarm management : Wasn t that problem already solved years
Honeywell Users Group 2011 Where Technology Shapes Solutions. Luc De Wilde, Total Petrochemicals Dal Vernon Reising, Human Centered Solutions Alarm management : Wasn t that problem already solved years
Saying Mahalo to Solar Savings: A Billing Analysis of Solar Water Heaters in Hawaii
 Saying Mahalo to Solar Savings: A Billing Analysis of Solar Water Heaters in Hawaii Jenny Yaillen, Evergreen Economics Chris Ann Dickerson, CAD Consulting Wendy Takanish and John Cole, Hawaii Public Utilities
Saying Mahalo to Solar Savings: A Billing Analysis of Solar Water Heaters in Hawaii Jenny Yaillen, Evergreen Economics Chris Ann Dickerson, CAD Consulting Wendy Takanish and John Cole, Hawaii Public Utilities
Patriot Systems Limited
 COPYRIGHT 1997 - The Patriot Systems Ltd. Patriot Alarm Monitoring Automation Package is licensed for use on one computer, by the original person, or company, or organization whose name is registered with
COPYRIGHT 1997 - The Patriot Systems Ltd. Patriot Alarm Monitoring Automation Package is licensed for use on one computer, by the original person, or company, or organization whose name is registered with
Fire Risks of Loviisa NPP During Shutdown States
 Fire Risks of Loviisa NPP During Shutdown States Sami Sirén a*, Ilkka Paavola a, Kalle Jänkälä a a Fortum Power And Heat Oy, Espoo, Finland Abstract: Fire PRA for all 15 shutdown states of Loviisa NPP
Fire Risks of Loviisa NPP During Shutdown States Sami Sirén a*, Ilkka Paavola a, Kalle Jänkälä a a Fortum Power And Heat Oy, Espoo, Finland Abstract: Fire PRA for all 15 shutdown states of Loviisa NPP
Security Management System - Configuring Video Analytics
 Introduction This document describes the steps for configuring the Video Analytics (VA) module available in the Security Management System software. Security Management System video analytics module is
Introduction This document describes the steps for configuring the Video Analytics (VA) module available in the Security Management System software. Security Management System video analytics module is
DeltaV Operate. DeltaV Operate. Introduction. DeltaV Product Data Sheet. Robust and secure plant operations
 February 2016 Page 1 DeltaV Operate You can easily manage your process with. Robust and secure plant operations Powerful operator interface, optionally up to four monitors Constant visibility and access
February 2016 Page 1 DeltaV Operate You can easily manage your process with. Robust and secure plant operations Powerful operator interface, optionally up to four monitors Constant visibility and access
E. Elnahrawy, X. Li, and R. Martin
 Using Area-based Presentations and Metrics for Localization Systems in Wireless LANs E. Elnahrawy, X. Li, and R. Martin Rutgers U. WLAN-Based Localization Localization in indoor environments using 802.11
Using Area-based Presentations and Metrics for Localization Systems in Wireless LANs E. Elnahrawy, X. Li, and R. Martin Rutgers U. WLAN-Based Localization Localization in indoor environments using 802.11
VENTILATIVE COOLING CONTROL STRATEGIES APPLIED TO PASSIVE HOUSE IN ORDER TO AVOID INDOOR OVERHEATING
 VENTILATIVE COOLING CONTROL STRATEGIES APPLIED TO PASSIVE HOUSE IN ORDER TO AVOID INDOOR OVERHEATING Rebeca Barbosa 1, Martin Barták 1, Jan L. M. Hensen 1, 2, Marcel G. L. C. Loomans 2 1 Czech Technical
VENTILATIVE COOLING CONTROL STRATEGIES APPLIED TO PASSIVE HOUSE IN ORDER TO AVOID INDOOR OVERHEATING Rebeca Barbosa 1, Martin Barták 1, Jan L. M. Hensen 1, 2, Marcel G. L. C. Loomans 2 1 Czech Technical
Patriot Systems Limited
 COPYRIGHT 1997 - The Patriot Systems Ltd. Patriot Alarm Monitoring Automation Package is licensed for use on one computer, by the original person, or company, or organisation whose name is registered with
COPYRIGHT 1997 - The Patriot Systems Ltd. Patriot Alarm Monitoring Automation Package is licensed for use on one computer, by the original person, or company, or organisation whose name is registered with
FIMD: Fine-grained Device-free Motion Detection
 ICPADS 2012 FIMD: Fine-grained Device-free Motion Detection Jiang Xiao, Kaishun Wu, Youwen Yi, Lu Wang, Lionel M. Ni Department of Computer Science and Engineering Hong Kong University of Science and Technology
ICPADS 2012 FIMD: Fine-grained Device-free Motion Detection Jiang Xiao, Kaishun Wu, Youwen Yi, Lu Wang, Lionel M. Ni Department of Computer Science and Engineering Hong Kong University of Science and Technology
Theoretical and Experimental Analysis of the Superheating in Heat Pump Compressors. * Corresponding Author ABSTRACT 1.
 568, Page Theoretical and Experimental Analysis of the Superheating in Heat Pump Compressors Jose N. FONSECA *, Rodrigo KREMER, Thiago DUTRA 2 EMBRACO, Research & Development Group, Joinville, Santa Catarina,
568, Page Theoretical and Experimental Analysis of the Superheating in Heat Pump Compressors Jose N. FONSECA *, Rodrigo KREMER, Thiago DUTRA 2 EMBRACO, Research & Development Group, Joinville, Santa Catarina,
Alarm Management for SCADA control rooms
 Whitepaper Alarm Management for SCADA control rooms Definition of the term alarm The concept of alarms (French for a l arme which means spring to arms ) is very old and originates from the military concept
Whitepaper Alarm Management for SCADA control rooms Definition of the term alarm The concept of alarms (French for a l arme which means spring to arms ) is very old and originates from the military concept
Modeling of Ceiling Fan Based on Velocity Measurement for CFD Simulation of Airflow in Large Room
 Modeling of Ceiling Fan Based on Velocity Measurement for CFD Simulation of Airflow in Large Room Y. Momoi 1, K. Sagara 1, T. Yamanaka 1 and H. Kotani 1 1 Osaka University, Graduate School of Eng., Dept.
Modeling of Ceiling Fan Based on Velocity Measurement for CFD Simulation of Airflow in Large Room Y. Momoi 1, K. Sagara 1, T. Yamanaka 1 and H. Kotani 1 1 Osaka University, Graduate School of Eng., Dept.
Improvements in Transmission Control Center Alarm Management Practices
 Improvements in Transmission Control Center Alarm Management Practices Navin Bhatt, Mahendra Patel, Bill Hollifield, Andrew Hunter 2017 CIGRE Grid of the Future Symposium Cleveland, Ohio, U.S.A. 22-25
Improvements in Transmission Control Center Alarm Management Practices Navin Bhatt, Mahendra Patel, Bill Hollifield, Andrew Hunter 2017 CIGRE Grid of the Future Symposium Cleveland, Ohio, U.S.A. 22-25
Monitor Alarms and Events
 This chapter contains the following topics: What Are Alarms and Events?, page 1 How are Alarms and Events Created and Updated?, page 2 Find and View Alarms, page 3 Set Alarm and Event Management Preferences,
This chapter contains the following topics: What Are Alarms and Events?, page 1 How are Alarms and Events Created and Updated?, page 2 Find and View Alarms, page 3 Set Alarm and Event Management Preferences,
Smart Combiners Installation Guide. For Obvius A89DC-08 sensor modules
 For Obvius A89DC-08 sensor modules Introduction Large roof and ground arrays connect the panels into stings that are merged together in combiner boxes. Each string will typically consist of 10-15 panels
For Obvius A89DC-08 sensor modules Introduction Large roof and ground arrays connect the panels into stings that are merged together in combiner boxes. Each string will typically consist of 10-15 panels
Research on Decision Tree Application in Data of Fire Alarm Receipt and Disposal
 Research Journal of Applied Sciences, Engineering and Technology 5(22): 5217-5222, 2013 ISSN: 2040-7459; e-issn: 2040-7467 Maxwell Scientific Organization, 2013 Submitted: October 09, 2012 Accepted: December
Research Journal of Applied Sciences, Engineering and Technology 5(22): 5217-5222, 2013 ISSN: 2040-7459; e-issn: 2040-7467 Maxwell Scientific Organization, 2013 Submitted: October 09, 2012 Accepted: December
Monitor Alarms and Events
 What Are Alarms and Events?, page 1 How are Alarms and Events Created and Updated?, page 2 Which Events Are Supported?, page 5 Set Alarm and Event Management Preferences, page 5 Interpret Event and Alarm
What Are Alarms and Events?, page 1 How are Alarms and Events Created and Updated?, page 2 Which Events Are Supported?, page 5 Set Alarm and Event Management Preferences, page 5 Interpret Event and Alarm
Statistical Analysis of Criteria and Key Aspects for Urban Design Quality Assessment of Built Environment
 Statistical Analysis of Criteria and Key Aspects for Urban Design Quality Assessment of Built Environment Ar. Mohd. Khalid Hasan 1 *, Prof. S. K. Gupta 2, Dr. (Mrs) Sangeeta Bagga Mehta 3 1 Assistant Professor,
Statistical Analysis of Criteria and Key Aspects for Urban Design Quality Assessment of Built Environment Ar. Mohd. Khalid Hasan 1 *, Prof. S. K. Gupta 2, Dr. (Mrs) Sangeeta Bagga Mehta 3 1 Assistant Professor,
Benefits of Enhanced Event Analysis in. Mark Miller
 Benefits of Enhanced Event Analysis in Data Center OTDR Testing Mark Miller Dr. Fang Xu AFL/Noyes Test & Inspection Overview Challenges Topics Techniques and Improvements Benefits of enhanced event analysis
Benefits of Enhanced Event Analysis in Data Center OTDR Testing Mark Miller Dr. Fang Xu AFL/Noyes Test & Inspection Overview Challenges Topics Techniques and Improvements Benefits of enhanced event analysis
Re: Energy Conservation Standards for Residential Boilers; Proposed Rule Docket Number EERE-2012-BT-STD-0047
 August 6, 2015 Ms. Brenda Edwards U.S. Department of Energy Building Technologies Program, Mailstop EE-5B 1000 Independence Avenue SW Washington, DC 20585-0121 Re: Energy Conservation Standards for Residential
August 6, 2015 Ms. Brenda Edwards U.S. Department of Energy Building Technologies Program, Mailstop EE-5B 1000 Independence Avenue SW Washington, DC 20585-0121 Re: Energy Conservation Standards for Residential
Coupling Multiple Hypothesis Testing with Proportion Estimation in Heterogeneous Categorical Sensor Networks
 Advancing the Science of Information Coupling Multiple Hypothesis Testing with Proportion Estimation in Heterogeneous Categorical Sensor Networks DTRA SBIR Phase II Contract: W911SR-10-C-0038 Chris Calderon,
Advancing the Science of Information Coupling Multiple Hypothesis Testing with Proportion Estimation in Heterogeneous Categorical Sensor Networks DTRA SBIR Phase II Contract: W911SR-10-C-0038 Chris Calderon,
When Precision is not good enough
 When Precision is not good enough Andrew Kelley XACT PCB Ltd North Shields, UK Abstract As PCB designs become ever more complex with more sequential build up layers, tighter annular ring designs and broader
When Precision is not good enough Andrew Kelley XACT PCB Ltd North Shields, UK Abstract As PCB designs become ever more complex with more sequential build up layers, tighter annular ring designs and broader
Intrusion Detection System: Facts, Challenges and Futures. By Gina Tjhai 13 th March 2007 Network Research Group
 Intrusion Detection System: Facts, Challenges and Futures By Gina Tjhai 13 th March 2007 Network Research Group 1 Overview Introduction Challenges of current IDS Potential solutions Alarm Correlation Existing
Intrusion Detection System: Facts, Challenges and Futures By Gina Tjhai 13 th March 2007 Network Research Group 1 Overview Introduction Challenges of current IDS Potential solutions Alarm Correlation Existing
6 th Pipeline Technology Conference 2011
 6 th Pipeline Technology Conference 2011 Pipeline Leak Detection and Theft Detection Using Rarefaction Waves Authors: Dr Alex Souza de Joode, VP International Operations; ATMOS International, UK. Andrew
6 th Pipeline Technology Conference 2011 Pipeline Leak Detection and Theft Detection Using Rarefaction Waves Authors: Dr Alex Souza de Joode, VP International Operations; ATMOS International, UK. Andrew
Force Protection Joint Experiment (FPJE) Battlefield Anti-Intrusion System (BAIS) Sensors Data Analysis and Filtering Metrics
 Force Protection Joint Experiment (FPJE) Battlefield Anti-Intrusion System (BAIS) Sensors Data Analysis and Filtering Metrics C.M. Barngrover, R.T. Laird, T.A. Kramer, J.R. Cruickshanks, S.H. Cutler Space
Force Protection Joint Experiment (FPJE) Battlefield Anti-Intrusion System (BAIS) Sensors Data Analysis and Filtering Metrics C.M. Barngrover, R.T. Laird, T.A. Kramer, J.R. Cruickshanks, S.H. Cutler Space
DeltaV Analyze. Introduction. Benefits. Continuous automated DeltaV System alarm system performance monitoring
 DeltaV Distributed Control System Product Data Sheet December 2016 DeltaV Analyze Continuous automated DeltaV System alarm system performance monitoring Trends of alarms, events, and user actions Identification
DeltaV Distributed Control System Product Data Sheet December 2016 DeltaV Analyze Continuous automated DeltaV System alarm system performance monitoring Trends of alarms, events, and user actions Identification
Supervisor Standard Edition
 Supervisor Standard Edition Installation Manual Heat-Tracing Controller Configuration and Monitoring Software INSTALL-119 (Europe) 1 / 18 Contents Section 1 Introduction...3 1.1 Welcome...3 1.2 Vital Information...3
Supervisor Standard Edition Installation Manual Heat-Tracing Controller Configuration and Monitoring Software INSTALL-119 (Europe) 1 / 18 Contents Section 1 Introduction...3 1.1 Welcome...3 1.2 Vital Information...3
Wet Bulb Thermo-Hygrometer Datalogger
 USER GUIDE Wet Bulb Thermo-Hygrometer Datalogger Plus Dew Point Temperature Model WB200 Introduction Thank you for selecting the Extech Instruments WB200 Thermo-Hygrometer Datalogger with Dew Point and
USER GUIDE Wet Bulb Thermo-Hygrometer Datalogger Plus Dew Point Temperature Model WB200 Introduction Thank you for selecting the Extech Instruments WB200 Thermo-Hygrometer Datalogger with Dew Point and
A new view on building protection. Cerberus DMS makes building protection smarter, easier and more flexible. Answers for infrastructure.
 A new view on building protection Cerberus DMS makes building protection smarter, easier and more flexible. Answers for infrastructure. Safety made easier. As an easy-to-use system with a single point
A new view on building protection Cerberus DMS makes building protection smarter, easier and more flexible. Answers for infrastructure. Safety made easier. As an easy-to-use system with a single point
Microgrid Fault Protection Based on Symmetrical and Differential Current Components
 Microgrid Fault Protection Based on Symmetrical and Differential Current Components Prepared for Public Interest Energy Research California Energy Commission Prepared by Hassan Nikkhajoei and Robert H.
Microgrid Fault Protection Based on Symmetrical and Differential Current Components Prepared for Public Interest Energy Research California Energy Commission Prepared by Hassan Nikkhajoei and Robert H.
Intrusion Detection: Eliminating False Alarms
 Intrusion Detection: Eliminating False Alarms MAFTIA Final Review Andreas Wespi 18/19 February 2003 Newcastle Overview! MAFTIA and Intrusion Detection! Eliminating False Alarms! Demonstrator of an Intrusion-Tolerant
Intrusion Detection: Eliminating False Alarms MAFTIA Final Review Andreas Wespi 18/19 February 2003 Newcastle Overview! MAFTIA and Intrusion Detection! Eliminating False Alarms! Demonstrator of an Intrusion-Tolerant
LYNX CE CENTRAL CONTROL FOR OSMAC. General Specifications
 LYNX CE CENTRAL CONTROL FOR OSMAC General Specifications Number of satellites: Up to 255 Number of satellite stations: up to 16,320 Number of Courses: 3 Number of holes per course: 48 Number of holes per
LYNX CE CENTRAL CONTROL FOR OSMAC General Specifications Number of satellites: Up to 255 Number of satellite stations: up to 16,320 Number of Courses: 3 Number of holes per course: 48 Number of holes per
CONSERVATION PLAN BASED ON THE CONCEPT OF INTEGRITY
 CONSERVATION PLAN BASED ON THE CONCEPT OF INTEGRITY Y. N. Yen a C. F. Cheng a, * a China University of Technology, 56 Sec. 3 Shin Long Rd., 116 Taipei, Taiwan - (alexyen, aabbyy)@ cute.edu.tw KEY WORDS:
CONSERVATION PLAN BASED ON THE CONCEPT OF INTEGRITY Y. N. Yen a C. F. Cheng a, * a China University of Technology, 56 Sec. 3 Shin Long Rd., 116 Taipei, Taiwan - (alexyen, aabbyy)@ cute.edu.tw KEY WORDS:
Estimating the Level of Free Riders in the Refrigerator Buy-Back Program
 Estimating the Level of Free Riders in the Refrigerator Buy-Back Program Diane M. Fielding, B.C. Hydro An impact evaluation, conducted in 1993 on B.C. Hydro s Refrigerator Buy-Back Program, employed an
Estimating the Level of Free Riders in the Refrigerator Buy-Back Program Diane M. Fielding, B.C. Hydro An impact evaluation, conducted in 1993 on B.C. Hydro s Refrigerator Buy-Back Program, employed an
Before you install ProSeries Express Edition software for network use
 Before you install ProSeries Express Edition software for network use The following pages describe system requirements and other information you need to know before installing ProSeries Express Edition
Before you install ProSeries Express Edition software for network use The following pages describe system requirements and other information you need to know before installing ProSeries Express Edition
Alarm Management Plan
 John E. Bogdan, Susan F. Booth, & David P. Garcia Abstract Why prepare an Alarm Management Plan just to meet PHMSA requirements (49 CFR Parts 192.631 and 195.446) when, for essentially the same effort,
John E. Bogdan, Susan F. Booth, & David P. Garcia Abstract Why prepare an Alarm Management Plan just to meet PHMSA requirements (49 CFR Parts 192.631 and 195.446) when, for essentially the same effort,
Compact Product Suite Compact HMI 6.0 Overview ABB
 Compact Product Suite Compact HMI 6.0 Overview ABB 2 OVERVIEW COMPACT HMI VERSION 6.0 Compact HMI A feature-rich human-machine interface Another feature is the high performance prefabricated, reusable
Compact Product Suite Compact HMI 6.0 Overview ABB 2 OVERVIEW COMPACT HMI VERSION 6.0 Compact HMI A feature-rich human-machine interface Another feature is the high performance prefabricated, reusable
White Paper: Video/Audio Analysis Technology. hanwhasecurity.com
 White Paper: Video/Audio Analysis Technology hanwhasecurity.com Contents 1. Preface p. 2 2. Hanwha Techwin's Analysis Technology 2.1 Tampering Detection p. 3 2.2 Face Detection p. 3 2.3 IVA (Intelligent
White Paper: Video/Audio Analysis Technology hanwhasecurity.com Contents 1. Preface p. 2 2. Hanwha Techwin's Analysis Technology 2.1 Tampering Detection p. 3 2.2 Face Detection p. 3 2.3 IVA (Intelligent
Energy Savings Potential of Passive Chilled Beam System as a Retrofit Option for Commercial Buildings in Different Climates
 Purdue University Purdue e-pubs International High Performance Buildings Conference School of Mechanical Engineering 2014 Energy Savings Potential of Passive Chilled Beam System as a Retrofit Option for
Purdue University Purdue e-pubs International High Performance Buildings Conference School of Mechanical Engineering 2014 Energy Savings Potential of Passive Chilled Beam System as a Retrofit Option for
AN ANALYSIS OF THE PERFORMANCE OF RESIDENTIAL SMOKE DETECTION TECHNOLOGIES UTILIZING THE CONCEPT OF RELATIVE TIME
 AN ANALYSIS OF THE PERFORMANCE OF RESIDENTIAL SMOKE DETECTION TECHNOLOGIES UTILIZING THE CONCEPT OF RELATIVE TIME Elizabeth L. Milarcik, Stephen M. Olenick*, and Richard J. Roby Combustion Science & Engineering,
AN ANALYSIS OF THE PERFORMANCE OF RESIDENTIAL SMOKE DETECTION TECHNOLOGIES UTILIZING THE CONCEPT OF RELATIVE TIME Elizabeth L. Milarcik, Stephen M. Olenick*, and Richard J. Roby Combustion Science & Engineering,
Frameworx 16.0 Product Conformance Certification Report CENX V6.1
 Frameworx 16.0 Product Conformance Certification Report CENX V6.1 Version 1.0 January 2017 Table of Contents List of Figures... 0 List of Tables... 0 1 Introduction... 1 1.1 Executive Summary... 1 2 Product
Frameworx 16.0 Product Conformance Certification Report CENX V6.1 Version 1.0 January 2017 Table of Contents List of Figures... 0 List of Tables... 0 1 Introduction... 1 1.1 Executive Summary... 1 2 Product
Effective Use of Statistical Models to Establish and Update Vibration Alarm
 Knowledge Base Article Effective Use of Statistical Models to Establish and Update Vibration Alarm Article ID: NK-1000-0468 Publish Date: 27 Feb 2015 Article Status: Article Type: Required Action: Approved
Knowledge Base Article Effective Use of Statistical Models to Establish and Update Vibration Alarm Article ID: NK-1000-0468 Publish Date: 27 Feb 2015 Article Status: Article Type: Required Action: Approved
Leak Detection Program Management (RP 1175) April 24-26, 2018 St. Louis, Missouri
 Leak Detection Program Management (RP 1175) April 24-26, 2018 St. Louis, Missouri Agenda Introduction Part 1 - Part 2 - Part 3 - Presentation from Chris Hoidal (PHMSA) Audience Q/A (~5 minutes) Presentation
Leak Detection Program Management (RP 1175) April 24-26, 2018 St. Louis, Missouri Agenda Introduction Part 1 - Part 2 - Part 3 - Presentation from Chris Hoidal (PHMSA) Audience Q/A (~5 minutes) Presentation
Improved occupancy detection accuracy using PIR and door sensors for a smart thermostat
 Improved occupancy detection accuracy using and door sensors for a smart thermostat Sun Ho Kim 1, Hyeun Jun Moon 1, Young Ran Yoon 1 1 Department of Architectural Engineering, Dankook University, Yongin,
Improved occupancy detection accuracy using and door sensors for a smart thermostat Sun Ho Kim 1, Hyeun Jun Moon 1, Young Ran Yoon 1 1 Department of Architectural Engineering, Dankook University, Yongin,
Presentation Flow. PNNI Routing Protocol Hello Protocol. What is PNNI?
 Performance Evaluation of Multiple Criteria Routing Algorithms in Large PNNI ATM Network Phongsak Prasithsangaree Master s Thesis Defense May 22, 2000 Presentation Flow What is PNNI? Problem statement
Performance Evaluation of Multiple Criteria Routing Algorithms in Large PNNI ATM Network Phongsak Prasithsangaree Master s Thesis Defense May 22, 2000 Presentation Flow What is PNNI? Problem statement
Fike set out to develop a better understanding of the power density trends in data centers around the world.
 Fike set out to develop a better understanding of the power density trends in data centers around the world. We wanted to learn how increasing power density translates into energy augmented combustion.
Fike set out to develop a better understanding of the power density trends in data centers around the world. We wanted to learn how increasing power density translates into energy augmented combustion.
Brine Generation Study
 DOE/WIPP 00-2000 Brine Generation Study April 2000 Waste Isolation Pilot Plant Carlsbad, New Mexico Processing and final preparation of this report was performed by the Waste Isolation Pilot Plant Management
DOE/WIPP 00-2000 Brine Generation Study April 2000 Waste Isolation Pilot Plant Carlsbad, New Mexico Processing and final preparation of this report was performed by the Waste Isolation Pilot Plant Management
USER APPROVAL OF SAFETY INSTRUMENTED SYSTEM DEVICES
 USER APPROVAL OF SAFETY INSTRUMENTED SYSTEM DEVICES Angela E. Summers, Ph.D., P.E, President Susan Wiley, Senior Consultant SIS-TECH Solutions, LP Process Plant Safety Symposium, 2006 Spring National Meeting,
USER APPROVAL OF SAFETY INSTRUMENTED SYSTEM DEVICES Angela E. Summers, Ph.D., P.E, President Susan Wiley, Senior Consultant SIS-TECH Solutions, LP Process Plant Safety Symposium, 2006 Spring National Meeting,
SCHULTE & ASSOCIATES Building Code Consultants 880D Forest Avenue Evanston, IL /
 SCHULTE & ASSOCIATES Building Code Consultants 880D Forest Avenue Evanston, IL 60202 fpeschulte@aol.com 504/220-7475 A CRITIQUE OF HUGHES ASSOCIATES, INC. PAPER TITLED: Analysis of the Performance of Ganged
SCHULTE & ASSOCIATES Building Code Consultants 880D Forest Avenue Evanston, IL 60202 fpeschulte@aol.com 504/220-7475 A CRITIQUE OF HUGHES ASSOCIATES, INC. PAPER TITLED: Analysis of the Performance of Ganged
Proxemic Interactions in Ubiquitous Computing Ecologies
 Proxemic Interactions in Ubiquitous Computing Ecologies Figure 1. People, digital devices, and non-digital physical objects in a ubiquitous computing ecology. Nicolai Marquardt Interactions Lab, University
Proxemic Interactions in Ubiquitous Computing Ecologies Figure 1. People, digital devices, and non-digital physical objects in a ubiquitous computing ecology. Nicolai Marquardt Interactions Lab, University
The Rise of Tier 2 Testing
 The Rise of Tier 2 Testing Why enterprises today demand better visibility into their fiber infrastructure Unprecedented demand for more bandwidth, faster network speeds, lower latency, and improved data
The Rise of Tier 2 Testing Why enterprises today demand better visibility into their fiber infrastructure Unprecedented demand for more bandwidth, faster network speeds, lower latency, and improved data
Crop Management Details Start from Parameters settings Emergence Planting Seed brand: Settings Parameter settings Hybrid-specific Generic
 2.3.4. Crop Management Details Start from: A Hybrid-Maize simulation can start from either planting or emergence. Make that choice and select the appropriate date from the month/date boxes on the right.
2.3.4. Crop Management Details Start from: A Hybrid-Maize simulation can start from either planting or emergence. Make that choice and select the appropriate date from the month/date boxes on the right.
KELTRON LS 7000 ALARM MANAGEMENT SYSTEM Keltron Alarm Monitoring, Dispatch, and Reporting Software
 KELTRON LS 7000 ALARM MANAGEMENT SYSTEM Keltron Alarm Monitoring, Dispatch, and Reporting Software OVERVIEW The Keltron LS 7000 Alarm Management System software and computers make up the dispatch portion
KELTRON LS 7000 ALARM MANAGEMENT SYSTEM Keltron Alarm Monitoring, Dispatch, and Reporting Software OVERVIEW The Keltron LS 7000 Alarm Management System software and computers make up the dispatch portion
FIRST YEAR RECOVERY FOLLOWING A SIMULATED DROUGHT IN WALNUT. D. A. Goldhamer, R. Beede, S. Sibbett, D. Ramos, D. Katayama, S. Fusi, and R.
 FIRST YEAR RECOVERY FOLLOWING A SIMULATED DROUGHT IN WALNUT D. A. Goldhamer, R. Beede, S. Sibbett, D. Ramos, D. Katayama, S. Fusi, and R. Jones ABSTRACT A one year drought was simulated in on mature conventionally
FIRST YEAR RECOVERY FOLLOWING A SIMULATED DROUGHT IN WALNUT D. A. Goldhamer, R. Beede, S. Sibbett, D. Ramos, D. Katayama, S. Fusi, and R. Jones ABSTRACT A one year drought was simulated in on mature conventionally
Chapter 5 Standards and Methodologies to Measure E-waste
 Chapter 5 Standards and Methodologies to Measure E-waste Illustration 5.1: Life cycle of EEE into e-waste, and the most common e-waste management scenarios Delivery NEW SALES! Sales Business use Private
Chapter 5 Standards and Methodologies to Measure E-waste Illustration 5.1: Life cycle of EEE into e-waste, and the most common e-waste management scenarios Delivery NEW SALES! Sales Business use Private
A Forest Fire Warning Method Based on Fire Dangerous Rating Dan Wang 1, a, Lei Xu 1, b*, Yuanyuan Zhou 1, c, Zhifu Gao 1, d
 International Conference on Applied Science and Engineering Innovation (ASEI 2015) A Forest Fire Warning Method Based on Fire Dangerous Rating Dan Wang 1, a, Lei Xu 1, b*, Yuanyuan Zhou 1, c, Zhifu Gao
International Conference on Applied Science and Engineering Innovation (ASEI 2015) A Forest Fire Warning Method Based on Fire Dangerous Rating Dan Wang 1, a, Lei Xu 1, b*, Yuanyuan Zhou 1, c, Zhifu Gao
Using BIM model for Fire Emergency Evacuation Plan
 Using BIM model for Fire Emergency Evacuation Plan Adam Stančík 1,, Roman Macháček 2, and Jiří Horák 1 1 Brno University of Technology, Institute of Computer Aided Engineering and Computer Science, 602
Using BIM model for Fire Emergency Evacuation Plan Adam Stančík 1,, Roman Macháček 2, and Jiří Horák 1 1 Brno University of Technology, Institute of Computer Aided Engineering and Computer Science, 602
DETECTING IT AND LIGHTING LOADS USING COMMON- MODE CONDUCTED EMI SIGNALS IIIT-DELHI (INDIA)
 DETECTING IT AND LIGHTING LOADS USING COMMON- MODE CONDUCTED EMI SIGNALS MANOJ GULATI SHOBHA SUNDAR RAM ANGSHUL MAJUMDAR AMARJEET SINGH IIIT-DELHI (INDIA) 1 May 15 th, 2016 WHY IT AND LIGHTING LOADS ARE
DETECTING IT AND LIGHTING LOADS USING COMMON- MODE CONDUCTED EMI SIGNALS MANOJ GULATI SHOBHA SUNDAR RAM ANGSHUL MAJUMDAR AMARJEET SINGH IIIT-DELHI (INDIA) 1 May 15 th, 2016 WHY IT AND LIGHTING LOADS ARE
MODULATING CONTROL OF LOW NO X BURNERS
 MODULATING CONTROL OF LOW NO X BURNERS ABSTRACT Manufacturers of today s wall-fired low NO X burners (LNB) recommend a single-position secondary air volume control for in-service burners. Air register
MODULATING CONTROL OF LOW NO X BURNERS ABSTRACT Manufacturers of today s wall-fired low NO X burners (LNB) recommend a single-position secondary air volume control for in-service burners. Air register
Scholars Research Library. The Role of Plant Clinic in Protecting Vertical Urban Green Spaces in Tehran
 Available online at www.scholarsresearchlibrary.com Annals of Biological Research, 2011, 2 (3) :255-261 (http://scholarsresearchlibrary.com/archive.html) ISSN 0976-1233 CODEN (USA): ABRNBW The Role of
Available online at www.scholarsresearchlibrary.com Annals of Biological Research, 2011, 2 (3) :255-261 (http://scholarsresearchlibrary.com/archive.html) ISSN 0976-1233 CODEN (USA): ABRNBW The Role of
A Network Theory Framework for Urban Cultural Heritage Conservation. Manal Ginzarly LEMA, Université de Liège
 A Network Theory Framework for Urban Cultural Heritage Conservation Manal Ginzarly LEMA, Université de Liège Objective Develop an ecological approach to the integration of heritage conservation and urban
A Network Theory Framework for Urban Cultural Heritage Conservation Manal Ginzarly LEMA, Université de Liège Objective Develop an ecological approach to the integration of heritage conservation and urban
Functional Versus Schematic Overview Displays: Impact on Operator Situation Awareness in Process Monitoring
 Functional Versus Schematic Overview Displays: Impact on Operator Situation Awareness in Process Monitoring Anand Tharanathan Honeywell Advanced Technology Golden Valley, MN Dal Vernon Reising Lone Tree,
Functional Versus Schematic Overview Displays: Impact on Operator Situation Awareness in Process Monitoring Anand Tharanathan Honeywell Advanced Technology Golden Valley, MN Dal Vernon Reising Lone Tree,
Effective Biomass Moisture Control
 Effective Biomass Moisture Control By John Robinson Drying Technology, Inc P.O. Box 1535 Silsbee, TX 77656 409-385-6422/6537fax john@moistureconrols.com www.moisturecontrols.com Presented at The Timber
Effective Biomass Moisture Control By John Robinson Drying Technology, Inc P.O. Box 1535 Silsbee, TX 77656 409-385-6422/6537fax john@moistureconrols.com www.moisturecontrols.com Presented at The Timber
New requirements for IEC best practice compliance
 New requirements for IEC 61511 best practice compliance Proof testing and a SIL study may no longer be enough by Sven Grone Schneider Electric Safety Services Practice Leader Executive summary Since its
New requirements for IEC 61511 best practice compliance Proof testing and a SIL study may no longer be enough by Sven Grone Schneider Electric Safety Services Practice Leader Executive summary Since its
Developing a Fire Test Strategy for Storage Protection Under Sloped Ceilings
 Developing a Fire Test Strategy for Storage Protection Under Sloped Ceilings Justin A. Geiman, Noah L. Ryder Fire & Risk Alliance, Rockville, MD, USA André W. Marshall Custom Spray Solutions, Silver Spring,
Developing a Fire Test Strategy for Storage Protection Under Sloped Ceilings Justin A. Geiman, Noah L. Ryder Fire & Risk Alliance, Rockville, MD, USA André W. Marshall Custom Spray Solutions, Silver Spring,
Pepperl+Fuchs GmbH Lilienthalstrasse Mannheim Germany
 PR-2010-1124PA-eng-Fieldbus planning Pepperl+Fuchs GmbH Lilienthalstrasse 200 68307 Mannheim Germany Please indicate the following contact information for publication: Tel.: +49 621 776-2222, Fax: +49
PR-2010-1124PA-eng-Fieldbus planning Pepperl+Fuchs GmbH Lilienthalstrasse 200 68307 Mannheim Germany Please indicate the following contact information for publication: Tel.: +49 621 776-2222, Fax: +49
Using Neural Networks for Alarm Correlation in Cellular Phone Networks
 Using Neural Networks for Alarm Correlation in Cellular Phone Networks Hermann Wietgrefe, Klaus-Dieter Tuchs, Klaus Jobmann, Guido Carls, Peter Fröhlich*, Wolfgang Nejdl*, Sebastian Steinfeld* Institut
Using Neural Networks for Alarm Correlation in Cellular Phone Networks Hermann Wietgrefe, Klaus-Dieter Tuchs, Klaus Jobmann, Guido Carls, Peter Fröhlich*, Wolfgang Nejdl*, Sebastian Steinfeld* Institut
Landscape Conservation Design June, 2014
 Designing Sustainable Landscapes in the Northeast A project of the North Atlantic Landscape Conservation Cooperative & Northeast Climate Science Center June, 2014 Adaptive Establish Conservation Goals
Designing Sustainable Landscapes in the Northeast A project of the North Atlantic Landscape Conservation Cooperative & Northeast Climate Science Center June, 2014 Adaptive Establish Conservation Goals
Customized, End-to-End Facility Monitoring
 Datasheet icontrol Customized, End-to-End Facility Monitoring Stay in control with customizable monitoring and interfaces. A highly adaptable television signal and network monitoring system, icontrol from
Datasheet icontrol Customized, End-to-End Facility Monitoring Stay in control with customizable monitoring and interfaces. A highly adaptable television signal and network monitoring system, icontrol from
ACTIVE ACOUSTIC METHODOLOGY FOR DETECTING SEWER LINE OBSTRUCTIONS
 Pre-Print NC-AWWA InfoSense, Inc. P a g e 1 ACTIVE ACOUSTIC METHODOLOGY FOR DETECTING SEWER LINE OBSTRUCTIONS Ivan Howitt InfoSense, Inc.* John Fishburne Charlotte-Mecklenburg Utilities Brian Wilson Charlotte-Mecklenburg
Pre-Print NC-AWWA InfoSense, Inc. P a g e 1 ACTIVE ACOUSTIC METHODOLOGY FOR DETECTING SEWER LINE OBSTRUCTIONS Ivan Howitt InfoSense, Inc.* John Fishburne Charlotte-Mecklenburg Utilities Brian Wilson Charlotte-Mecklenburg
Slope stability assessment
 Engineering manual No. 25 Updated: 03/2018 Slope stability assessment Program: FEM File: Demo_manual_25.gmk The objective of this manual is to analyse the slope stability degree (factor of safety) using
Engineering manual No. 25 Updated: 03/2018 Slope stability assessment Program: FEM File: Demo_manual_25.gmk The objective of this manual is to analyse the slope stability degree (factor of safety) using
January 21, Re: NOPR to Revise Water Heater Test Procedures. Docket No. EERE 2011 BT-TP Dear Ms. Edwards,
 Ms. Brenda Edwards U.S. Department of Energy Building Technologies Program, MS EE-2J EERE-2011-BT-TP-0042 1000 Independence Avenue, S.W. Washington, D.C. 20585-0121 Re: NOPR to Revise Water Heater Test
Ms. Brenda Edwards U.S. Department of Energy Building Technologies Program, MS EE-2J EERE-2011-BT-TP-0042 1000 Independence Avenue, S.W. Washington, D.C. 20585-0121 Re: NOPR to Revise Water Heater Test
Real-Time Root Cause Analysis for Complex Technical Systems
 Real-Time Root Cause Analysis for Complex Technical Systems Jan Eric Larsson, Joseph DeBor IEEE HPRCT Monterey, CA, August 29 th 2007 Handling Alarm Cascades Root cause analysis: find the initiating events
Real-Time Root Cause Analysis for Complex Technical Systems Jan Eric Larsson, Joseph DeBor IEEE HPRCT Monterey, CA, August 29 th 2007 Handling Alarm Cascades Root cause analysis: find the initiating events
1. EXPLORE A CAREER PLAN IN DESIGN AND MERCHANDISING
 21 st Century Learning Interior Design and Merchandising High School Interior Design and Merchandising is an elective that focuses on creating beauty, comfort and convenience in rooms and homes. The principles
21 st Century Learning Interior Design and Merchandising High School Interior Design and Merchandising is an elective that focuses on creating beauty, comfort and convenience in rooms and homes. The principles
ICONE DRAFT Proceedings of the 16th International Conference on Nuclear Engineering ICONE16 May 11-15, 2008, Orlando, Florida, USA
 DRAFT Proceedings of the 16th International Conference on Nuclear Engineering ICONE16 May 11-15, 2008, Orlando, Florida, USA ICONE16-48187 THERMAL CYCLE EVALUATION FOR FEEDWATER HEATER OUT OF SERVICE CONDITION
DRAFT Proceedings of the 16th International Conference on Nuclear Engineering ICONE16 May 11-15, 2008, Orlando, Florida, USA ICONE16-48187 THERMAL CYCLE EVALUATION FOR FEEDWATER HEATER OUT OF SERVICE CONDITION
The Game of Life Safety Procurement
 The Game of Life Safety Procurement During a recent search on the internet I discovered countless blogs broadcasting hate mail about fire alarm systems. Some singled out their smoke alarms; others lamented
The Game of Life Safety Procurement During a recent search on the internet I discovered countless blogs broadcasting hate mail about fire alarm systems. Some singled out their smoke alarms; others lamented
DEFECTOVISION IR. Non-Destructive Testing of Steel Billets and Tubes
 DEFECTOVISION IR Non-Destructive Testing of Steel Billets and Tubes FOERSTER DIVISION TESTING SYSTEMS (TS) The Company FOERSTER is a global technology leader for nondestructive testing of metallic materials.
DEFECTOVISION IR Non-Destructive Testing of Steel Billets and Tubes FOERSTER DIVISION TESTING SYSTEMS (TS) The Company FOERSTER is a global technology leader for nondestructive testing of metallic materials.
Alarms Updated 03/26/2018
 Updated 03/26/2018 Table of Contents Alarms Alarms in OneView...1 Types of Alarms...1 Setting up Alarms...2 Alarm Configuration...4 Customize Alarm Parameters...5 List of Configured Alarms...7 Acknowledging
Updated 03/26/2018 Table of Contents Alarms Alarms in OneView...1 Types of Alarms...1 Setting up Alarms...2 Alarm Configuration...4 Customize Alarm Parameters...5 List of Configured Alarms...7 Acknowledging
Integrating fire-spread and household-level trigger modeling to stage wildfire evacuation warnings
 Integrating fire-spread and household-level trigger modeling to stage wildfire evacuation warnings Dapeng. Li 1, Thomas. J. Cova 1, Philip. E. Dennison 1 1 Department of Geography, University of Utah,
Integrating fire-spread and household-level trigger modeling to stage wildfire evacuation warnings Dapeng. Li 1, Thomas. J. Cova 1, Philip. E. Dennison 1 1 Department of Geography, University of Utah,
Low Temperature Separation Systems. Separation Process
 Low Temperature Separation Systems Robin Smith and Sonia Farrokhpanah Centre for Process Integration, School of Chemical Engineering and Analytical Science, University of Manchester, Manchester U.K., M60
Low Temperature Separation Systems Robin Smith and Sonia Farrokhpanah Centre for Process Integration, School of Chemical Engineering and Analytical Science, University of Manchester, Manchester U.K., M60
FREQUENCY ENHANCEMENT OF DUAL-JUNCTION THERMOCOUPLE PROBES
 XXIII Biannual Symposium on Measuring Techniques in Turbomachinery Transonic and Supersonic Flow in FREQUENCY ENHANCEMENT OF DUAL-JUNCTION THERMOCOUPLE PROBES James Braun Purdue University Indiana, United
XXIII Biannual Symposium on Measuring Techniques in Turbomachinery Transonic and Supersonic Flow in FREQUENCY ENHANCEMENT OF DUAL-JUNCTION THERMOCOUPLE PROBES James Braun Purdue University Indiana, United
CROWD-SOURCED REMOTE ASSESSMENTS OF REGIONAL-SCALE POST-DISASTER DAMAGE
 Eleventh U.S. National Conference on Earthquake Engineering Integrating Science, Engineering & Policy June 25-29, 2018 Los Angeles, California CROWD-SOURCED REMOTE ASSESSMENTS OF REGIONAL-SCALE POST-DISASTER
Eleventh U.S. National Conference on Earthquake Engineering Integrating Science, Engineering & Policy June 25-29, 2018 Los Angeles, California CROWD-SOURCED REMOTE ASSESSMENTS OF REGIONAL-SCALE POST-DISASTER
PRESENTS AQUADUCT AUTOMATED WATER-LEAK MONITORING SYSTEM A KINGPIN TECHNOLOGY
 PRESENTS AQUADUCT AUTOMATED WATER-LEAK MONITORING SYSTEM A KINGPIN TECHNOLOGY INTRODUCING THE INNOVATIVE NEW TECHNOLOGY FOR THE DETECTION OF LEAKS IN WATER NETWORKS. SA WATER CRISIS the rising tide The
PRESENTS AQUADUCT AUTOMATED WATER-LEAK MONITORING SYSTEM A KINGPIN TECHNOLOGY INTRODUCING THE INNOVATIVE NEW TECHNOLOGY FOR THE DETECTION OF LEAKS IN WATER NETWORKS. SA WATER CRISIS the rising tide The
Section 3: How much food waste can be collected for recycling?
 Household food waste collections guide This publication updates the 2009 guide and pulls together the findings from more recent studies and pilots conducted by WRAP and others. Through the various sections,
Household food waste collections guide This publication updates the 2009 guide and pulls together the findings from more recent studies and pilots conducted by WRAP and others. Through the various sections,
Before you install ProSeries software for network use
 Before you install ProSeries software for network use The following pages describe system requirements and other information you need to know before installing ProSeries software for network use. Important:
Before you install ProSeries software for network use The following pages describe system requirements and other information you need to know before installing ProSeries software for network use. Important:
