1.1 Ensure the room is in the ACCESS state. Workstation indicates zone is in ACCESS state.
|
|
|
- Ruth Reeves
- 5 years ago
- Views:
Transcription
1 Title: Arming/Disarming Keypad Test Objective: Verify device is installed using acceptable standards and practices, communicates properly with the IDS, and provides proper protection of assets and meets or exceeds the contract performance specification. Applicability: Intrusion Detection System (IDS) 1. Assumes a room with an arming/disarming keypad on the secure side, a Balanced Magnetic Switch (BMS) on the door, and motion sensor coverage. 2. Program alarm delays only for those sensors that would activate prior to the user reaching the keypad and entering the disarm code. All other sensors operate without delay. 3. Real-time voice communications between the workstation operator and the field technician is required. 1.0 Arming Test 1.1 Ensure the room is in the ACCESS state. Workstation indicates zone is in ACCESS state. 1.2 Input correct arming code. No alarms are received at the workstation. Keypad and system both show SECURE. 1.3 Exit within the appropriate delay period. No alarms are received at the workstation. Zone is SECURE. 2.0 Disarming Test 2.1 Ensure the room is in the SECURE state. Workstation indicates zone is in SECURE state. 2.2 Enter the secure space. BMS and motion sensors show activity, but no alarms are received at the workstation. 2.3 Enter the correct disarming code within the delay period. 2.4 Walk through the zone and attempt to activate each sensor that has been disarmed. 2.5 Attempt to activate 24/7 alarms (such as emergency exits). No alarms are received at the workstation. Keypad and system both show ACCESS. No alarms are received at the workstation. Alarm received at workstation. 2.6 Clear the alarm at the workstation. The active alarm queue is empty. 3.0 Incorrect Code Test - Arming 3.1 Ensure the room is in the ACCESS state. Workstation indicates zone is in ACCESS state. 3.2 Input an incorrect arming code. No alarms are received at the workstation. Keypad alerts user that system was not armed. Keypad and system both show ACCESS. 3.3 Repeat 3.2 until the maximum number of allowed attempts is reached. Alarm received at workstation. 3.4 Clear the alarm at the workstation. The active alarm queue is empty.
2 4.0 Incorrect Code Test - Disarming 4.1 Enter the secure space. BMS and motion sensors show activity, but no alarms are received at the workstation. 4.2 Enter an incorrect disarming code. Keypad alerts user that system did not disarm. Keypad and system both show SECURE. 4.3 Repeat 4.2 until the maximum number of allowed attempts is reached within the allotted time. Workstation shows keypad alarm. 4.4 Clear the alarm at the workstation. The active alarm queue is empty. 5.0 Delayed Exit After Arming Test 5.1 Enter the correct arming code. No alarms are received at the workstation. Keypad and workstation both show SECURE. 5.2 Exit the secure space after the programmed delay period ends. Intrusion alarm received at the workstation after the alarm is received. 5.3 Clear the alarm at the workstation. The active alarm queue is empty. 6.0 Delayed Disarming Test 6.1 Enter the armed space. BMS and motion sensors show activity, but no alarms are received at the workstation. 6.2 Wait for the delay period to end. Intrusion alarm is received at the workstation. 6.3 Enter the correct disarming code. Keypad and workstation both show ACCESS. Alarms are still active. 6.4 Clear the alarm at the workstation. The active alarm queue is empty. 7.0 Duress Code Test 7.1 Ensure the room is in the SECURE state. Workstation indicates zone is in SECURE state. 7.2 Enter the secure space. BMS and motion sensors show activity, but no alarms are received at the workstation. 7.3 Enter the duress code within the delay period. Alarm is received at the workstation. Keypad shows ACCESS. 7.4 Clear the alarm at the workstation. The active alarm queue is empty.
3 Title: Magnetic Lock Objective: Verify system is installed using acceptable standards and practices, communicates properly, and provides proper protection of assets and meets or exceeds the contract performance specification. Applicability: Doors and gates. Magnetic Locks. Electronic Entry Control Systems (EECS). NFPA and life safety codes. 1. These procedures are based on interior door with card reader for entrance. This magnetic lock is installed in a fail secure configuration. On the secure side, the door has a magnetic lock with door position switch, PIR REX (Passive Infrared Request to Exit) sensor above the door, and a Push To Exit button on the wall (this is as a backup exit system). 2. All standard access control tests are needed in addition to this test. The intent of this test is to ensure egress due to the dangers of magnetic locks. 3. Ensure that the magnetic lock is installed correctly: it is flush with the closer, is on the handle side of the door, and the closer does not slam the door. 4. Assumes only one credential is required for entry (i.e. card only). 5. The Power Failure Fail Secure Test is performed if the door is configured in Fail Secure mode (i.e. in a power fail situation, the door defaults to the locked condition). 6. Real-time voice communications between the workstation operator and the field technician is required. 7. For Steps 9.0 and 10.0, coordinate testing so that building occupants and emergency response forces along with all appropriate parties understand that testing is occurring. 1.0 Lock Test 1.1 Ensure that the door is closed and locked. Contract the operator to verify that the door is secure. 1.2 Activate the door hardware from the public side and attempt open the door. Door is locked and secure. Door does not open. No alarm received at the workstation. 2.0 PIR REX Field of View Test 2.1 Stand slightly outside of the PIR s expected field of view 2.2 Staying slightly outside of the PIR s expected field of view, walk the boundary of the PIR. PIR does not detect test subject. Lock does not release. PIR does not detect test subject. Lock does not release. 3.0 Valid Credential Test 3.1 Present a valid badge to the reader. Transaction logged. Lock releases. 3.2 Open door and enter. Door indicates as open. No alarm is received at workstation. 3.3 Close the door. Door indicates as closed. No alarm is received at workstation. Lock reactivates when door is closed. The active alarm queue is empty. 4.0 Invalid Credential Test 4.1 Present Invalid Badge to the reader. An invalid credential alarm is received at the
4 workstation. Transaction logged. Door lock does not release. 4.2 Clear the alarm at the workstation. The active alarm queue is empty. 5.0 Exit Test 5.1 Walk up to the door. PIR releases the magnetic lock. 5.2 Walk through the door. Door indicates as open at the workstation. Alarm does not activate. 5.3 Close the door. Door indicates as closed. No alarm is received at workstation. Lock reactivates when door is closed. The active alarm queue is empty. 6.0 Push-To-Exit Test 6.1 Walk up to the door and stand to the side (with hand on the Push To Exit button) until the PIR no longer detects the person trying to exit. PIR releases the magnetic lock and relocks it after appropriate time. No alarm received. 6.2 Push the Push To Exit button. Magnetic Lock releases. No alarm received. 6.3 Have person outside the room open the door. Door opens and indicates as open at the workstation. Alarm is received at workstation. 6.4 Close the door and clear the alarm queue. Door indicates as closed. Lock reactivates when door is closed. The active alarm queue is empty. 7.0 Power Failure Fail Secure Test (This procedure is for use when lock is configured in the Fail Secure mode. I.e. lock remains active when power fails.) 7.1 Disconnect AC power from the door controller. 7.2 Activate the door hardware from the public side and attempt open the door. 7.3 Attempt to exit through the door by means of the PIR REX. 7.4 Attempt to exit through the door by means of the Push To Exit button. (Stand still on the secure side of the door until the PIR disengages to do this). Door does not open. No alarm received at the workstation. Free egress is achieved. Free egress is achieved. 8.0 Power Failure Fail Safe Test (This procedure is for use when lock is configured in the Fail Safe mode. I.e. lock disengages when power fails.) 8.1 Disconnect AC power from the door controller. 8.2 Activate the door hardware from the public side and Door opens. Door forced alarm received at the
5 attempt open the door. workstation. 8.3 Attempt to exit through the door from the secure side. Free egress is achieved. 9.0 Fire Alarm Fail Secure Test (This procedure is for use when lock is tied into the fire alarm system and is configured in the Fail Secure mode. I.e. lock remains active when power fails.) 9.1 Activate the fire alarm system. 9.2 Activate the door hardware from the public side and attempt open the door. 9.3 Attempt to exit through the door by means of the PIR REX. 9.4 Attempt to exit through the door by means of the Push To Exit button. (Stand still on the secure side of the door until the PIR disengages to do this). Door does not open. No alarm received at the workstation. Free egress is achieved. Free egress is achieved Power Failure Fail Safe Test (This procedure is for use when lock is tied into the fire alarm system and is configured in the Fail Safe mode. I.e. lock disengages when power fails.) 10.1 Activate the fire alarm system Activate the door hardware from the public side and attempt open the door Attempt to exit through the door from the secure side. Door opens. Door forced alarm received at the workstation. Free egress is achieved.
6 Title: Mechanical Turnstile Objective: Verify device is installed using acceptable standards and practices, communicates properly with the Access Control System (ACS), and provides proper protection of assets and meets or exceeds the contract performance specification. Applicability: Access control systems. Examples: Perimeter gates, fence lines, remote sites. 1. These procedures assume a single-rotor mechanical turnstile with an entry card reader. Exit lane is the same as entry lane, and occupants are allowed free egress. 2. Assumes a single credential required for entry (i.e. card only). 3. Perform valid and invalid credential tests for entry. 4. The cards to be prepared prior to testing and used for these tests are as follows: Card 1: Authorized to access all areas. Card 2: Time zone restricted card. Valid for only normal duty hours. Card 3: Time zone restricted card. Valid for only non-duty hours. Card 4: Enrolled user with expired access. Card 5: Un-programmed card. Card 6: Card with insufficient access permissions. 5. For Valid Credential Tests (Step 2.0), use cards 1 and For Invalid Credential Tests (Step 3.0), use cards 3, 4, 5, and Real-time voice communications between the workstation operator and the field technician is required. 8. Perform these tests with the associated zone in the SECURE state. 9. Line Supervision, Power Fail, and Tamper Tests need to be performed in addition to these procedures. 1.0 Mechanical Test 1.1 From the unsecure side, verify that the turnstile rotor assembly is locked. Attempt to enter from the unsecure side without a credential. Turnstile does not allow access. No alarm received at the workstation. 2.0 Valid Credential Access Test (It is recommended to repeat this test at least 3 times with no failures to help ensure proper functionality) 2.1 Present a valid credential to the reader. Transaction logged at workstation. Turnstile mechanical lock releases and allows rotor assembly to turn. 2.2 Pass through the turnstile. Turnstile rotor assembly rotates to allow one person to pass through the turnstile and reactivates the mechanical lock. 3.0 Invalid Credential Access Test (It is recommended to repeat this test at least 3 times with no failures to help ensure proper functionality) 3.1 Present invalid credential to the reader. An invalid credential alarm is received at the workstation. Turnstile does not release. 3.2 Clear the alarm at the workstation. The active alarm queue is empty. 3.3 Repeat for each of the invalid credentials.
7 4.0 Egress Test (It is recommended to repeat this test at least 3 times with no failures to help ensure proper functionality) 4.1 Verify turnstile rotor assembly is locked from the unsecure side. 4.2 From the secure side, attempt to egress through the turnstile to the unsecure side. 4.3 Repeat 4.1 to ensure turnstile rotor assembly lock is active after egress. Turnstile does not allow access. No alarm received at the workstation. Turnstile rotates to allow free egress. Turnstile does not allow access. No alarm received at the workstation.
8 Title: Single Door with an Electronic Entry Control System (EECS) Objective: Verify system is installed using acceptable standards and practices, communicates properly, and provides proper protection of assets and meets or exceeds the contract performance specification. Applicability: Electronically Controlled Access Doors. These procedures are based on the system shown in UFC Figure These procedures are based on the system shown in UFC Figure Assumes 2 credentials required for entry (i.e. card and PIN). 3. The cards to be prepared prior to testing and used for these tests are as follows: Card 1: Authorized to access all areas. Card 2: Time zone restricted card. Valid for only normal duty hours. Card 3: Time zone restricted card. Valid for only non-duty hours. Card 4: Enrolled user with expired access. Card 5: Un-programmed card. Card 6: Card with insufficient access permissions. 4. For Valid Badge Tests (Steps ), use cards 1 and For Invalid Badge Tests (Step 6.0), use cards 3, 4, 5, and Real-time voice communications between the workstation operator and the field technician is required. 7. Perform these tests with the associated zone in the SECURE state. 8. Line Supervision, Power Fail, and Tamper Tests need to be performed in addition to these procedures. 9. Perform the tamper test on all tampers associated with the ACS portal. For example: tampers included in card readers, BMSs, door hardware, and junction boxes. 1.0 Nuisance Test 1.1 Ensure that the door is closed and locked. Contract the operator to verify that the door is secure. 1.2 Without activating the door hardware, push and pull on the door to attempt to trigger a nuisance alarm. Door is locked and secure. Door does not open. No alarm received at the workstation. 2.0 Mechanical Lock Test 2.1 Turn the handle and attempt to open the door. Door does not open. No alarm received at the workstation. 3.0 Door Forced Test 3.1 Either use a manual key override or open the door and fix the latch in the retracted position in such a way that the request to exit switch is not activated. Close the door. Ensure the door is shown as closed at the workstation and that the active alarm queue is empty. 3.2 Slowly open the door until the operator notifies of a door forced alarm. Door closed. Latch retracted. The active alarm queue is empty. Door forced alarm received at workstation before door has moved ¼ inch. 3.3 Return the door and all components to normal operating condition and ensure the door is closed.
9 3.4 Clear the alarm at the workstation. The active alarm queue is empty. 4.0 Valid Badge and no PIN Test 4.1 Present a valid badge to the reader without entering a PIN. Transaction logged at the workstation. Door lock does not release. 5.0 Valid Badge and Correct PIN Test (See note 4) 5.1 Present a valid badge to the reader and enter the correct PIN. Transaction logged at the workstation. Door lock releases. 5.2 Open door and enter. Door indicates as open. No alarm is received at the workstation. 5.3 Close the door. Door indicates as closed. Door lock reactivates. No alarm is received at workstation. The active alarm queue is empty. 6.0 Valid Badge and incorrect PIN Test (See note 4) 6.1 Present a valid badge to the reader, and enter an incorrect PIN. An invalid credential alarm is received at the workstation. Transaction logged. Door lock does not release. 6.2 Clear the alarm at the workstation. The active alarm queue is empty. 7.0 Invalid Badge and Correct PIN Test (See note 5) 7.1 Present Invalid Badge to the reader, and enter a valid PIN. An invalid credential alarm is received at the workstation. Transaction logged. Door lock does not release. 7.2 Clear the alarm at the workstation. The active alarm queue is empty. 8.0 Egress Test 8.1 From the secure side of the door, use the push bar to egress. Request to exit is activated. Door lock releases. Door opens. Door indicates as open at the workstation, but does not alarm. 8.2 Close the door. Door indicates as closed at the workstation. 9.0 Door Held Open Test 9.1 Open the door. 9.2 Hold door open until the operator notifies of a door held alarm. Door held alarm received at workstation within specified time. 9.3 Close the door. Door indicates as closed at the workstation. Alarm is still active. 9.4 Clear the alarm at the workstation. The active alarm queue is empty.
10
11 Title: Vehicle Gate Objective: Verify device is installed using acceptable standards and practices, communicates properly with the Access Control System (ACS), and provides proper protection of assets and meets or exceeds the contract performance specification. Applicability: Gates and site access. Access control systems. 1. These procedures are based on a system consisting of a sliding vehicle gate with entry reader, safety sensor loop, and exit sensor loop. 2. Assumes a single credential required for entry (i.e. card only). 3. Perform valid and invalid credential tests for entry. 4. The cards to be prepared prior to testing and used for these tests are as follows: Card 1: Authorized to access all areas. Card 2: Time zone restricted card. Valid for only normal duty hours. Card 3: Time zone restricted card. Valid for only non-duty hours. Card 4: Enrolled user with expired access. Card 5: Un-programmed card. Card 6: Card with insufficient access permissions. 5. For Valid Credential Tests (Step 1.0), use cards 1 and For Invalid Credential Tests (Step 2.0), use cards 3, 4, 5, and Real-time voice communications between the workstation operator and the field technician is required. 8. Line Supervision, Power Fail, and Tamper Tests need to be performed in addition to these procedures. 9. Perform these tests with the associated zone in the SECURE state. 1.0 Valid Credential Access Test 1.1 Approach gate with vehicle from the unsecure side. Gate does not open. No alarm received. 1.2 Present a valid credential to the reader. Transaction logged at workstation. Gate opens while sounding local area buzzer. 1.3 Drive through the gate. After appropriate hold time, gate closes while sounding local area buzzer. 2.0 Invalid Credential Access Test (see note 3) 2.1 Present Invalid credential to the reader. An invalid credential alarm is received at the workstation. Gate does not open. 2.2 Clear the alarm at the workstation. The active alarm queue is empty. 3.0 Safety Loop Test 3.1 Present a valid credential to the reader. Transaction logged at workstation. Gate opens while sounding local area buzzer. 3.2 Place a metal plate on the safety loop. After appropriate hold time, gate does not close. Gate sounds local area buzzer. Blocked gate alarm received at workstation. 3.3 Remove the metal plate and clear the alarm at the workstation. Gate closes while sounding local area buzzer. The active alarm queue is empty.
12 3.4 Present a valid credential to the reader. Transaction logged at workstation. Gate opens while sounding local area buzzer. 3.5 Drive into the gate path and stop. After appropriate hold time, gate does not close. Gate sounds local area buzzer. Blocked gate alarm received at workstation. 3.6 Move vehicle away from gate. Gate does closes while sounding local area buzzer. Blocked gate alarm still active at workstation. 3.7 Clear the alarm at the workstation. The active alarm queue is empty. 4.0 Vehicle Block Test 4.1 Present a valid credential to the reader. Transaction logged. Gate opens. 4.2 Stand Near the gate path, being careful not to block the path of the gate. After appropriate hold time, gate does not close. Gate sounds local area buzzer. Blocked gate alarm received at workstation. 4.3 Walk away from gate. Gate does closes while sounding local area buzzer. Blocked gate alarm still active at workstation. 4.4 Clear the alarm at the workstation. The active alarm queue is empty. 5.0 Exit Test 5.1 Drive vehicle to gate from the inside. Gate opens while sounding local area buzzer. No alarm received. 5.2 Drive through the gate. After appropriate hold time, gate closes while sounding local area buzzer.
13 Title: Image Quality (Day and Night) Objective: Verify system is installed using acceptable standards and practices, communicates properly, and meets or exceeds the contract performance specification. Applicability: Closed Circuit Television (CCTV) System, Video Management Software (VMS) 1. If this test is performed on a camera system displaying multiple cameras on the same monitor, then view the video from each camera in full screen mode. 2. Perform all tests on every camera. 3. For pan, tilt, zoom cameras, perform these tests using the default/home positions. 4. In some cases, if acceptable to end user and contract documents, it is appropriate to conduct these tests based on recorded video. 5. In locations where specific weather patterns (such as frequent rain) typically occur, consider performing the same steps from the day/night testing for that weather condition. 6. Nighttime test can be done in either pre-dawn or post-sunset, preferably not during a full moon in order to better test worst-case conditions. 7. Verify that security lighting is operating according to the site s standard operating procedures. 8. Real-time voice communications between the workstation operator and the field technician are required. 1.0 Daytime Video Quality Test 1.1 If applicable direct a test subject (person or vehicle) to enter the field of view. 1.2 Once image is brought to full screen, verify the following: The video image is clear. Test subject s movement in the video image is smooth, not choppy. 1.3 The video image is in focus. The video image is sharp, clear and distinct. 1.4 The video image is stable. The video image does not move or sway. 1.5 The video image has sufficient resolution and quality. The video image meets the contract performance specifications and is without pixilation, rolling, flickering, discoloration, and glare from light sources. 2.0 Nighttime Video Quality Test 2.1 If applicable direct a test subject (person or vehicle) to enter the field of view. 2.2 Once image is brought to full screen, verify the following: The video image is clear. Test subject s movement in the video image is smooth, not choppy. If applicable, the camera has shifted to the correct day/night mode. 2.3 The video image is in focus. The video image is sharp, clear and distinct. 2.4 The video image is stable. The video image does not move or sway.
14 2.5 The video image has sufficient resolution and quality. The video image meets the contract performance specifications and is without pixilation, rolling, flickering, discoloration, and glare from light sources. 3.0 Video Specifications Validation Test 3.1 Open the camera options menu and verify the following settings are set in accordance with the contract requirements: 3.2 Frame Rate The camera is recording at the specified frame rate. The frame rate is sufficient for the video to meet its intent. 3.3 Recording Resolution The camera is being recorded at the resolution required by the contract. 4.0 Field of View Test 4.1 Verify that the camera field of view meets the intent of the camera and satisfies the contract requirements. Required areas are covered. Video does not show significant dead space (for example: ceilings). 5.0 Video Loss Detection Test 5.1 Disconnect the camera from the video storage device. The video image goes blank, and the video lost message appears. 5.2 Reconnect the camera to the video storage device. The video image returns, and the video lost message is no longer present.
15 Title: Active Infrared Sensor Objective: Verify device is installed using acceptable standards and practices, communicates properly with the IDS, and provides proper protection of assets and meets or exceeds the contract performance specification. Applicability: Active Infrared Sensors, Photoelectric Sensors. Example: Covering doors, windows and other openings. 1. Real-time voice communications between the workstation operator and the field technician is required. 2. The field technician may need tools and a stepladder to perform the sensor tamper test. 3. Perform the intrusion test with the associated zone in the SECURE state. 4. Enable sensor motion test lights for conducting these tests. Deactivate after testing is completed. 5. Line Supervision, Power Fail, and Tamper Tests (tamper test each cover on the beam tower/array) need to be performed in addition to these procedures. 1.0 Intrusion Test 1.1 Stand outside of the detection beams and ensure that the detection path is clear. No alarms are received at the workstation. 1.2 Attempt to pass through the detection area. An intrusion alarm is received at the workstation. 1.3 Stand clear of the detection area. 1.4 Clear the intrusion alarm at the workstation. The active alarm queue is empty. 2.0 Beam Test 2.1 Block only one beam on the sensor tower/array. An intrusion alarm is received at the workstation. 2.2 Clear the intrusion alarm at the workstation. The active alarm queue is empty. 2.3 Repeat for each individual beam on the sensor tower/array.
16 Title: Balanced Magnetic Switch (BMS) Objective: Verify device is installed using acceptable standards and practices, communicates properly with the workstation, and provides proper protection of assets and meets or exceeds the contract performance specification. Applicability: Examples: Doors, gates, hatches, and operable windows. 1. Real-time voice communications between the workstation operator and the field technician is required. 2. The field technician may need tools and a stepladder to perform the BMS tamper tests. 3. Perform the nuisance test and intrusion test with the associated zone in the SECURE state. 4. Line Supervision, Power Fail, and Tamper Tests need to be performed in addition to these procedures. 1.0 Nuisance Test 1.1 Rattle or shake the door to simulate normal vibrations that might be induced by wind or other non-intrusion factors. No alarm is received at the workstation. 2.0 Intrusion Test (It is recommended to repeat this test at least 3 times with no failures to help ensure proper functionality) 2.1 Gradually open the door until an alarm occurs. (This assumes that the door alarm is not programmed with an entry delay.) An intrusion alarm is received at the workstation when greater than ¼ inch movement of the magnet in relation to the switch housing. 2.2 Close the door. 2.3 Clear the intrusion alarm at the workstation. The active alarm queue is empty.
17 Title: Beam Break Sensor Objective: Verify device is installed using acceptable standards and practices, communicates properly with the IDS, and provides proper protection of assets and meets or exceeds the contract performance specification. Applicability: Active Infrared Sensors, Photoelectric Sensors. 1. Real-time voice communications between the workstation operator and the field technician is required. 2. Make penetration attempts using methods and locations that minimize the chance of detection. 3. The field technician may need tools and a stepladder to perform the sensor tamper test. 4. Perform the intrusion test with the associated zone in the SECURE state. 5. Enable sensor motion test lights for conducting these tests. Deactivate after testing is completed. 6. Line Supervision, Power Fail, and Tamper Tests (tamper test each cover on the beam tower/array) need to be performed in addition to these procedures. 1.0 Intrusion Test Beam Cross 1.1 Stand outside of the detection beams and ensure that the detection path is clear. No alarms are received at the workstation. 1.2 Attempt to pass through the detection area. An intrusion alarm is received at the workstation. 1.3 Stand clear of the sensor detection pattern. 1.4 Clear the intrusion alarm at the workstation. The active alarm queue is empty. 2.0 Beam Test 2.1 Block only one beam on the sensor tower/array. An intrusion alarm is received at the workstation. 2.2 Clear the intrusion alarm at the workstation. The active alarm queue is empty. 2.3 Repeat for each individual beam on the sensor tower/array. 3.0 Intrusion Test Post Climb 3.1 Stand outside of the detection beams and ensure that the detection path is clear. No alarms are received at the workstation. 3.2 Attempt to climb the post (do not climb over the top). An intrusion alarm is received at the workstation. 3.4 Clear the intrusion alarm at the workstation. The active alarm queue is empty.
18 Title: Passive Infrared Sensor Curtain Type Objective: Verify device is installed using acceptable standards and practices, communicates properly with the IDS, and provides proper protection of assets and meets or exceeds the contract performance specification. Applicability: Curtain Passive Infrared Sensors 1. Real-time voice communications between the workstation operator and the field technician is required. 2. The field technician may need tools and a stepladder to perform the sensor tamper test. 3. Perform intrusion tests with a human target. All observers are to remain still and clear of the detection zone to avoid triggering the alarm and creating invalid results. 4. Prior to the start of testing, mark five intrusion lanes (or points of intrusion taking into account the sensor coverage area), with each lane probing a different portion of the sensor detection pattern. Test each intrusion lane. 5. Perform the intrusion test with the associated zone in the SECURE state. 6. Line Supervision, Power Fail, and Tamper Tests need to be performed in addition to these procedures. 1.0 Intrusion Test 1.1 Stand at the beginning of the intrusion lane and remain motionless for 20 seconds. No alarms are received at the workstation. 1.2 Step into intrusion lane. An intrusion alarm is received at the workstation. 1.3 Move out of the sensor detection pattern. 1.4 Clear the intrusion alarm at the workstation. The active alarm queue is empty. 1.5 Repeat for all lanes (note # 4).
19 Title: Dual Technology Sensor Objective: Verify device is installed using acceptable standards and practices, communicates properly with the IDS, and provides proper protection of assets and meets or exceeds the contract performance specification. Applicability: Dual technology sensors (microwave and passive infrared) 1. Real-time voice communications between the workstation operator and the field technician is required. 2. The field technician may need tools and a stepladder to perform the sensor tamper test. 3. Perform intrusion tests with a human target. All observers are to remain still and clear of the detection zone to avoid triggering the alarm and creating invalid results. 4. Prior to the start of testing, mark five intrusion lanes (or points of intrusion taking into account the sensor coverage area), with each lane probing a different portion of the sensor detection pattern. Test each intrusion lane. 5. Perform the intrusion with the associated zone in the SECURE state. 6. If multiple sensors are used to protect an alarmed zone, disable all sensors except the unit being tested. Restore all sensors to normal operation following the completion of testing. 7. If equipped, enabling sensor motion test light is useful for conducting these tests. Deactivate after testing is completed. 8. Line Supervision, Power Fail, and Tamper Tests need to be performed in addition to these procedures. 1.0 Intrusion Test 1.1 Stand at the beginning of the intrusion lane and remain motionless for 20 seconds or until test light turns off. 1.2 Take four steps at a normal walking pace along the intrusion lane and stop. No alarms are received at the workstation. An intrusion alarm is received at the workstation. 1.3 Move out of the sensor detection pattern. 1.4 Clear the intrusion alarm at the workstation. The active alarm queue is empty. 1.5 Repeat for all lanes (note # 4).
20 Title: Fence Sensor Objective: Verify device is installed using acceptable standards and practices, communicates properly with the ACS, and provides proper protection of assets and meets or exceeds the contract performance specification. Applicability: Fiber optic sensing cable, fence mounted vibration sensors, strain sensitive cable sensors. 1. Real-time voice communications between the workstation operator and the field technician is required. 2. The field technician will need a screwdriver, protective equipment and a stepladder to perform the fence sensor test. 3. Make penetration attempts using methods and locations that minimize the chance of detection. 4. Simulated cut test will use a screwdriver to tap on the fence fabric. Ensure the number of taps exceeds the event count calibration value. 5. Apply a similar force to that needed to cut the fence fabric for each simulated cut test tap. 6. If sensing cable is in the outrigger, the simulated Cut test needs to be performed on the outrigger also. 7. Do not climb over the fence or into the outrigger. 8. Establish number of tests and test locations per the requirements. 9. Line Supervision, Power Fail, and Tamper Tests need to be performed in addition to these procedures. 1.0 Intrusion Test Simulated Cut 1.1 Intruder will position themselves at the section of fence to be tested. 1.2 Tap the screwdriver at different locations on the fence panel and vertical outrigger at approximately one-second intervals. No alarms are received at the workstation. An intrusion alarm is received at the workstation. 1.3 Clear the intrusion alarm at the workstation. The active alarm queue is empty. 2.0 Intrusion Test General 2.1 Intruder will position themselves at the section of fence to be tested. 2.2 Grab and firmly shake the fence fabric to attempt to set off an alarm. No alarms are received at the workstation. An intrusion alarm is received at the workstation. 2.3 Clear the intrusion alarm at the workstation. The active alarm queue is empty. 3.0 Intrusion Test Fence Climb 3.1 Intruder will position themselves at the section of fence to be climbed. No alarms are received at the workstation. 3.2 Intruder will begin to climb the fence. An intrusion alarm is received at the workstation. 3.3 Clear the intrusion alarm at the workstation. The active alarm queue is empty. 4.0 Nuisance Test 4.1 Intruder will position themselves at the section of No alarms are received at the workstation.
21 fence to be tested. 4.2 Grab and rattle the fence to simulate wind on the fence. No intrusion alarms are received at the workstation.
22 Title: Glass Break Sensor - Acoustic Type Objective: Verify device is installed using acceptable standards and practices, communicates properly with the IDS, and provides proper protection of assets and meets or exceeds the contract performance specification. Applicability: Glass Break Sensors (Acoustic Type) 1. Real-time voice communications between the workstation operator and the field technician is required. 2. The field technician will need a Glass Breakage Tester unit (and potentially a stepladder and other tools) to perform the tests. 3. Perform all tests with the associated zone in the ACCESS state. 4. If multiple sensors are used to protect an alarmed zone, disable all sensors except the unit being tested. Restore all sensors to normal operation following the completion of testing. 5. Line Supervision, Power Fail, and Tamper Tests need to be performed in addition to these procedures. 1.0 Intrusion Test 1.1 Position testing unit on the glass pane furthest away from the sensor but at a distance no greater than the sensors range published by the manufacturer. Activate the testing unit. An intrusion alarm is received at the workstation. If equipped, a visual alarm (light) will be displayed. After completion of test and prior to performing additional tests, verify that the visual alarm is reset. 1.2 Clear the intrusion alarm at the workstation. The active alarm queue is empty. 1.3 Repeat for each of the corners of the covered glass farthest from the center of the coverage zone.
23 Title: Glass Break Sensor - Contact Type Objective: Verify device is installed using acceptable standards and practices, communicates properly with the IDS, and provides proper protection of assets and meets or exceeds the contract performance specification. Applicability: Glass Break Sensors (Contact Type) 1. Real-time voice communications between the workstation operator and the field technician is required. 2. The field technician may need tools and a stepladder to perform the test. 3. Conduct the intrusion test with a lightweight tool such as the plastic handle of a screwdriver. 4. Perform all tests with the associated zone in the ACCESS state. 5. If multiple sensors are used to protect an alarmed zone, disable all sensors except the unit being tested. Restore all sensors to normal operation following the completion of testing. 6. Line Supervision, Power Fail, and Tamper Tests need to be performed in addition to these procedures. 1.0 Intrusion Test 1.1 Lightly rap the glass in the corner farthest from the sensor. An intrusion alarm is received at the workstation. 1.2 Clear the intrusion alarm at the workstation. The active alarm queue is empty.
24 Title: Interior Volumetric Sensor Objective: Verify device is installed using acceptable standards and practices, communicates properly with the IDS, and provides proper protection of assets and meets or exceeds the contract performance specification. Applicability: Passive infrared, microwave, and dual technology sensors 1. Real-time voice communications between the workstation operator and the field technician is required. 2. The field technician may need tools and a stepladder to perform the sensor tamper test. 3. Perform intrusion tests with a human target. All observers are to remain still and clear of the detection zone to avoid triggering the alarm and creating invalid results. 4. Prior to the start of testing, mark five intrusion lanes (or points of intrusion taking into account the sensor coverage area), with each lane probing a different portion of the sensor detection pattern. Test each intrusion lane. 5. Perform the intrusion test with the associated zone in the SECURE state. 6. If multiple sensors are used to protect an alarmed zone, disable all sensors except the unit being tested. Restore all sensors to normal operation following the completion of testing. 7. If equipped, enabling sensor motion test light is useful for conducting these tests. Deactivate after testing is completed. 8. Line Supervision, Power Fail, and Tamper Tests need to be performed in addition to these procedures. 1.0 Intrusion Test 1.1 Stand at the beginning of the intrusion lane and remain motionless for 20 seconds or until test light turns off. 1.2 Take four steps at a normal walking pace along the intrusion lane and stop. No alarms are received at the workstation. An intrusion alarm is received at the workstation. 1.3 Move out of the sensor detection pattern. 1.4 Clear the intrusion alarm at the workstation. The active alarm queue is empty. 1.5 Repeat for all lanes (note # 4).
25 Title: Microwave Sensors Objective: Verify device is installed using acceptable standards and practices, communicates properly with the IDS, and provides proper protection of assets and meets or exceeds the contract performance specification. Applicability: Bi-static microwave and mono-static microwave 1. Real-time voice communications between the workstation operator and the field technician is required. 2. Make penetration attempts using methods and locations that minimize the chance of detection. 3. It is acceptable to use calibrated substitutes for a human intruder. For example, a 12-inch (30 cm) diameter aluminum sphere pulled at grade across the detection zone may be permissible. 4. Instruct all observers to stand away from the coverage zone in order to avoid triggering an alarm and creating invalid results. 5. Perform the walk test at a normal pace. Allow practice runs for the run-and-jump test in order to approximate the location of the zone to better time the jump to clear the zone. Conduct the crawl test at a slow, steadily paced crawl. If applicable at a vehicle gate, perform the intrusion test using a vehicle. Vary test speed in the range of 0.2 to 25 feet/second. 6. Perform intrusion tests approximately every 10 feet or less depending on the zone length. 7. Perform the Intrusion Tests with the associated zone in the SECURE state. 8. Line Supervision, Power Fail, and Tamper Tests need to be performed in addition to these procedures. 9. Perform the tamper test on all transmitters, receivers, and field distribution boxes. 10. If equipped, enabling sensor motion test lights or tones is useful for conducting these tests. Deactivate after testing is completed. 1.0 Intrusion Test Walking, Run-and-Jump, Crawling, Vehicle 1.1 Stand outside of the coverage zone. No alarms are received at the workstation. 1.2 Cross the coverage zone. An intrusion alarm is received at the workstation. 1.3 Stop outside of the coverage zone. 1.4 Clear the intrusion alarm at the workstation. The active alarm queue is empty. 1.5 Repeat for each entry method along the coverage zone.
26 Title: Buried Ported Coax Sensors Objective: Verify device is installed using acceptable standards and practices, communicates properly with the IDS, and provides proper protection of assets and meets or exceeds the contract performance specification. Applicability: Perimeters 1. Real-time voice communications between the workstation operator and the field technician is required. 2. The sensor may be equipped with an integral test indicator. If present, verify that the test indicator is operable and visible during the test. 3. Instruct all observers to stand away from the coverage zone in order to avoid triggering the alarm and creating invalid results. 4. Make penetration attempts using methods and locations that minimize the chance of detection. Areas of note are beginning and ending of cable runs, crossovers, transitions to different ground medium, areas after sharp bends in the cable paths, and locations in close proximity to fencing and other metal objects. 5. Make intrusion attempts across the sensor cable at approximately 10-foot intervals. Adjust this interval at the termination points of the two sensor cable pairs. 6. Vary test speed in the range of 0.2 to 25 feet/second. 7. Allow practice runs for the run-and-jump test to approximate the location of the zone to better time the jump to clear the zone. 8. Perform the intrusion tests with the associated zone in the SECURE state. 9. Line Supervision, Power Fail, and Tamper Tests need to be performed in addition to these procedures. 1.0 Intrusion Test Walking and Run-and-Jump 1.1 Stand outside of the coverage zone. No alarms are received at the workstation. 1.2 Cross the coverage zone. An intrusion alarm is received at the workstation. 1.3 Stop outside of the coverage zone. 1.4 Clear the intrusion alarm at the workstation. The active alarm queue is empty. 1.5 Repeat for each testing method. 2.0 Remote Test 2.1 Verify that there are no active alarms along the sensor path. 2.2 Activate the remote test. Alarm received at the workstation. 2.3 Clear the alarm at the workstation. The active alarm queue is empty.
27 Title: Taut Wire Sensor Objective: Verify device is installed using acceptable standards and practices, communicates properly with the IDS, and provides proper protection of assets and meets or exceeds the contract performance specification. Applicability: Fences, perimeters. 1. Real-time voice communications between the workstation operator and the field technician is required. 2. The field technician may need tools, protective equipment, and a stepladder to perform the sensor tamper test. 3. When conducting the deflection test, do not pull wires beyond a 2 inch deflection. This is to avoid damaging the system. 4. Make penetration attempts using methods and locations that minimize the chance of detection. 5. Conduct tests for each wire at the point farthest from the sensor posts. 6. Conduct the tamper test for field distribution boxes, sensor posts, and sensor post junction boxes (if used). 1.0 Intrusion Test Deflection Test 1.1 Attach a measurement tool (like a yardstick) behind the wire to be tested. 1.2 Slowly pull the wire down and measure the vertical deflection required to trigger an alarm. (See note 3.) No alarms are received at the workstation. An intrusion alarm is received at the workstation. 1.3 Clear the intrusion alarm at the workstation. The active alarm queue is empty. 1.4 Repeat for each wire.
28 Title: Vibration Sensor Objective: Verify system is installed using acceptable standards and practices, communicates properly, and provides proper protection of assets and meets or exceeds the contract performance specification. Applicability: Vibration Sensors. Example: covering vaults and arms rooms. 1. Real-time voice communications between the workstation operator and the field technician is required. 2. The field technician may need tools and a stepladder to perform the sensor tamper test. 3. Take care so as not to damage any surfaces while conducting this test. 4. Test may require multiple impacts to trigger sensor depending on the sensor configuration. 5. Perform the intrusion tests with the associated zone in the SECURE state. 6. If multiple sensors are used to protect an alarmed zone, disable all sensors except the unit being tested. Restore all sensors to normal operation following the completion of testing. 7. Line Supervision, Power Fail, and Tamper Tests need to be performed in addition to these procedures. 1.0 Intrusion Test 1.1 Stand still near the sensor. No alarms are received at the workstation. 1.2 Create a vibration. Example: strike the wall with a rubber mallet at different locations within the manufacturer s rated coverage area. An intrusion alarm is received at the workstation. 1.3 Clear the intrusion alarm at the workstation. The active alarm queue is empty.
29 Title: Line Supervision Test Objective: Verify system is installed using acceptable standards and practices, communicates properly, and provides proper protection of assets and meets or exceeds the contract performance specification. Also verifies the ability of a system to recover after a communications failure. Applicability: Sensors, Transmission lines, Panels (FDBs and ACUs), Workstations, Servers, IDS, ACS. 1. Procedures are designed assuming a system consisting of an Access Control Unit (ACU) (for example a door controller) with associated devices that is connected to a workstation. 2. The field technician may need keys to access components in locked rooms for these tests. 3. A detailed link testing list is essential to ensuring 100% system testing. 4. The purpose of alarm annunciation is to provide a correct and useful location of the alarm. 5. Real-time voice communications between the workstation operator and the field technician is required. 6. Verify that alarms annunciate quickly and meet appropriate standards. 1.0 Communications Failure and Access Control Unit (ACU) Test 1.1 Disconnect the network communication line at the ACU. 1.2 Repeat access, access denied, egress, and alarm (door held or door forced) tests. Network communication failure alarm received at the workstation. Tests results are consistent with the results from the respective tests, but alarms are not received at the workstation. 1.3 Reconnect the communications line. Workstation receives all system transaction logs and alarms from tests performed while communications were disconnected. Workstation shows communications have been restored. 1.4 Clear the alarms at the workstation. The active alarm queue is empty. 2.0 ACU to Credential Verification Device Failure Test 2.1 Disconnect the communication line from the ACU to the credential verification device. Line supervision alarm received at the workstation. 2.2 Repeat Valid Credential test. Device is unresponsive, door lock does not release. 2.3 Reconnect the communication line from the ACU to the credential verification device. Line supervision alarm is still active. 2.4 Clear the alarms at the workstation. The active alarm queue is empty. 2.5 Repeat Valid Credential test. Transaction logged at the workstation. Door lock releases. 3.0 Open Circuit Test (conduct this test for each
30 device) 3.1 Disconnect the device signal lead from the ACU. Line supervision alarm received at the workstation. 3.2 Reconnect the device signal lead from the ACU. The alarm is still active. 3.3 Clear the alarms at the workstation. The active alarm queue is empty. 4.0 Short Circuit Test (conduct this test for each device) 4.1 Place a jumper wire across the terminal blocks for the input and short the device s input wires together. Line supervision alarm received at the workstation. 4.2 Remove the jumper wire. The alarm is still active. 4.3 Clear the alarms at the workstation. The active alarm queue is empty.
31 Title: Power Failure Test Objective: Verify system is installed using acceptable standards and practices, communicates properly, and provides proper protection of assets and meets or exceeds the contract performance specification. Applicability: Backup Power, ACS, IDS 1. Procedures are designed assuming a system consisting of an Access Control Unit (ACU) (for example a door controller) with associated devices that is connected to a workstation. 2. Take appropriate safety precautions because this test involves energized power sources. 3. If backup power is batteries, a multi-meter or voltage meter is required to test voltage. 4. Real-time voice communications between the workstation operator and the field technician is required. 5. Perform these tests with the associated zone in the SECURE state. 1.0 AC Power Loss and Restoration Test 1.1 Disconnect AC power from the ACU. AC power failure alarm is received at the workstation. No intrusion alarms are generated from the power loss. System continues to operate correctly. 1.2 Reconnect AC power to the ACU. Workstation notifies that AC power has been restored. No intrusion alarms are generated from the change in power source. System continues to operate correctly. AC power failure alarm is not cleared until acknowledged at the workstation. 1.3 Clear alarm at workstation. Active alarm queue is empty. 2.0 Backup Power Duration Test 2.1 Allow the system to run under normal conditions on battery power. Note the time of disconnection from AC power. (If backup power is a battery, measure the voltage of the battery immediately after disconnecting AC power). 2.2 Allow the system to run until at least the required duration has passed. (If backup battery is used, measure the voltage of the battery prior to reconnecting the AC power in the next step). System switches to backup power without issues. (If battery backup is used, document the measured voltage.) System operated correctly for the entire required duration. (If battery backup is used, document the measured voltage.) 2.3 Reconnect AC power. System switches to AC power without issues. 3.0 Battery Recharge Test (if applicable) 3.1 After Backup Power Duration Test has been performed, reconnect AC power and note the time. 3.2 Allow the system to run for the required recharge duration. System switches to AC power without issues. System operated correctly for the entire required duration. 3.3 Measure the battery s voltage. Voltage on the battery has returned to full value as measured in the Backup Power Duration Test.
Total Connect Box. User manual
 Total Connect Box User manual 1 Congratulations on your purchase of the Honeywell Total Connect Box security system. To make the best out of your system we advise you to read this manual carefully. This
Total Connect Box User manual 1 Congratulations on your purchase of the Honeywell Total Connect Box security system. To make the best out of your system we advise you to read this manual carefully. This
The most user friendly Security Alarm System L S Section 1 Overview of System Section 2 Planning your Installation
 The most user friendly Contents Section 1 Overview of System 1.1 Kit Contents 1.2 Tools Required 1.3 System Features Security Alarm System L S 4 0 0 Section 2 Planning your Installation 2.1 Location of
The most user friendly Contents Section 1 Overview of System 1.1 Kit Contents 1.2 Tools Required 1.3 System Features Security Alarm System L S 4 0 0 Section 2 Planning your Installation 2.1 Location of
Security Considerations for Secure Workplaces
 Security Considerations for Secure Workplaces Mitchell Factor HMA Consulting, Inc. USA Canada UK UAE Overview Security Risk Assessment The Process Security Design Process Technology Updates & Design Considerations
Security Considerations for Secure Workplaces Mitchell Factor HMA Consulting, Inc. USA Canada UK UAE Overview Security Risk Assessment The Process Security Design Process Technology Updates & Design Considerations
Paradox Integration Module Settings Guide
 Paradox Integration Module Settings Guide List of Terms used in Paradox Integration Module Settings Guide............. 3 Introduction into Paradox Integration Module Settings Guide............... 4 Configuration
Paradox Integration Module Settings Guide List of Terms used in Paradox Integration Module Settings Guide............. 3 Introduction into Paradox Integration Module Settings Guide............... 4 Configuration
A Beginners Guide to Inner Range Systems
 A Beginners Guide to Inner Range Systems Inner Range manufactures a range of integrated Intrusion Detection and Access Control systems to cover sites of any size, while sharing a common configuration layout.
A Beginners Guide to Inner Range Systems Inner Range manufactures a range of integrated Intrusion Detection and Access Control systems to cover sites of any size, while sharing a common configuration layout.
1126 Series Ceiling Mount PIR Motion Detector
 Installation Sheet 1126 Series Ceiling Mount PIR Motion Detector Description The 1126 Series PIR (Passive Infrared) Motion Detectors are a compact wireless PIR. The 1126 Series offer 360, Wide Angle, or
Installation Sheet 1126 Series Ceiling Mount PIR Motion Detector Description The 1126 Series PIR (Passive Infrared) Motion Detectors are a compact wireless PIR. The 1126 Series offer 360, Wide Angle, or
IDS816 User Manual H Issued January 2009
 1 Contents Glossary-------------------------------------------------------------------------------------------------------------------6 1. Introduction to the IDS 816---------------------------------------------------------------------------7
1 Contents Glossary-------------------------------------------------------------------------------------------------------------------6 1. Introduction to the IDS 816---------------------------------------------------------------------------7
The IPPS was developed on IBM-PC platform under QNX real time operating system (RTOS) and uses QNX-Windows GUI.
 IAEA-SM-367/4/02/P INTEGRATED PHYSICAL PROTECTION SYSTEM Ranajit Kumar Control Instrumentation Division, Bhabha Atomic Research Center, Trombay, Mumbai 400085, India Abstract An Integrated Physical Protection
IAEA-SM-367/4/02/P INTEGRATED PHYSICAL PROTECTION SYSTEM Ranajit Kumar Control Instrumentation Division, Bhabha Atomic Research Center, Trombay, Mumbai 400085, India Abstract An Integrated Physical Protection
Contents. Glossary
 Contents Glossary ------------------------------------------------------------------------------------------------------ 6 1. Introduction to the IDS 1632 -------------------------------------------------------------
Contents Glossary ------------------------------------------------------------------------------------------------------ 6 1. Introduction to the IDS 1632 -------------------------------------------------------------
Wireless Keypads LKP(E)S8M Series
 Wireless Keypads LKP(E)S8M Series User manual Contents Congratulations on your purchase of this Honeywell wireless keypad. To make the best out of your equipment we advise you to read this manual carefully.
Wireless Keypads LKP(E)S8M Series User manual Contents Congratulations on your purchase of this Honeywell wireless keypad. To make the best out of your equipment we advise you to read this manual carefully.
FlexZone SIX STEPS TO AFFORDABLE PERIMETER PROTECTION EASY TO INSTALL LOW TOTAL COST OF OWNERSHIP HASSLE-FREE OPERATION & MAINTENANCE HOW-TO GUIDE
 FlexZone HOW-TO GUIDE SIX STEPS TO AFFORDABLE PERIMETER PROTECTION EASY TO INSTALL LOW TOTAL COST OF OWNERSHIP HASSLE-FREE OPERATION & MAINTENANCE Detect intruders BEFORE they get in By itself, your expensive
FlexZone HOW-TO GUIDE SIX STEPS TO AFFORDABLE PERIMETER PROTECTION EASY TO INSTALL LOW TOTAL COST OF OWNERSHIP HASSLE-FREE OPERATION & MAINTENANCE Detect intruders BEFORE they get in By itself, your expensive
1125 PIR Motion Detector
 Tamper Survey LED INSTALLATION SHEET 1125 PIR Motion Detector Description The 1125 PIR (Passive Infrared) Motion Detector is a wireless, low current sensor for use with the 1100D Wireless Receiver. Using
Tamper Survey LED INSTALLATION SHEET 1125 PIR Motion Detector Description The 1125 PIR (Passive Infrared) Motion Detector is a wireless, low current sensor for use with the 1100D Wireless Receiver. Using
abode Web app Functionality
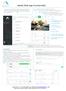 abode Web app Functionality System mode display controls the state of the alarm system. The user can change the mode of the system by simply clicking on the desired mode. When arming the system with the
abode Web app Functionality System mode display controls the state of the alarm system. The user can change the mode of the system by simply clicking on the desired mode. When arming the system with the
The. Long Beach, California August 14-17, Solutions Network. Physical Security PERIMETER SECURITY TECHNOLOGIES. Leon Snyman GVI Security, Inc.
 Long Beach, California August 14-17, 2005 The Solutions Network Physical Security PERIMETER SECURITY TECHNOLOGIES Leon Snyman GVI Security, Inc. Why Secure the Perimeter? Your Perimeter is Your FIRST line
Long Beach, California August 14-17, 2005 The Solutions Network Physical Security PERIMETER SECURITY TECHNOLOGIES Leon Snyman GVI Security, Inc. Why Secure the Perimeter? Your Perimeter is Your FIRST line
4040 FM 535 F :
 OVERVIEW OPTICAL TURNSTILE SYSTEM HALF HEIGHT BARRIER TURNSTILES MODEL OTS-HHB-6 The OTS-HHB monitors through-beam infrared sensors, access control contacts, and barrier posion sensors to control the moon
OVERVIEW OPTICAL TURNSTILE SYSTEM HALF HEIGHT BARRIER TURNSTILES MODEL OTS-HHB-6 The OTS-HHB monitors through-beam infrared sensors, access control contacts, and barrier posion sensors to control the moon
Contents. Glossary Introduction to the IDS Notes Understanding the Keypad Indicators Operation of the Keypad...
 2 Contents Glossary...7 1. Introduction to the IDS805...8 1.1 Notes...8 2. Understanding the Keypad Indicators...8 3. Operation of the Keypad...9 4. System Information...10 4.1 Programmed Functions...10
2 Contents Glossary...7 1. Introduction to the IDS805...8 1.1 Notes...8 2. Understanding the Keypad Indicators...8 3. Operation of the Keypad...9 4. System Information...10 4.1 Programmed Functions...10
Contact ID as of 2/2/2015
 Contact ID as of 2/2/2015 100 Medical Zone A non-specific medical exists 101 Personal Emergency Zone Emergency Assistance request 102 Fail to report in Zone A user has failed to activate a monitoring device
Contact ID as of 2/2/2015 100 Medical Zone A non-specific medical exists 101 Personal Emergency Zone Emergency Assistance request 102 Fail to report in Zone A user has failed to activate a monitoring device
DS9370-BEL. Installation Instructions TriTech Ceiling Mount PIR/Microwave Intrusion Detector
 DS970-BEL EN Installation Instructions TriTech Ceiling Mount PIR/Microwave Intrusion Detector DS970-BEL Installation Instructions.0 Installation Considerations.0 Installation Considerations Not suitable
DS970-BEL EN Installation Instructions TriTech Ceiling Mount PIR/Microwave Intrusion Detector DS970-BEL Installation Instructions.0 Installation Considerations.0 Installation Considerations Not suitable
Solution Ultima 862 Operators Manual ISSUE 1.10
 Solution Ultima 862 Operators Manual ISSUE 1.10 Solution Ultima 862 Operators Manual Copyright 2001 by, SYDNEY, AUSTRALIA Document Part Number MA486O DOCUMENT ISSUE 1.10 Printed 24 April 2001 This documentation
Solution Ultima 862 Operators Manual ISSUE 1.10 Solution Ultima 862 Operators Manual Copyright 2001 by, SYDNEY, AUSTRALIA Document Part Number MA486O DOCUMENT ISSUE 1.10 Printed 24 April 2001 This documentation
Integration Test Plan
 Integration Test Plan Terminus Security Prepared by: Kai Chan Stephen Krenzel John O Meara Version: 1.0 1 Contents 1 Introduction 3 1.1 Purpose.................................. 3 1.2 Scope...................................
Integration Test Plan Terminus Security Prepared by: Kai Chan Stephen Krenzel John O Meara Version: 1.0 1 Contents 1 Introduction 3 1.1 Purpose.................................. 3 1.2 Scope...................................
8 plus and16 plus. User s Guide * # ent. esc GALAXY 16+ V2.XX TUE 30 JUN. IU ZST 962 Issue 2. A u B u
 8 plus and16 plus User s Guide GALAXY 16+ V2.XX 06.22 TUE 30 JUN 1 2 3 4 5 6 7 8 9 0 * # A u B u ent esc IU1-0018 ZST 962 Issue 2 Contents INTRODUCTION... 1 Glossary of Terms... 3 KEYPAD INFORMATION...
8 plus and16 plus User s Guide GALAXY 16+ V2.XX 06.22 TUE 30 JUN 1 2 3 4 5 6 7 8 9 0 * # A u B u ent esc IU1-0018 ZST 962 Issue 2 Contents INTRODUCTION... 1 Glossary of Terms... 3 KEYPAD INFORMATION...
Wireless Keypad GKP-S8M
 Wireless Keypad GKP-S8M User manual Contents Congratulations on your purchase of this Honeywell wireless keypad. To make the best out of your equipment we advise you to read this manual carefully. This
Wireless Keypad GKP-S8M User manual Contents Congratulations on your purchase of this Honeywell wireless keypad. To make the best out of your equipment we advise you to read this manual carefully. This
To activate the Net2 alarm integration software the correct check box must be ticked on the features tab in the Net2 server configuration utility.
 n A Overview AN1035 - Integrating with an intruder alarm system 22/09/2006 When using alarm integration, will monitor whether the intruder alarm is armed or disarmed. If the alarm is armed, will only allow
n A Overview AN1035 - Integrating with an intruder alarm system 22/09/2006 When using alarm integration, will monitor whether the intruder alarm is armed or disarmed. If the alarm is armed, will only allow
OPTICAL TURNSTILE SYSTEM
 OPTICAL TURNSTILE SYSTEM Installation Instructions OTS-WNG UNPACK TURNSTILES. Remove the bolts at the ends of the turnstiles to separate from the skids and place turnstiles on the floor. With a box knife
OPTICAL TURNSTILE SYSTEM Installation Instructions OTS-WNG UNPACK TURNSTILES. Remove the bolts at the ends of the turnstiles to separate from the skids and place turnstiles on the floor. With a box knife
IDS S E C U R I T Y IDS816. User Manual. MANUAL NO A ISSUED November 2004 VERSION 1.00
 INHEP DIGITAL IDS S E C U R I T Y IDS816 User Manual MANUAL NO. 700-283-02A ISSUED November 2004 VERSION 1.00 Contents 1. Introduction to the IDS816... 4 2. Understanding the Keypad Indicators... 4 3.
INHEP DIGITAL IDS S E C U R I T Y IDS816 User Manual MANUAL NO. 700-283-02A ISSUED November 2004 VERSION 1.00 Contents 1. Introduction to the IDS816... 4 2. Understanding the Keypad Indicators... 4 3.
RCR-REX Request-to-Exit Dual Technology Motion Sensor Installation Guide
 RCR-REX Request-to-Exit Dual Technology Motion Sensor Installation Guide Introduction This is the Interlogix RCR-REX Request-to-Exit Dual Technology Motion Sensor Installation Instructions for models RCR-REX-W,
RCR-REX Request-to-Exit Dual Technology Motion Sensor Installation Guide Introduction This is the Interlogix RCR-REX Request-to-Exit Dual Technology Motion Sensor Installation Instructions for models RCR-REX-W,
Security System. User Guide for the LED Command Center
 Security System User Guide for the LED Command Center National Security Systems Inc (800)457-1999 MY SECURITY COMPANY IS: CALL BEFORE TEST: THIS SECURITY SYSTEM IS CONNECTED TO TELEPHONE NUMBER: THE SECURITY
Security System User Guide for the LED Command Center National Security Systems Inc (800)457-1999 MY SECURITY COMPANY IS: CALL BEFORE TEST: THIS SECURITY SYSTEM IS CONNECTED TO TELEPHONE NUMBER: THE SECURITY
SecurityScan Inspection Certificate
 SecurityScan Inspection Certificate For Sample Inspection Report 123 Main Street Kalamazoo, MI 49007 Tested to applicable Standards This Inspection was performed in accordance with applicable Standards.
SecurityScan Inspection Certificate For Sample Inspection Report 123 Main Street Kalamazoo, MI 49007 Tested to applicable Standards This Inspection was performed in accordance with applicable Standards.
System. For a better understanding of this product, please read this user manual thoroughly before using it.
 GSM Alarm System User s Manual For a better understanding of this product, please read this user manual thoroughly before using it. Chapter 1. Features Chapter 2. Control Panel Introduction Chapter 3.
GSM Alarm System User s Manual For a better understanding of this product, please read this user manual thoroughly before using it. Chapter 1. Features Chapter 2. Control Panel Introduction Chapter 3.
Microwave/PIR Intrusion Detector with POPIT Interface ZX970
 Microwave/PIR Intrusion Detector with POPIT Interface ZX970 Installation Instructions 1.0 Specifications Input Power: 9 to 15 VDC, 6 ma nominal (35 ma with LED on) Zonex Current Draw: 500 ma Standby Power:
Microwave/PIR Intrusion Detector with POPIT Interface ZX970 Installation Instructions 1.0 Specifications Input Power: 9 to 15 VDC, 6 ma nominal (35 ma with LED on) Zonex Current Draw: 500 ma Standby Power:
The system should also be capable of recording events automatically on any compatible DVR and should be able to retrieve recordings based on events.
 0BThe System The Security Management System should be capable of Controlling and Monitoring Access through the doors, Monitor and control Inputs and Outputs, include an Integrated Video Badging, Integrate
0BThe System The Security Management System should be capable of Controlling and Monitoring Access through the doors, Monitor and control Inputs and Outputs, include an Integrated Video Badging, Integrate
System Design and Overview Document
 System Design and Overview Document Power Calculations: This is one the most important tasks when designing your system. You must add up worst case current draw of your system. The power supply contained
System Design and Overview Document Power Calculations: This is one the most important tasks when designing your system. You must add up worst case current draw of your system. The power supply contained
SIA/IAPSC CAD Security Symbols
 APPENDIX A TABLE OF SYMBOLS (This Appendix shall be considered a fully binding part of this standard.) 1. ANNOTATION 1.01 REF Device Reference A: Drawing Sheet B: Detail C: Device / Zone Number 2. ACCESS
APPENDIX A TABLE OF SYMBOLS (This Appendix shall be considered a fully binding part of this standard.) 1. ANNOTATION 1.01 REF Device Reference A: Drawing Sheet B: Detail C: Device / Zone Number 2. ACCESS
OpenDevice Events Guide
 OpenDevice Events Guide 2016 United Lenel is a part of UTC Climate, Controls & Security, a unit of United July 19, 2016 1 Table of Contents Open Device Events... 3 Granted Access Events... 8 Denied Events...
OpenDevice Events Guide 2016 United Lenel is a part of UTC Climate, Controls & Security, a unit of United July 19, 2016 1 Table of Contents Open Device Events... 3 Granted Access Events... 8 Denied Events...
Lonix Access Control Operation & Maintenance Manual
 1 (7) Lonix Access Control Operation & Maintenance Manual Lonix Ltd Teollisuuskatu 33 FI-00510 Helsinki Finland www.lonix.com 2 (7) Contents 1 Introduction...3 1.1 Health and Safety...3 1.2 Health and
1 (7) Lonix Access Control Operation & Maintenance Manual Lonix Ltd Teollisuuskatu 33 FI-00510 Helsinki Finland www.lonix.com 2 (7) Contents 1 Introduction...3 1.1 Health and Safety...3 1.2 Health and
Section PERIMETER SECURITY SYSTEMS
 Section 28 16 43 PERIMETER SECURITY SYSTEMS PART 1 GENERAL 1.1 SUMMARY A. Provide and install a perimeter security system as herein specified for the purpose of detecting entry into a designated security
Section 28 16 43 PERIMETER SECURITY SYSTEMS PART 1 GENERAL 1.1 SUMMARY A. Provide and install a perimeter security system as herein specified for the purpose of detecting entry into a designated security
IDS800 USER MANUAL. Summary of Operation. + [ ] 2 IDS800 USER MANUAL NO K ISSUED APR 2003 VER 1.44
![IDS800 USER MANUAL. Summary of Operation. + [ ] 2 IDS800 USER MANUAL NO K ISSUED APR 2003 VER 1.44 IDS800 USER MANUAL. Summary of Operation. + [ ] 2 IDS800 USER MANUAL NO K ISSUED APR 2003 VER 1.44](/thumbs/89/98095999.jpg) Summary of Operation A rm/ disarm [#] + [USER CODE] Quick Quick Quick Away Arm Stay Arm Stay Arm & Go H old down [ 1] for 1 second H old down [ 5] for 1 second H old down [ 6] for 1 second Panic Fire Medical
Summary of Operation A rm/ disarm [#] + [USER CODE] Quick Quick Quick Away Arm Stay Arm Stay Arm & Go H old down [ 1] for 1 second H old down [ 5] for 1 second H old down [ 6] for 1 second Panic Fire Medical
Version 1.03 January-2002 USER S MANUAL
 Version 1.03 January-2002 1 USER S MANUAL 2 Version 1.03 January-2002 System Details CUSTOMER:...... PHONE:... FAX:... INSTALLED BY:...... PHONE:... FAX:... MAINTENANCE & SERVICE:...... PHONE:... FAX:...
Version 1.03 January-2002 1 USER S MANUAL 2 Version 1.03 January-2002 System Details CUSTOMER:...... PHONE:... FAX:... INSTALLED BY:...... PHONE:... FAX:... MAINTENANCE & SERVICE:...... PHONE:... FAX:...
CC880/LP880, SC8016. Operators Guide Solution-16, Solution-16 Safecom
 CC880/LP880, SC8016 EN Operators Guide Solution-16, Solution-16 Safecom CC880/LP880, SC8016 Operators Guide EN 2 Copyright Notice Unless otherwise indicated, this publication is the copyright of Bosch
CC880/LP880, SC8016 EN Operators Guide Solution-16, Solution-16 Safecom CC880/LP880, SC8016 Operators Guide EN 2 Copyright Notice Unless otherwise indicated, this publication is the copyright of Bosch
Touchpad Exit Controller Administration Guide
 Touchpad Exit Controller Administration Guide 2018 RF Technologies, Inc. All specifications subject to change without notice. All Rights Reserved. No Part of this work may be reproduced or copied in any
Touchpad Exit Controller Administration Guide 2018 RF Technologies, Inc. All specifications subject to change without notice. All Rights Reserved. No Part of this work may be reproduced or copied in any
Bi-Directional Barrier Arm Turnstile
 ES831 *Custom model shown in stone and bronze Bi-Directional Barrier Arm Turnstile Model ES831 Optical Turnstiles > ES831 Series > Optical Turnstiles w/ Barrier Arms > Design Overview The ES831 bi-directional
ES831 *Custom model shown in stone and bronze Bi-Directional Barrier Arm Turnstile Model ES831 Optical Turnstiles > ES831 Series > Optical Turnstiles w/ Barrier Arms > Design Overview The ES831 bi-directional
RDM LOCK G Series Electromagnetic Lock. Listings. Standard Features. Ordering Information:
 RDM LOCK G-1 1400 Series Electromagnetic Lock The patented 1400 Series Electromagnetic Lock is universal for all types of applications, including outdoor use. The innovative design will reduce installation
RDM LOCK G-1 1400 Series Electromagnetic Lock The patented 1400 Series Electromagnetic Lock is universal for all types of applications, including outdoor use. The innovative design will reduce installation
IDS S E C U R I T Y IDS816. User Manual MANUAL NO B ISSUED DEC 2004 VERSION 2.00
 INHEP DIGITAL IDS S E C U R I T Y IDS816 User Manual MANUAL NO. 700-283-01 B ISSUED DEC 2004 VERSION 2.00 Contents 1. Introduction to the IDS816... 4 2. Understanding the Keypad Indicators... 4 3. Programmable
INHEP DIGITAL IDS S E C U R I T Y IDS816 User Manual MANUAL NO. 700-283-01 B ISSUED DEC 2004 VERSION 2.00 Contents 1. Introduction to the IDS816... 4 2. Understanding the Keypad Indicators... 4 3. Programmable
KwêBeams Effective wire free outdoor early warning system
 1 KwêBeams Effective wire free outdoor early warning system Features: - Easy to install & use - Operates on 868Mhz frequency (less congested to avoid signal jamming) - All sensors with built in sirens,
1 KwêBeams Effective wire free outdoor early warning system Features: - Easy to install & use - Operates on 868Mhz frequency (less congested to avoid signal jamming) - All sensors with built in sirens,
Why Should You Invest In An Access Management System?
 Why Should You Invest In An Access Management System? The key word in this question is Invest. Buying and installing an access system by itself is an investment that will increase security, enhance overall
Why Should You Invest In An Access Management System? The key word in this question is Invest. Buying and installing an access system by itself is an investment that will increase security, enhance overall
HA-263K HA-263D. OWNER'S MANUAL Installation And Operation 8-ZONE ALARM CONTROL PANEL FOR HOME AND OFFICE PROTECTIONS OPEN THE CABINET FOR SERVICE
 D (OPERATION) INITIATE A DYNAMIC BATTERY TEST The system tests the back-up battery once every 24 hours. The owner can initiate a dynamic battery test at any time with the following codes while the system
D (OPERATION) INITIATE A DYNAMIC BATTERY TEST The system tests the back-up battery once every 24 hours. The owner can initiate a dynamic battery test at any time with the following codes while the system
AXI LED USER MANUAL (REV. 1.0)
 Security & Home Automation System AXI LED USER MANUAL (REV. 1.0) CONTENTS PREFACE FEATURES LED KEYPAD OUTLOOK 1.0 LIGHT INDICATION 1 2 4 6 CHAPTER 1: ALARM SYSTEM CONTROL 1.0 USING LED KEYPAD 1.0.1 ARMING
Security & Home Automation System AXI LED USER MANUAL (REV. 1.0) CONTENTS PREFACE FEATURES LED KEYPAD OUTLOOK 1.0 LIGHT INDICATION 1 2 4 6 CHAPTER 1: ALARM SYSTEM CONTROL 1.0 USING LED KEYPAD 1.0.1 ARMING
Solution Ultima Series Operators Manual ISSUE 1.00
 Solution Ultima Series Operators Manual ISSUE 1.00 Solution Ultima Series Operators Manual Copyright 1998 by, SYDNEY, AUSTRALIA Document Part Number MA488O DOCUMENT ISSUE 1.00 Printed 16 February 1999
Solution Ultima Series Operators Manual ISSUE 1.00 Solution Ultima Series Operators Manual Copyright 1998 by, SYDNEY, AUSTRALIA Document Part Number MA488O DOCUMENT ISSUE 1.00 Printed 16 February 1999
Section 1: General Description. Section 2: Features. Section 3: Operation. CM-RQE70 PIR REQUEST TO EXIT DETECTOR Installation Instructions.
 CM-RQE70 PIR REQUEST TO EXIT DETECTOR Installation Instructions 1 PACKAGE CONTENTS Wiring Harness 6 Wire Nuts #6 x 3/4 Screws s BP7175 3/16 Wall Plugs Section 1: General Description Camden CM-RQE-70 Request-to-Exit
CM-RQE70 PIR REQUEST TO EXIT DETECTOR Installation Instructions 1 PACKAGE CONTENTS Wiring Harness 6 Wire Nuts #6 x 3/4 Screws s BP7175 3/16 Wall Plugs Section 1: General Description Camden CM-RQE-70 Request-to-Exit
Destiny Destiny Owners Manual
 Destiny 4100 Destiny 4100 Owners Manual TABLE OF CONTENTS INTRODUCTION Control Panel...3 Detection Devices...3 Telephone Keypads...3 GLOSSARY... 4-5 LOCAL PHONE ACCESS Using Your Telephones As Keypads...6
Destiny 4100 Destiny 4100 Owners Manual TABLE OF CONTENTS INTRODUCTION Control Panel...3 Detection Devices...3 Telephone Keypads...3 GLOSSARY... 4-5 LOCAL PHONE ACCESS Using Your Telephones As Keypads...6
TW-8000 TAUT WIRE FENCE
 TW-8000 TAUT WIRE FENCE www. rbtec. com Email: info@rbtecom GENERAL TW-8000 Product information INTRUDALERT is a powerful electronic system specifically designed for total perimeter protection of critical
TW-8000 TAUT WIRE FENCE www. rbtec. com Email: info@rbtecom GENERAL TW-8000 Product information INTRUDALERT is a powerful electronic system specifically designed for total perimeter protection of critical
Installation Instructions
 Request-to-Exit Dual Technology Motion Sensor 1048889B November 2005 Copyright 2005, GE Security Inc. Introduction This is the GE Request-to-Exit Dual Technology Motion Sensor for models -W, -B, and -G.
Request-to-Exit Dual Technology Motion Sensor 1048889B November 2005 Copyright 2005, GE Security Inc. Introduction This is the GE Request-to-Exit Dual Technology Motion Sensor for models -W, -B, and -G.
CM-RQE70 PIR REQUEST TO EXIT DETECTOR
 Door Activation Devices CM-RQE70 PIR REQUEST TO EXIT DETECTOR THIS PACKAGE INCLUDES (1) Wiring Harness (2) #6 x 3/4" Screws (2) 3/16" Wall Plugs (6) Wire Nuts (2) 's BP7175 1. GENERAL DESCRIPTION Camden
Door Activation Devices CM-RQE70 PIR REQUEST TO EXIT DETECTOR THIS PACKAGE INCLUDES (1) Wiring Harness (2) #6 x 3/4" Screws (2) 3/16" Wall Plugs (6) Wire Nuts (2) 's BP7175 1. GENERAL DESCRIPTION Camden
Wireless Alarm system s manual
 MOUNTVIEW TECH AUSTRALIA PTY LTD Wireless Alarm system s manual ADS ECO GSM320 Series ADS Security 1/11/2011 1. Before You Begin For your safety and the safety of others, and to ensure that you get the
MOUNTVIEW TECH AUSTRALIA PTY LTD Wireless Alarm system s manual ADS ECO GSM320 Series ADS Security 1/11/2011 1. Before You Begin For your safety and the safety of others, and to ensure that you get the
Electric and Electronic Security Devices
 SECTION 6 Electric and Electronic Security Devices 6.1 Introduction The previous sections of this document identified applications for which utilities may want to install electric and electronic security
SECTION 6 Electric and Electronic Security Devices 6.1 Introduction The previous sections of this document identified applications for which utilities may want to install electric and electronic security
SECTION INTRUSION DETECTION
 (NOTE TO DESIGNER: These Specifications are basic minimum criteria to be met in preparing the final specifications for this section, which is the responsibility of the Designer.) SECTION 28 16 00 INTRUSION
(NOTE TO DESIGNER: These Specifications are basic minimum criteria to be met in preparing the final specifications for this section, which is the responsibility of the Designer.) SECTION 28 16 00 INTRUSION
DIVISION 28 ELECTRONIC SAFETY AND SECURITY
 281300 - ACCESS CONTROL A. General DIVISION 28 ELECTRONIC SAFETY AND SECURITY At the beginning of the project, schedule a meeting with the Facilities Access/Maintenance Coordinator with questions and concerns.
281300 - ACCESS CONTROL A. General DIVISION 28 ELECTRONIC SAFETY AND SECURITY At the beginning of the project, schedule a meeting with the Facilities Access/Maintenance Coordinator with questions and concerns.
X64 Wireless Training
 X64 Wireless Training IDS Contents 1 Contents Features 3 Wireless Hardware 4 IDS & Duevi integration PCB 5 LED operation 5 Wireless Device Hardware setup 6 Location 260 7 LED Keypad Instructions 7 Adding
X64 Wireless Training IDS Contents 1 Contents Features 3 Wireless Hardware 4 IDS & Duevi integration PCB 5 LED operation 5 Wireless Device Hardware setup 6 Location 260 7 LED Keypad Instructions 7 Adding
RVRC Training Manual Fast Trace Installer Menu
 RVRC Training Manual Fast Trace Installer Menu Advanced Independent Monitoring Introduction The following guide is explain how to set up a Fast Trace or Fast TX and common areas to look out for and check
RVRC Training Manual Fast Trace Installer Menu Advanced Independent Monitoring Introduction The following guide is explain how to set up a Fast Trace or Fast TX and common areas to look out for and check
DS160/161 Request To Exit PIR sensors Installation Instructions
 DS160/161 Request To Exit PIR sensors Installation Instructions 1.0 Description The DS160/161 is a passive-infrared (PIR) detector designed for request to exit (REX) interior applications. It is UL Listed
DS160/161 Request To Exit PIR sensors Installation Instructions 1.0 Description The DS160/161 is a passive-infrared (PIR) detector designed for request to exit (REX) interior applications. It is UL Listed
User s Guide. SUB-MA7240O-0001.OG.Solution doc. Created: 6/05/03. Last Updated: 23/09/03. MA7240AO-0001 Version 1.0
 User s Guide SUB-MA7240O-0001.OG.Solution40-111.doc Created: 6/05/03 Last Updated: 23/09/03 MA7240AO-0001 Version 1.0 2 Table Of Contents User List...6 Quick Reference..7 Features...7 Keypad User's Guide...8
User s Guide SUB-MA7240O-0001.OG.Solution40-111.doc Created: 6/05/03 Last Updated: 23/09/03 MA7240AO-0001 Version 1.0 2 Table Of Contents User List...6 Quick Reference..7 Features...7 Keypad User's Guide...8
GARCIA GALUSKA DESOUSA Consulting Engineers
 L#57297 /Page 1/July 21, 2017 ELECTRICAL SYSTEMS NARRATIVE REPORT The following is the Electrical Systems narrative, which defines the scope of work and capacities of the Power and Lighting systems, as
L#57297 /Page 1/July 21, 2017 ELECTRICAL SYSTEMS NARRATIVE REPORT The following is the Electrical Systems narrative, which defines the scope of work and capacities of the Power and Lighting systems, as
ARCHITECTURAL SPECIFICATIONS
 1 G4.1 Entrance System Page 1 of 6, August 2017 DIVISION 10 - SPECIALTIES SECTION 10450 PEDESTRIAN CONTROL DEVICES Specifier Note: Coordinate and edit articles and paragraphs below to suit project requirements.
1 G4.1 Entrance System Page 1 of 6, August 2017 DIVISION 10 - SPECIALTIES SECTION 10450 PEDESTRIAN CONTROL DEVICES Specifier Note: Coordinate and edit articles and paragraphs below to suit project requirements.
Access Professional Edition. The flexible access control system that grows with your business.
 Access Professional Edition The flexible access control system that grows with your business www.boschsecurity.com Access Professional Edition: the ideal solution for easy and intuitive access management
Access Professional Edition The flexible access control system that grows with your business www.boschsecurity.com Access Professional Edition: the ideal solution for easy and intuitive access management
SILENCING AN ALARM When the alarm bell or siren is sounding, enter your user code or present your SecuraProx fob to your keypad.
 SYSTEM USER GUIDE SILENCING AN ALARM When the alarm bell or siren is sounding, enter your user code or present your SecuraProx fob to your keypad. IS THIS A FALSE ALARM? YES NO displays. REAL ALARM If
SYSTEM USER GUIDE SILENCING AN ALARM When the alarm bell or siren is sounding, enter your user code or present your SecuraProx fob to your keypad. IS THIS A FALSE ALARM? YES NO displays. REAL ALARM If
LS800S Intruder Alarm System. Engineering Manual
 LS800S Intruder Alarm System Engineering Manual Table of Contents Section 1 Overview of System 1.1 Kit Contents 1.2 Tools Required 1.3 System Features Section 2 Planning your installation 2.1 Location
LS800S Intruder Alarm System Engineering Manual Table of Contents Section 1 Overview of System 1.1 Kit Contents 1.2 Tools Required 1.3 System Features Section 2 Planning your installation 2.1 Location
G SERIES: Security INTEGRATION as you want it. Greater expansion, communication, video integration, system resilience, and automation.
 G SERIES: Security INTEGRATION as you want it Greater expansion, communication, video integration, system resilience, and automation. G Series Integrated Security Solution Fire Intrusion Access Greater
G SERIES: Security INTEGRATION as you want it Greater expansion, communication, video integration, system resilience, and automation. G Series Integrated Security Solution Fire Intrusion Access Greater
Smart Security, Always Connected
 Smart Security, Always Connected Products Presentation 2018 www.maxkin.com Achieved FINALIST Status at IFSEC s Security & Fire Excellence Awards 2014,2016 Innovative Technology WiFi/GSM Dual-Network FHSS
Smart Security, Always Connected Products Presentation 2018 www.maxkin.com Achieved FINALIST Status at IFSEC s Security & Fire Excellence Awards 2014,2016 Innovative Technology WiFi/GSM Dual-Network FHSS
GV2 Series Control Panels
 GV2 Series Control Panels EN Owner's Manual Supplement System Requirements Minimum system requirements for Classification in accordance with ANSI/SIA CP-01-2000: UL Listed and Classified control unit Model
GV2 Series Control Panels EN Owner's Manual Supplement System Requirements Minimum system requirements for Classification in accordance with ANSI/SIA CP-01-2000: UL Listed and Classified control unit Model
Product Specifications
 Southwest Microwave, Inc. 9055 S. McKemy Street Tempe, Arizona 85284 USA (480) 783-0201 Fax (480) 783-0401 Product Specifications Procurement Specifications INTREPID MicroPoint Cable System Perimeter Detection
Southwest Microwave, Inc. 9055 S. McKemy Street Tempe, Arizona 85284 USA (480) 783-0201 Fax (480) 783-0401 Product Specifications Procurement Specifications INTREPID MicroPoint Cable System Perimeter Detection
 Solution-6 Operators Manual Page 1 Preface Congratulations on selecting the Solution-6 security control system for your installation. So that you can obtain the most from your unit, we suggest that you
Solution-6 Operators Manual Page 1 Preface Congratulations on selecting the Solution-6 security control system for your installation. So that you can obtain the most from your unit, we suggest that you
Touchpad Exit Controller User Guide
 Touchpad Exit Controller User Guide 2018 RF Technologies, Inc. All specifications subject to change without notice. All Rights Reserved. No Part of this work may be reproduced or copied in any form or
Touchpad Exit Controller User Guide 2018 RF Technologies, Inc. All specifications subject to change without notice. All Rights Reserved. No Part of this work may be reproduced or copied in any form or
IDS S E C U R I T Y IDS816. User Manual MANUAL NO C ISSUED APRIL 2005 VERSION 2.00
 INHEP DIGITAL IDS S E C U R I T Y IDS816 User Manual MANUAL NO. 700-283-01C ISSUED APRIL 2005 VERSION 2.00 Contents 1. Introduction to the IDS816... 4 2. Understanding the Keypad Indicators... 4 3. Programmable
INHEP DIGITAL IDS S E C U R I T Y IDS816 User Manual MANUAL NO. 700-283-01C ISSUED APRIL 2005 VERSION 2.00 Contents 1. Introduction to the IDS816... 4 2. Understanding the Keypad Indicators... 4 3. Programmable
GSM Alarm System. User s Manual. Profile. MOBILE CALL GSM Alarm System
 MOBILE CALL GSM Alarm System GSM Alarm System System disarmed 11/26/2013 User s Manual Profile For a better understanding of this product, please read this user manual thoroughly before using it. CONTENTS
MOBILE CALL GSM Alarm System GSM Alarm System System disarmed 11/26/2013 User s Manual Profile For a better understanding of this product, please read this user manual thoroughly before using it. CONTENTS
CARD ACCESS CONTROL SYSTEM
 SECTION 13851 CARD ACCESS CONTROL SYSTEM PART 1 GENERAL 1.01 SUMMARY A. Section Includes: A complete, operable, tested, integrated proximity access control system, to operate on a proximity principle where
SECTION 13851 CARD ACCESS CONTROL SYSTEM PART 1 GENERAL 1.01 SUMMARY A. Section Includes: A complete, operable, tested, integrated proximity access control system, to operate on a proximity principle where
BUYERS GUIDE PRODUCT & SERVICE CATEGORIES
 BUYERS GUIDE PRODUCT & SERVICE CATEGORIES BURGLAR ALARM EQUIPMENT ANNUNCIATORS, LIGHTS, AND SOUNDERS 10100 Annunciators 10150 Entry/Exit 10200 Graphic Displays 10250 Zone Displays 10300 Lights 10350 Emergency
BUYERS GUIDE PRODUCT & SERVICE CATEGORIES BURGLAR ALARM EQUIPMENT ANNUNCIATORS, LIGHTS, AND SOUNDERS 10100 Annunciators 10150 Entry/Exit 10200 Graphic Displays 10250 Zone Displays 10300 Lights 10350 Emergency
CM-RQE70A PIR REQUEST TO EXIT DETECTOR
 Door Activation Devices CM-RQE70A PIR REQUEST TO EXIT DETECTOR THIS PACKAGE INCLUDES (2) #6 x 3/4" Screws (2) 3/16" Wall Plugs (2) MOV's BP7175 1. GENERAL DESCRIPTION Camden CM-RQE70A Request-to-Exit Sensor
Door Activation Devices CM-RQE70A PIR REQUEST TO EXIT DETECTOR THIS PACKAGE INCLUDES (2) #6 x 3/4" Screws (2) 3/16" Wall Plugs (2) MOV's BP7175 1. GENERAL DESCRIPTION Camden CM-RQE70A Request-to-Exit Sensor
USER GUIDE WIRE-FREE HOME PROTECTION SYSTEM AG100+ CONTENTS
 CONTENTS USER GUIDE WIRE-FREE HOME PROTECTION SYSTEM AG00 Section Getting started. General system overview. Introduction to the system. Items included with the system. Introduction to the Smart Panel.5
CONTENTS USER GUIDE WIRE-FREE HOME PROTECTION SYSTEM AG00 Section Getting started. General system overview. Introduction to the system. Items included with the system. Introduction to the Smart Panel.5
Description Supervised Wireless Technology PRODUCT SPECIFICATION SHEET
 PRODUCT SPECIFICATION SHEET Made by RSI VIDEO TECHNOLOGIES 2200-XLSP February 2012 Description is a Videofied wireless, battery operated security system. The control panel is designed for residential and
PRODUCT SPECIFICATION SHEET Made by RSI VIDEO TECHNOLOGIES 2200-XLSP February 2012 Description is a Videofied wireless, battery operated security system. The control panel is designed for residential and
CODE ALERT Enterprise Software User Guide
 CODE ALERT Enterprise Software User Guide 2018 RF Technologies, Inc. All specifications subject to change without notice. All Rights Reserved. No Part of this work may be reproduced or copied in any form
CODE ALERT Enterprise Software User Guide 2018 RF Technologies, Inc. All specifications subject to change without notice. All Rights Reserved. No Part of this work may be reproduced or copied in any form
Integrated Security Solutions
 Integrated Security Solutions Table of Contents Control Panels 4 Keypads 8 Communication Modules 16 I/O Expanders 20 Door Control 24 Home Automation 25 RF Receivers 26 3 Our integrated security solutions
Integrated Security Solutions Table of Contents Control Panels 4 Keypads 8 Communication Modules 16 I/O Expanders 20 Door Control 24 Home Automation 25 RF Receivers 26 3 Our integrated security solutions
Watchguard WGAP864 User Manual
 Watchguard WGAP864 User Manual v1.0 Issued September 2016 1 2 Table of Contents Glossary... 5 1. Introduction to your Watchguard WGAP864... 6 2. Before Operating your Alarm System... 6 3. Understanding
Watchguard WGAP864 User Manual v1.0 Issued September 2016 1 2 Table of Contents Glossary... 5 1. Introduction to your Watchguard WGAP864... 6 2. Before Operating your Alarm System... 6 3. Understanding
Challenger10 Users Manual
 Challenger10 Users Manual P/N MAUSER-TS1016 REV 01 ISS 18FEB13 Copyright Trademarks and patents Manufacturer Agency compliance Contact information 2013 UTC Fire & Security. All rights reserved. The Challenger
Challenger10 Users Manual P/N MAUSER-TS1016 REV 01 ISS 18FEB13 Copyright Trademarks and patents Manufacturer Agency compliance Contact information 2013 UTC Fire & Security. All rights reserved. The Challenger
TD flex is an award-winning tailgate detection solution that prevents unauthorized access at: Doors Mantraps Airlocks E-gates Turnstiles
 Tailgate Detector TD TDflex is an award-winning tailgate detection solution that prevents unauthorized access at: Doors Mantraps Airlocks E-gates Turnstiles Access points without doors Tailgate Detector
Tailgate Detector TD TDflex is an award-winning tailgate detection solution that prevents unauthorized access at: Doors Mantraps Airlocks E-gates Turnstiles Access points without doors Tailgate Detector
DATA CENTER SECURITY. March 2017 Anton Panaitescu
 DATA CENTER SECURITY March 2017 Anton Panaitescu a-panaitescu@optex.com.pl +40 742 02 02 09 Activities Company Overview Business Domain Creation of a safer, more secure and more comfortable society. Security
DATA CENTER SECURITY March 2017 Anton Panaitescu a-panaitescu@optex.com.pl +40 742 02 02 09 Activities Company Overview Business Domain Creation of a safer, more secure and more comfortable society. Security
Wireless Devices. This chapter introduces the suite of DSC wireless sensors and devices used with the Impassa and other series of DSC alarm systems
 Wireless Devices This chapter introduces the suite of DSC wireless sensors and devices used with the Impassa and other series of DSC alarm systems ALARM DETECTORS WS4945 DOOR/WINDOW SENSOR The WS4945 is
Wireless Devices This chapter introduces the suite of DSC wireless sensors and devices used with the Impassa and other series of DSC alarm systems ALARM DETECTORS WS4945 DOOR/WINDOW SENSOR The WS4945 is
Physical and Environmental Security. CISSP Guide to Security Essentials Chapter 8
 Physical and Environmental Security CISSP Guide to Security Essentials Chapter 8 Objectives Site access controls including key card access systems, biometrics, video surveillance, fences and walls, notices,
Physical and Environmental Security CISSP Guide to Security Essentials Chapter 8 Objectives Site access controls including key card access systems, biometrics, video surveillance, fences and walls, notices,
DS160/DS161 Request To Exit PIR sensors Installation Instructions
 DS160/DS161 Request To Exit PIR sensors Installation Instructions 1.0 Description The DS160 is a Passive Infrared Detector (PIR) which is UL Listed as an Access Control Device under the UL 294 Standard.
DS160/DS161 Request To Exit PIR sensors Installation Instructions 1.0 Description The DS160 is a Passive Infrared Detector (PIR) which is UL Listed as an Access Control Device under the UL 294 Standard.
D3D Wi-Fi GSM Smart Alarm System -User Manual
 D3D Wi-Fi GSM Smart Alarm System -User Manual D3D Wi-Fi / GSM Smart Alarm system (Model : D10). Please read all instructions carefully & follow steps for easy home installation. 1 P a g e D3D Wi-Fi / GSM
D3D Wi-Fi GSM Smart Alarm System -User Manual D3D Wi-Fi / GSM Smart Alarm system (Model : D10). Please read all instructions carefully & follow steps for easy home installation. 1 P a g e D3D Wi-Fi / GSM
Security System. User s Guide for the Text Command Center
 User s Guide for the Text Command Center MY ALARM COMPANY IS: CALL BEFORE TEST: THIS SECURITY SYSTEM IS CONNECTED TO TELEPHONE NUMBER: THE SECURITY CONTROL PANEL IS CONNECTED TO THE PHONE JACK LOCATED:
User s Guide for the Text Command Center MY ALARM COMPANY IS: CALL BEFORE TEST: THIS SECURITY SYSTEM IS CONNECTED TO TELEPHONE NUMBER: THE SECURITY CONTROL PANEL IS CONNECTED TO THE PHONE JACK LOCATED:
Table of Contents. Appendix A Special Characters 31
 Table of Contents Introduction 2 Section 1: General System Operation 3 1.1 Getting to Know Your System... 3 1.2 How to Arm... 4 1.3 Alternate Arming Methods... 5 1.4 Disarming... 6 1.5 Alarm Memory...
Table of Contents Introduction 2 Section 1: General System Operation 3 1.1 Getting to Know Your System... 3 1.2 How to Arm... 4 1.3 Alternate Arming Methods... 5 1.4 Disarming... 6 1.5 Alarm Memory...
Case Studies. Redscan Laser Detector
 Case Studies Art Gallery Optex protects expensive art pieces with Redscan laser sensors that detect hand/arms Major Art Gallery s Protect valuable paintings from being touched In an indoor environment,
Case Studies Art Gallery Optex protects expensive art pieces with Redscan laser sensors that detect hand/arms Major Art Gallery s Protect valuable paintings from being touched In an indoor environment,
UBC Technical Guidelines Section Edition Access Control Page 1 of 5
 Page 1 of 5 1.0 GENERAL 1.1 Related UBC Guidelines.1 Section 28 05 00 Access Services: General Standards.2 Section 08 71 00 Door Hardware 1.2 Coordination Requirements.1 UBC Access Services 1.3 Description.1
Page 1 of 5 1.0 GENERAL 1.1 Related UBC Guidelines.1 Section 28 05 00 Access Services: General Standards.2 Section 08 71 00 Door Hardware 1.2 Coordination Requirements.1 UBC Access Services 1.3 Description.1
RUNNER 8/64. 8/64 Zones Control Panel. Program Summary Guide
 RUNNER 8/64 8/64 Zones Control Panel Program Summary Guide SOFTWARE VERSION This manual relates to RUNNER 864 control panels with software version V10.0.115 and above Special Programming Operating Procedures
RUNNER 8/64 8/64 Zones Control Panel Program Summary Guide SOFTWARE VERSION This manual relates to RUNNER 864 control panels with software version V10.0.115 and above Special Programming Operating Procedures
SA 2650 Kit User Manual
 SA 2650 Kit User Manual Table of Contents 1. System Installation Planning 1 2. Device Introduction 3 3. Getting Started 6 4. System Default Setting 10 5. Connect2Home Application 11 6. System Information
SA 2650 Kit User Manual Table of Contents 1. System Installation Planning 1 2. Device Introduction 3 3. Getting Started 6 4. System Default Setting 10 5. Connect2Home Application 11 6. System Information
CONSULTANT PROCEDURES & DESIGN GUIDELINES ACCESS CONTROL SYSTEM
 GENERAL: To provide minimum standards for Access Control Systems. PART 1 Common Work Results for Access Control System 1.1 Owner will provide server and software for connecting control panels through the
GENERAL: To provide minimum standards for Access Control Systems. PART 1 Common Work Results for Access Control System 1.1 Owner will provide server and software for connecting control panels through the
Preface. Thank you for purchasing our GSM Security Alarm System ( The System )! The System will keep your home and property safe around the clock.
 Preface Thank you for purchasing our GSM Security Alarm System ( The System )! The System will keep your home and property safe around the clock. The GSM Security Alarm ( The Alarm ) adopts the most advanced
Preface Thank you for purchasing our GSM Security Alarm System ( The System )! The System will keep your home and property safe around the clock. The GSM Security Alarm ( The Alarm ) adopts the most advanced
Code Alert Series 30 Software User Guide
 Code Alert Series 30 Software User Guide 2018 RF Technologies, Inc. All specifications subject to change without notice. All Rights Reserved. No Part of this work may be reproduced or copied in any form
Code Alert Series 30 Software User Guide 2018 RF Technologies, Inc. All specifications subject to change without notice. All Rights Reserved. No Part of this work may be reproduced or copied in any form
Solution 880 Operators Manual. Issue 1.00
 Solution 880 Operators Manual Issue 1.00 Solution 880 Operators Manual Copyright 1998 by, SYDNEY, AUSTRALIA Document Part Number MA408O Document ISSUE 1.00 Printed 15 June 1998 This documentation is provided
Solution 880 Operators Manual Issue 1.00 Solution 880 Operators Manual Copyright 1998 by, SYDNEY, AUSTRALIA Document Part Number MA408O Document ISSUE 1.00 Printed 15 June 1998 This documentation is provided
Controllers. Centralization of Access Control Devices Made Easy. Installer Guide
 Controllers Centralization of Access Control Devices Made Easy Installer Guide CONTENTS 1 INTRODUCTION 3 The Overview of Hardware 5 The Overview of Installation & Communications 7 Installations with door
Controllers Centralization of Access Control Devices Made Easy Installer Guide CONTENTS 1 INTRODUCTION 3 The Overview of Hardware 5 The Overview of Installation & Communications 7 Installations with door
